Hier nog een mooi filmpje hoe Palantir (met dus de NSA/CIA database) iedereen zijn informatie makkelijk kan controleren;quote:Op vrijdag 7 juni 2013 23:56 schreef epicbeardman het volgende:
Grappig youtube filmpje van Palantir, het bedrijf waar CIA vermoedelijk met werkt.
[..]
Dit doen ze dus ongeveer, maar dan op massive scale;
http://www.businessinside(...)ed-by-the-cia-2013-6
PRISM Is Also The Name Of A Product From Palantir, A $5 Billion Tech Startup Funded By The CIA
Dat filmpje is 3dagen geleden geupload door Palantir.
Als iemand dit kijkt, zie je toch wel hoe eng dit eigenlijk is.
Natuurlijk is het ook weer een Arabische naam die ze moeten "investigaten"
Iemand die haat heeft tegen Elon Musk gunt succesvolle Afrikanen het licht niet in de ogen en is een racist bigot.


9/11 is een inside job. Een van de redenen voor de aanslag was het op grote schaal verzamelen van gegevens van burgers.
[ Bericht 1% gewijzigd door polderturk op 08-06-2013 15:38:50 ]
[ Bericht 1% gewijzigd door polderturk op 08-06-2013 15:38:50 ]


quote:Op zaterdag 8 juni 2013 14:18 schreef polderturk het volgende:
9/11 is een inside job. Een van de redenen voor de aanslag os het op grote schaal verzamelen van gegevens van burgers.
In Baden-Badener Badeseen kann man Baden-Badener baden sehen.


Toepasselijke naam ook, Palantir.quote:Op zaterdag 8 juni 2013 12:52 schreef epicbeardman het volgende:
[..]
Hier nog een mooi filmpje hoe Palantir (met dus de NSA/CIA database) iedereen zijn informatie makkelijk kan controleren;
Als iemand dit kijkt, zie je toch wel hoe eng dit eigenlijk is.
Natuurlijk is het ook weer een Arabische naam die ze moeten "investigaten"


http://rationalwiki.org/wiki/9/11_conspiracy_theoriesquote:Op zaterdag 8 juni 2013 14:18 schreef polderturk het volgende:
9/11 is een inside job. Een van de redenen voor de aanslag os het op grote schaal verzamelen van gegevens van burgers.


Weet je, het ergste aan dit hele gezeik dat er nu nog meer volksstammen dit soort onzin gaan geloven.quote:Op zaterdag 8 juni 2013 14:18 schreef polderturk het volgende:
9/11 is een inside job. Een van de redenen voor de aanslag was het op grote schaal verzamelen van gegevens van burgers.
Ik ben vooral benieuwd hoe dit allemaal gelekt is.
And if you listen very hard
The tune will come to you at last
When all are one and one is all
To be a rock and not to roll
The tune will come to you at last
When all are one and one is all
To be a rock and not to roll


De ergste uitkomst van dat hele volksstammen het inside job verhaal gaan geloven is dat de overheid eindelijk eens gedwongen word op te rotten met hun inlichtingendiensten en oorlogen. De uitkomst van het huidige verhaal dat terroristen onder iedere steen zitten heeft letterlijk tot meer dan een miljoen doden geleid, het verdwijnen van een hele hoop rechten en privacy, het faillissement van de Amerikaanse overheid en permanente haat vanuit moslim landen richting ons.quote:Op zaterdag 8 juni 2013 16:53 schreef Fir3fly het volgende:
[..]
Weet je, het ergste aan dit hele gezeik dat er nu nog meer volksstammen dit soort onzin gaan geloven.
Ik ben vooral benieuwd hoe dit allemaal gelekt is.


Dat lijkt mij ook. Hopelijk leidt het tot een herziening van de huidige politieke koers in de VS op tal van terreinen.quote:Op zaterdag 8 juni 2013 19:06 schreef Brum_brum het volgende:
[..]
De ergste uitkomst van dat hele volksstammen het inside job verhaal gaan geloven is dat de overheid eindelijk eens gedwongen word op te rotten met hun inlichtingendiensten en oorlogen. De uitkomst van het huidige verhaal dat terroristen onder iedere steen zitten heeft letterlijk tot meer dan een miljoen doden geleid, het verdwijnen van een hele hoop rechten en privacy, het faillissement van de Amerikaanse overheid en permanente haat vanuit moslim landen richting ons.
The view from nowhere.


