

Anon: Wordt gebruikt als aanduiding van zowel de totale internet-community als voor netizens die zich identificeren met Anonymous.
Anonymous: Ongeorganiseerd hacktivist collectief.
Anonops: Een netwerk/infrastructuur dat door Anonymous gebruikt word om actie te voeren.
Peoples Liberation Front: Cyber millitia. Volgens CommanderX gevormd in 1985 met behulp van LSD. Werkt samen met Anonops als dat zo uitkomt.
http://www.itworld.com/in(...)mmander-x?page=0%2C0
Lulzsec: Leakers. Ze "testen" met veel plezier beveiligingen op internet. Ge´nfiltreerd en opgerold door de FBI e.d.
Whatis-theplan.org Discussie-forum. Verander de wereld in 3 stappen. Ligt onder vuur door oldfag-trollen.
http://nl.wikipedia.org/wiki/4chan
4chan is een Engelstalig imageboard/internetforum. 4chan werd op 1 oktober 2003 opgericht door de toen 15-jarige "moot". Gebruikers kunnen volledig anoniem afbeeldingen en reacties plaatsen over alle denkbare onderwerpen. De site is gebaseerd op het Japanse internetforum Futaba Channel en is onderverdeeld in verschillende subfora, 'boards' genaamd. Het meest populaire (en beruchte) is het Random board, genaamd /b/. 4chan gebruikers zijn verantwoordelijk voor het bedenken of populariseren van vele zogeheten internetmemes.
Een bekende meme komt van een Japanse manga.
Als je denkt dat je geweldig bent of iets fantastisch hebt gedaan zeg je “I’m over 9000”
Oprah Winfrey weet het , na een berichtje van 4chan, nu ook:
Iedereen kan via 4chan, maar ook via de ouderwetse IRC-channels, volledig anoniem met elkaar “communiceren”. http://nl.wikipedia.org/wiki/Internet_Relay_Chat
4chan /b/ gaat over borsten, cracken/hacken van software en websites, down- en uploaden. De veelal jonge gebruikers van 4chan verveelden zich niet alleen met elkaar, maar hun kattenkwaad bereikte ook de echte wereld. Buren en leraren kregen ongevraagd pizza-bezorgers aan de deur of werden over de telefoon lastig gevallen nadat persoonlijke gegevens via 4chan werden verspreidt. Ook werden websites bestookt met commentaar of extreem veel bezoek. Bezoek dat na verloop van tijd werd geautomatiseerd met behulp van een test-tool voor websites, omgebouwd en omgedoopt tot Low Orbit Ion Cannon.
Binnen de Anon-community ontstond op een dag het hacktivisme. En het heette Anonymous. Anonymous belichaamde een belangrijk Anon-ideaal: Vrij, open, ongecensureerd internet, onbeperkte vrijheid van (het delen van) informatie. En Anonymous vond een vijand. Januari 2008.
Deze interne propaganda-video lekte uit en kwam uit via Gawker. Scientology staat er om bekend om auteurswetgeving te misbruiken om hun methoden uit de openbaarheid te houden. Scientology vroeg Gawker de video te verwijderen. De video bleef opduiken en nadat advocaten van Scientology wereldwijd websites terroriseerden kwam Anonymous met hun oorlogsverklaring.
Anonymous gebruikte het volledige 4chan arsenaal. DDOSsen van scientology-websites, e-mail/fax-bommen, prank-calls. Maar de acties breidden zich uit naar de echte wereld. Main-stream media pikten het op en demonstraties over de hele wereld vonden plaats.
Na maanden werd het wat rustiger tussen Anonymous en Scientology, maar Oparation Chanalogy loopt nog steeds.
De strijd voor een vrij en open internet bleef en richtte zich vooral op film- en platenmaatschappijen in Operation Payback. Anonymous verklaarde zich solidair met WikiLeaks toen Joe Liebermann financiŰle mogelijkheden van WikiLeaks probeerde af te sluiten, en startte Operation Avenge Assange waarbij ze de websites van Paypal, Mastercard en Visa aanvielen.