Dat maakt het nog niet waar maar in een wereld waarin we over de grote gebeurtenissen toch nooit de hele waarheid horen kunnen we maar beter een versie hebben die geen oorlog veroorzaakt.quote:Op zaterdag 8 juni 2013 20:04 schreef deelnemer het volgende:
[..]
Dat lijkt mij ook. Hopelijk leidt het tot een herziening van de huidige politieke koers in de VS op tal van terreinen.


quote:Op zaterdag 8 juni 2013 20:25 schreef Brum_brum het volgende:
[..]
Dat maakt het nog niet waar maar in een wereld waarin we over de grote gebeurtenissen toch nooit de hele waarheid horen kunnen we maar beter een versie hebben die geen oorlog veroorzaakt.
The view from nowhere.


Misschien gewoon het feit alleen al dat de overheid dat ziet en ik dat beangstigend vind? Ik heb niks te verbergen maar dat betekent niet dat ik wil dat iedereen alles over me weetquote:Op zaterdag 8 juni 2013 02:31 schreef Daftastic het volgende:
Je moet wel ontzettend naïef / technofoob als je denkt dat dit niet gebeurde.
Mensen doen veel te zwaar over privacy. Het is niet zo dat de Amerikaanse overheid al je chatsessies gaan doorlezen, je moet wel erg verdacht internet- en surfgedrag hebben voordat ze ook maar de moeite nemen (en ook al zouden ze je gesprekken doorlezen met vrienden, wat dan nog als je niks te verbergen hebt?)...*
Ik denk dat veel mensen zich zullen verbazen als ze weten waardoor ze allemaal 'bespioneerd' worden, zoals smartphone apps, de Albert Heijn bonuskaart en de KvK die al je gegevens opslaan, gebruiken en soms doorverkopen.
* Ik heb het nu puur over de Amerikaanse overheid.


Simpel, gewoon wegblijven van het internet.quote:Op zondag 9 juni 2013 02:36 schreef Romanus het volgende:
[..]
Misschien gewoon het feit alleen al dat de overheid dat ziet en ik dat beangstigend vind? Ik heb niks te verbergen maar dat betekent niet dat ik wil dat iedereen alles over me weet
And if you listen very hard
The tune will come to you at last
When all are one and one is all
To be a rock and not to roll
The tune will come to you at last
When all are one and one is all
To be a rock and not to roll


Wegblijven van het internet is niet genoeg. Ze kunnen altijd je telefoon, elektriciteitsrekening, bankrekening en post nog controleren.quote:Op zondag 9 juni 2013 03:08 schreef Fir3fly het volgende:
[..]
Simpel, gewoon wegblijven van het internet.
Op zaterdag 8 februari 2014 23:39 schreef Slaapscheet het volgende:
Oke, MichaelScott, je bent geweldig. :D
Oke, MichaelScott, je bent geweldig. :D


quote:Boundless Informant: the NSA's secret tool to track global surveillance data | World news | guardian.co.uk
Revealed: The NSA's powerful tool for cataloguing data – including figures on US collection
The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications.
The Guardian has acquired top-secret documents about the NSA datamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks.
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.
The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, "What type of coverage do we have on country X" in "near real-time by asking the SIGINT [signals intelligence] infrastructure."
An NSA factsheet about the program, acquired by the Guardian, says: "The tool allows users to select a country on a map and view the metadata volume and select details about the collections against that country."
Under the heading "Sample use cases", the factsheet also states the tool shows information including: "How many records (and what type) are collected against a particular country."
A snapshot of the Boundless Informant data, contained in a top secret NSA "global heat map" seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.
Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. Jordan, one of America's closest Arab allies, came third with 12.7bn, Egypt fourth with 7.6bn and India fifth with 6.3bn.
The heatmap gives each nation a color code based on how extensively it is subjected to NSA surveillance. The color scheme ranges from green (least subjected to surveillance) through yellow and orange to red (most surveillance).
The disclosure of the internal Boundless Informant system comes amid a struggle between the NSA and its overseers in the Senate over whether it can track the intelligence it collects on American communications. The NSA's position is that it is not technologically feasible to do so.
At a hearing of the Senate intelligence committee In March this year, Democratic senator Ron Wyden asked James Clapper, the director of national intelligence: "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?"
"No sir," replied Clapper.
Judith Emmel, an NSA spokeswoman, told the Guardian in a response to the latest disclosures: "NSA has consistently reported – including to Congress – that we do not have the ability to determine with certainty the identity or location of all communicants within a given communication. That remains the case."
Other documents seen by the Guardian further demonstrate that the NSA does in fact break down its surveillance intercepts which could allow the agency to determine how many of them are from the US. The level of detail includes individual IP addresses.
IP address is not a perfect proxy for someone's physical location but it is rather close, said Chris Soghoian, the principal technologist with the Speech Privacy and Technology Project of the American Civil Liberties Union. "If you don't take steps to hide it, the IP address provided by your internet provider will certainly tell you what country, state and, typically, city you are in," Soghoian said.
That approximation has implications for the ongoing oversight battle between the intelligence agencies and Congress.
On Friday, in his first public response to the Guardian's disclosures this week on NSA surveillance, Barack Obama said that that congressional oversight was the American peoples' best guarantee that they were not being spied on.
"These are the folks you all vote for as your representatives in Congress and they are being fully briefed on these programs," he said. Obama also insisted that any surveillance was "very narrowly circumscribed".
Senators have expressed their frustration at the NSA's refusal to supply statistics. In a letter to NSA director General Keith Alexander in October last year, senator Wyden and his Democratic colleague on the Senate intelligence committee, Mark Udall, noted that "the intelligence community has stated repeatedly that it is not possible to provide even a rough estimate of how many American communications have been collected under the Fisa Amendments Act, and has even declined to estimate the scale of this collection."
At a congressional hearing in March last year, Alexander denied point-blank that the agency had the figures on how many Americans had their electronic communications collected or reviewed. Asked if he had the capability to get them, Alexander said: "No. No. We do not have the technical insights in the United States." He added that "nor do we do have the equipment in the United States to actually collect that kind of information".
Soon after, the NSA, through the inspector general of the overall US intelligence community, told the senators that making such a determination would jeopardize US intelligence operations – and might itself violate Americans' privacy.
"All that senator Udall and I are asking for is a ballpark estimate of how many Americans have been monitored under this law, and it is disappointing that the inspectors general cannot provide it," Wyden told Wired magazine at the time.
The documents show that the team responsible for Boundless Informant assured its bosses that the tool is on track for upgrades.
The team will "accept user requests for additional functionality or enhancements," according to the FAQ acquired by the Guardian. "Users are also allowed to vote on which functionality or enhancements are most important to them (as well as add comments). The BOUNDLESSINFORMANT team will periodically review all requests and triage according to level of effort (Easy, Medium, Hard) and mission impact (High, Medium, Low)."
Emmel, the NSA spokeswoman, told the Guardian: "Current technology simply does not permit us to positively identify all of the persons or locations associated with a given communication (for example, it may be possible to say with certainty that a communication traversed a particular path within the internet. It is harder to know the ultimate source or destination, or more particularly the identity of the person represented by the TO:, FROM: or CC: field of an e-mail address or the abstraction of an IP address).
"Thus, we apply rigorous training and technological advancements to combine both our automated and manual (human) processes to characterize communications – ensuring protection of the privacy rights of the American people. This is not just our judgment, but that of the relevant inspectors general, who have also reported this."
She added: "The continued publication of these allegations about highly classified issues, and other information taken out of context, makes it impossible to conduct a reasonable discussion on the merits of these programs."
Bron: www.guardian.co.uk
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Geweldig boek ook.quote:Op donderdag 26 juli 2012 09:57 schreef wise het volgende:
duidelijk 1984 ja.
Grappig hoe zo'n "oud" boek zoveel waarheden bevat.


Proxy gaan gebruiken.quote:Op zondag 9 juni 2013 02:36 schreef Romanus het volgende:
[..]
Misschien gewoon het feit alleen al dat de overheid dat ziet en ik dat beangstigend vind? Ik heb niks te verbergen maar dat betekent niet dat ik wil dat iedereen alles over me weet


Daar had de NSA natuurlijk geen rekening mee gehoudenquote:
In Baden-Badener Badeseen kann man Baden-Badener baden sehen.