Kort daarna kwam de video voor Operation Payback uit.
3 januari 2011 opende Anonymous de aanval op websites van TunesiŰ, en Anonymous bemoeit zich tot op de dag van vandaag met de revoluties in het Midden Oosten. Niet alleen met DDOS-aanvallen, maar ook met informatie (naar demonstranten en naar het internationale publiek) praktische tips (EHBO, maak zelf een gasmasker) alternatieve communicatiemiddelen.
5 februari 2011: Ene Aaron Barr van HBGary Federal maakte in een interview bekend dat hij de leiders van Anonymous had ge´dentificeerd. Een groep hackers hackte de computers van HBGary, zette een boodschap op hun website, wiste een berg data en openbaarde 70.000 e-mails. Uit de e-mails bleek dat het Amerikaanse bedrijfsleven en de overheid alle legale en illegale middelen gebruikt om tegenstanders (mensenrechten organisaties, vakbonden en WikiLeaks) kapot te maken.
http://arstechnica.com/te(...)rr-met-anonymous.ars
Barret Brown stortte zich op de mails en heeft Project PM opgericht om de activiteiten van internetbeveiligingsbedrijven i.s.m. vooral de US overheid in kaart te brengen.
IRL-Troll familie Westboro Baptist Church dacht ook mee te kunnen liften en daagde Anonymous uit.twitter:BarrettBrownLOL twitterde op maandag 03-09-2012 om 02:16:10 And all this because man put in motion systems that returned to enslave him #ProjectPM reageer retweet
Waarna Th3 J3st3r de WBC-websites maandenlang plat legde.
NATO maakt zich zorgen:
Anonymous en Occupy Wall Str.:quote:http://www.thinq.co.uk/20(...)persecute-anonymous/
NATO leaders have been warned that WikiLeaks-loving 'hacktivist' collective Anonymous could pose a threat to member states' security, following recent attacks on the US Chamber of Commerce and defence contractor HBGary - and promise to 'persecute' its members.
quote:From a single hashtag, a protest circled the world
(Reuters) - It all started innocuously enough with a July 13 blog post urging people to #OccupyWallStreet, as though such a thing (Twitter hashtag and all) were possible.
NWS / Anonymous daagt Mexicaans drugskartel uit.
quote:Gabriella Coleman Assistant Professor of Media, Culture, and Communication
Trained as an anthropologist, Gabriella (Biella) Coleman examines the ethics of online collaboration/institutions as well as the role of the law and digital media in sustaining various forms of political activism. Between 2001-2003 she conducted ethnographic research on computer hackers primarily in San Francisco, the Netherlands, as well as those hackers who work on the largest free software project, Debian. Her first book, "Coding Freedom: The Aesthetics and the Ethics of Hacking" is forthcoming with Princeton University Press and she is currently working on a new book on Anonymous and digital activism. She is the recipient of numerous grants, fellowships, and awards, including ones from the National Science Foundation, the Woodrow Wilson Foundation, the Ford Foundation, the Social Science Research Council and the Institute for Advanced Study.
quote:
quote:Our Weirdness Is Free
The logic of Anonymous—online army, agent of chaos, and seeker of justice.
by Gabriella Coleman, [01.13.2012]
quote:
TIMELINE: The Evolution Of The 'Anonymous' Internet Hacktivist Groupquote:Anonymous And The War Over The Internet
This article is the first in a two-part series tracing the development of the amorphous online community known as Anonymous, pranksters who have become a force in global affairs.
The Huffington Post, Saki Knafo. Posted: 1/30/12 12:20 PM ET | Updated: 2/1/12 07:36 PM ET
Vorige delen:
NWS / Internet community begint oorlog tegen Scientology...