Leuk he trouwens die "vind ik leuk" knop op alle websites. De tracking cookie van facebook weet precies welke websites jij bezoekt.
Wie dit leest is een lezer van dit.


Ik blijf het trouwens grappig vinden dat de opwinding gaat over dat de NSA VS burgers nagaat. Dat is formeel illigaal, de NSA mag juridisch in het binnenland niet actief zijn. Maar dat is voor ons geheel niet interessant.
Dat de NSA achterom in de servers van allerlei IT leveranciers komt is veel belangrijker. De NSA heeft in het verleden gegevens van Europese bedrijven doorgespeeld aan Amerikaanse om die daarmee een concurrentievoordeel te geven. Dit betekend dus dat je als niet amerikaans bedrijf met interessante technologie er voor moet kiezen geen amerikaanse it diensten af te nemen.
Het zoekgedrag van technologie ontwikkelaars zegt bv veel over waar men onderzoek naar doet.
Ditzelfde geld voor patentonderzoek.
Dat de NSA achterom in de servers van allerlei IT leveranciers komt is veel belangrijker. De NSA heeft in het verleden gegevens van Europese bedrijven doorgespeeld aan Amerikaanse om die daarmee een concurrentievoordeel te geven. Dit betekend dus dat je als niet amerikaans bedrijf met interessante technologie er voor moet kiezen geen amerikaanse it diensten af te nemen.
Het zoekgedrag van technologie ontwikkelaars zegt bv veel over waar men onderzoek naar doet.
Ditzelfde geld voor patentonderzoek.
In Baden-Badener Badeseen kann man Baden-Badener baden sehen.


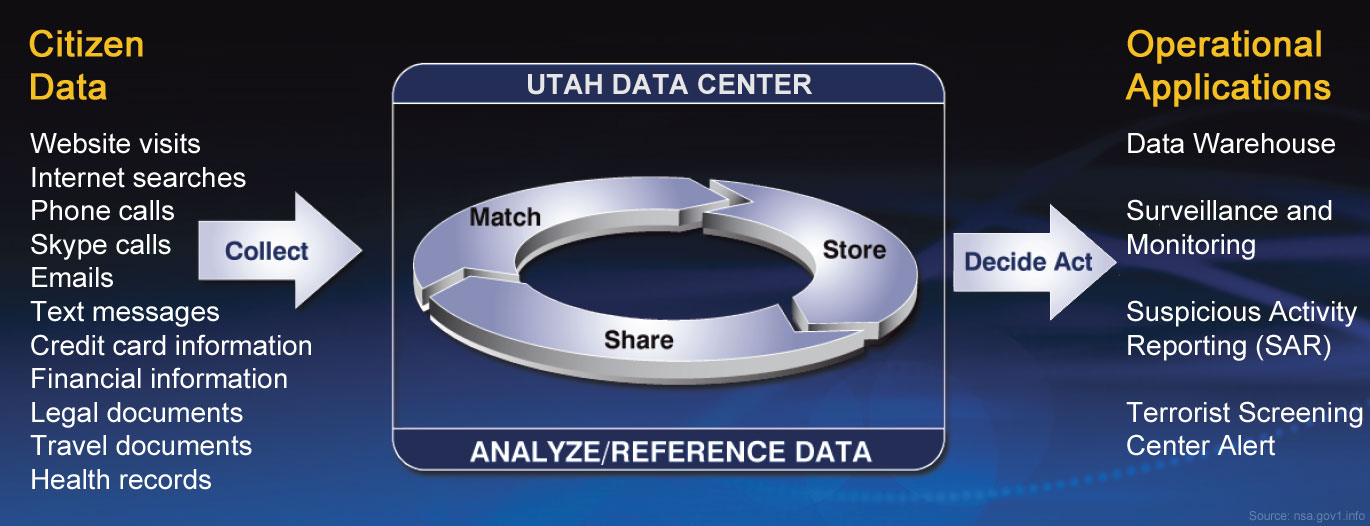
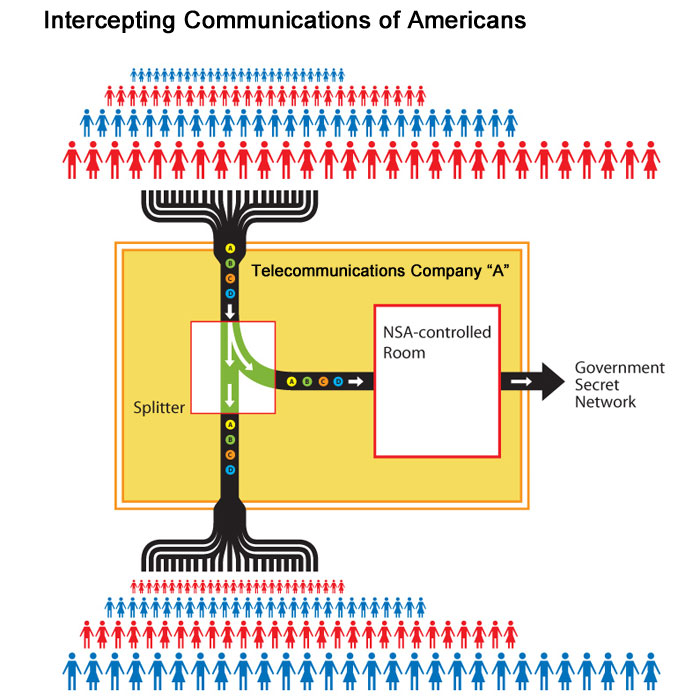
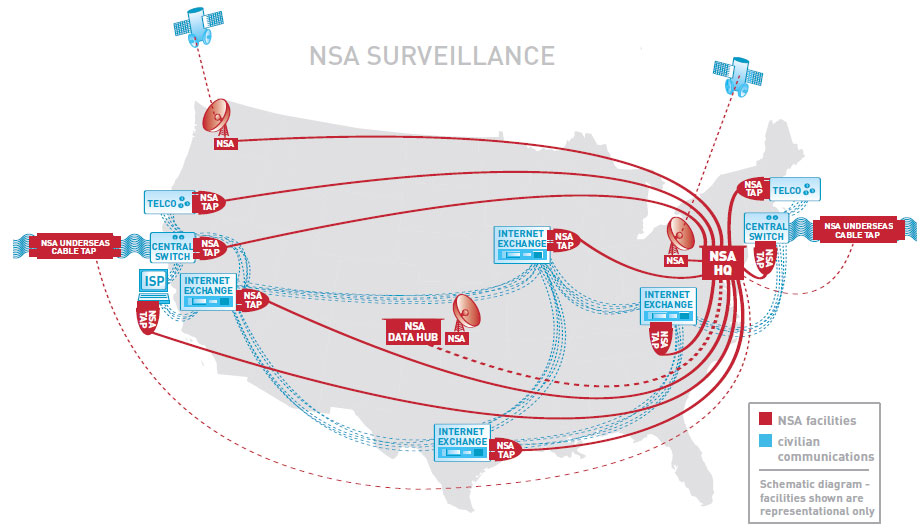
Leuke plaatjes van de NSA:
Zo geheim zijn ze niet over wat ze doen

Zo geheim zijn ze niet over wat ze doen
Waar is mn alufoliehoedje?quote:Your Data: If You Have Nothing to Hide, You Have Nothing to Fear
Our value is founded on a unique and deep understanding of risks, vulnerabilities, mitigations, and threats. Domestic Surveillance plays a vital role in our national security by maintaining a total information awareness of all domestic activities by using advanced data mining systems to "connect the dots" to identify suspicious patterns.
Why We Collect Your Data
Under the authority of Homeland Security Presidential Directive 6, which defines the integration and use of screening information to protect against terrorism, the NSA is authorized to collect and disseminate information about suspected foreign and domestic terrorists. In the past, this meant gathering information AFTER a target had been identified. This often led to missed intelligence and lost opportunities.
But what if we could collect the information in advance, before the target was known? What if the mere act of collecting information could result in the identification of new targets? What if we could build a national data warehouse containing all available information about every person in the United States? Under the authority of the classified Homeland Security Directive 15 (U.S. Strategy and Policy in the War on Terror), we can.
What Data We Collect
Every day, people leave a digital trail of electronic breadcrumbs as they go about their daily routine. They go to work using electronic fare cards; drive through intersections with traffic cameras; walk down the street past security cameras; surf the internet; pay for purchases with credit/debit cards; text or call their friends; and on and on.
There is no way to predict in advance which crucial piece of data will be the key to revealing a potential plot. The standard operating procedure for the Domestic Surveillance Directorate is to "collect all available information from all available sources all the time, every time, always".
For security reasons, it is unrealistic to expect a complete list of information we collect for our national citizen database. In the spirit of openness and transparency however, here is a partial list:
internet searches
websites visited
emails sent and received
social media activity (Facebook, Twitter, etc)
blogging activity including posts read, written, and commented on - View our patent
videos watched and/or uploaded online
photos viewed and/or uploaded online
music downloads
mobile phone GPS-location data
mobile phone apps downloaded
phone call records - View our patent
text messages sent and received
online purchases and auction transactions
bookstore receipts
credit card/ debit card transactions
bank statements
cable television shows watched and recorded
commuter toll records
parking receipts
electronic bus and subway passes / Smartpasses
travel itineraries
border crossings
surveillance cameras
medical information including diagnoses and treatments
prescription drug purchases
guns and ammunition sales
educational records
arrest records
driver license information
How We Collect Your Data
For information on how we collect your data, including our PRISM program, visit Our Surveillance Strategy page on this website. For information about our new state-of-the-art Surveillance Data Center, visit our Utah Data Center information page.
How We Use Your Data
We treasure the U.S. Constitution and the rights it secures for all the people. In a world in which privacy has become illusory in so many areas of our lives, the Domestic Surveillance Directorate maintains the highest standards of integrity and lawful action. Your private data is safely secured using our custom database software called Cloudbase, which has fine-grained security to control access down to the cell level.
Threat Matrix Processing
Incoming transactional data is analyzed against a continually evolving threat matrix and is assigned an action code. The vast majority of these transactions are routed directly to a permanent static storage state. In fact, for most Americans, your data is never accessed or viewed by anyone within the US Government unless some future event triggers an inquiry. We work closely with our partners in the Intelligence Community to ensure that your stored data is released only as a result of a "national security" request.
Continuity of Government
Our strong commitment to keeping the Nation safe includes an important role in maintaining the Continuity of Government. Since the early 1980s, the federal government has used its secret Main Core database to track dissidents and watchlisted Americans in the event of a national emergency. The roots of the Domestic Surveillance Directorate can, in fact, be traced back to the early days of this program. We are proud to continue this tradition by sharing our data with the modern-day COG program. Learn more about this.
Future Uses of Domestic Intelligence Data
In 2006, the Intelligence Advanced Research Projects Activity (IARPA) was created to invest in high-risk, high-payoff classified programs uniquely designed to provide research and technical capabilities for the Intelligence Community. IARPA-funded researchers are currently studying novel ways of processing and analyzing the explosive growth of domestic data.
The Aladdin program seeks to extract intelligence information from the high volume of videos uploaded to the internet.
The Babel program is developing agile and robust speech recognition technology that can provide effective search capability for analysts to efficiently process massive amounts of real-world recorded speech.
The Knowledge Discovery and Dissemination (KDD) program will develop advanced analytic algorithms that can effectively draw inferences across multiple databases to allow the Intelligence Community to create virtual fusion centers enabling analysts to produce actionable intelligence.
The Socio-cultural Content in Language (SCIL) Program will develop novel algorithms, techniques and technologies to uncover the social actions and characteristics of members of a group (ie; within discussion forums, online comment sections, social media, etc.) by examining the language used in relation to acceptable social and cultural norms.
The Reynard Program starts from the premise that "real world" characteristics are reflected in "virtual world" behavior. The program seeks to identify behavioral indicators in online virtual worlds and "massively multiplayer online games" that are related to the real world characteristics of the users. Attributes of interest include gender, age, economic status, educational level, occupation, ideology or "world view", and physical geographic location.
http://nsa.gov1.info/data/index.html
Are we not savages, innately destined to maim and kill?
Blame it on the environment, heredity or evolution: we're still responsible
Our intelligence may progress at geometric rates
Yet socially we remain belligerent neonates
Blame it on the environment, heredity or evolution: we're still responsible
Our intelligence may progress at geometric rates
Yet socially we remain belligerent neonates


Die is er niet!!quote:Op zondag 9 juni 2013 10:35 schreef YuckFou het volgende:
Leuke plaatjes van de NSA:
[ afbeelding ]
Zo geheim zijn ze niet over wat ze doen
[ afbeelding ]
[ afbeelding ]
[ afbeelding ]
[ afbeelding ]
[..]
Waar is mn alufoliehoedje?


Leuk dat ze het "if you have nothing to hide, you have nothing to fear", ook nog even zelf herhalen 
Jammer alleen dat ze niet zeggen naar waar ze op zoek zijn. Oh je hebt SP gestemd? Hmm kans dat je een linkse-extremist bent. Oh je hebt daarnaast wikileaks gesteund met een paar dollar? Nu is de kans wel erg groot dat je Amerika haat. Misschien is het beter als vliegvelden je gewoon helemaal weigeren.
Trouwens, echt HULDE aan The Guardian dat ze zo doorgaan met het publiceren van die gelekte documenten.
Jammer alleen dat ze niet zeggen naar waar ze op zoek zijn. Oh je hebt SP gestemd? Hmm kans dat je een linkse-extremist bent. Oh je hebt daarnaast wikileaks gesteund met een paar dollar? Nu is de kans wel erg groot dat je Amerika haat. Misschien is het beter als vliegvelden je gewoon helemaal weigeren.
Trouwens, echt HULDE aan The Guardian dat ze zo doorgaan met het publiceren van die gelekte documenten.
Opgeblazen gevoel of winderigheid? Zo opgelost met Rennie!


Ik heb genoeg to hide, het gaat de overheid niets aan met wie ik neuk, een biertje drink of een overleg heb. Slechts als er gerede verdenking is dat er criminele activiteiten zijn hoort een rechter te oordelen of er reden is om te tappen.
Wat men doet is iedereen en alles monitoren om dan met big data tooling analyses te maken.
Dit zijn tools waar de stasi slechts van kon dromen, nee, zelfs in hun dromen kon de stasi zich zulke controle niet voorstellen.
Is dat erg? Ja, dat is natuurlijk erg want hier zal gebruik/misbruik van worden gemaakt. Dat de politiek dit soort mogelijkheden gebruikt weten we al sinds Nixon, sinds het Boeing/Airbus/Echelon gebeuren.
Het gaat niet alleen om terrorisme, maar om industriespionage, om lekken naar de pers op te sporen, om de pers af te luisteren. Dit gebeurd net zo hard in Nederland waar de inlichtingendiensten de pers afluisterde om de lekkers van de misstanden op te sporen. Een overheid die doelbewust haar eigen regels overtreed om haar falen te maskeren.
Wat men doet is iedereen en alles monitoren om dan met big data tooling analyses te maken.
Dit zijn tools waar de stasi slechts van kon dromen, nee, zelfs in hun dromen kon de stasi zich zulke controle niet voorstellen.
Is dat erg? Ja, dat is natuurlijk erg want hier zal gebruik/misbruik van worden gemaakt. Dat de politiek dit soort mogelijkheden gebruikt weten we al sinds Nixon, sinds het Boeing/Airbus/Echelon gebeuren.
Het gaat niet alleen om terrorisme, maar om industriespionage, om lekken naar de pers op te sporen, om de pers af te luisteren. Dit gebeurd net zo hard in Nederland waar de inlichtingendiensten de pers afluisterde om de lekkers van de misstanden op te sporen. Een overheid die doelbewust haar eigen regels overtreed om haar falen te maskeren.
In Baden-Badener Badeseen kann man Baden-Badener baden sehen.


Zoals de waard is vertrouwd hij zijn gasten....quote:Op zondag 9 juni 2013 12:10 schreef Pietverdriet het volgende:
Een overheid die doelbewust haar eigen regels overtreed om haar falen te maskeren.
Are we not savages, innately destined to maim and kill?
Blame it on the environment, heredity or evolution: we're still responsible
Our intelligence may progress at geometric rates
Yet socially we remain belligerent neonates
Blame it on the environment, heredity or evolution: we're still responsible
Our intelligence may progress at geometric rates
Yet socially we remain belligerent neonates