NWS / Internet community begint oorlog tegen Scientology #2
NWS / Internet community begint oorlog tegen Scientology #3
NWS / Anonops : Take down mastercard
NWS / Anonops : Take down Politie.nl
NWS / Anonops #3: Soldiers are enlisting.
NWS / Anonops #4: The war goes on
NWS / Anonops #5: Anonymous en de MO-revoluties
NWS / Anonops #6: Anonymous en de MO-revoluties
NWS / Anonops #7: Meer is beter
NWS / Anonops #8: Occupy Wall Str.
NWS / Anonops #9: Get Los(t) Zetas
NWS / Anonops #10: Stop SOPA
NWS / Anonops #11: Stop ACTA
NWS / Anonops #12: Spy on the Spyers
NWS / Anonops #13: Stop CISPA
NWS / Anonops #14: All about control
NWS / Anonops #15: Last or not to Last
[ Bericht 0% gewijzigd door Papierversnipperaar op 12-04-2014 16:01:13 ]
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Voor Edward Snowden en de NSA is een apart topic: NWS / Monitoring NSA in de VS en erbuiten, deel 8
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:Freedom fighters or cyber-terrorists?
Internationally famous for cyber-attacks against the Church of Scientology, government agencies of the US, Israel, Tunisia, Uganda, and others; child pornography sites; copyright protection agencies; the Westboro Baptist Church; and corporations such as PayPal, MasterCard, Visa, and Sony, who are the hacktivist collective known as ‘Anonymous’? What do they think? What motivates them?
In November 2012, The Imaginary Book Co. invited Anonymous to share their thoughts. We wanted to try and capture something of the essence of an imaginary non-organisation, to preserve it as a time-capsule for the future. We believe we’re witnessing the birth of something important, although perhaps it’s too early to even say what it is yet: a new form of democracy? Time will tell...
We assured Anonymous we would not edit, collate, correct, censor, comment upon, or judge what we received. That’s for others to do. We would simply print. We didn’t know what we’d get, if anything. This is what we got.
Anarchic, chaotic, sensible, deep, shallow, thoughtful, radical, revolutionary, and funny, this book is the first time Anonymous have written in their own words; plenty has been written about them, most of it inaccurate. And who’s to say this book itself isn’t more disinformation? Does it express the hopes and desires and motivations of the entire collective? Undoubtedly not; just a small sample of the thousands of reasons why anyone would associate themselves. Nevertheless, it’s a snapshot of Anonymous, right here and now, at this moment in time. If you want to know where Anonymous is headed, this is the book for you. When your government starts burning books, this is the one they’ll come for first…
Published to coincide with Anonymous’ worldwide “Million Mask March” on November 5th 2013, this 212 page paperback book, measuring 190mm x 250mm (7.72 x 10.08 inches) is packed with images, slogans and texts that explain, not only what Anonymous think, but how to get involved yourself.
All royalties from this book are being donated to FreeAnons, which provides legal and moral support for activists facing prosecution for involvement, alleged or otherwise, in Anonymous actions.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:YourAnonNews twitterde op maandag 14-04-2014 om 15:28:57 "I just miss - I miss being anonymous." - Barack Obama” -.- reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Barrett Brown's New Book 'Keep Rootin' for Putin' Skewers Mainstream Media Pundits
Next week, Barrett Brown's legal defense fund is publishing the jailed journalist's hilarious new book, Keep Rootin' for Putin: Establishment Pundits and the Twilight of American Competence. Brown's new work takes down talking heads and argues for the revolutionary potential of the Internet. The book couldn't address his case directly, since his prosecutors secured a gag agreement, but implicitly shows why his legal battles are so important.
You remember Barrett Brown, the colourful author who loudly defended the hacktivist collective Anonymous. After the 2007 release of his first book, Flock of Dodos: Behind Modern Creationism, Intelligent Design, and the Easter Bunny, Brown embraced the cutting edge by publishing his deep research into WikiLeaks, Anonymous, and leaked documents from military and corporate “cybersecurity” contractors in the Guardian, Huffington Post, and elsewhere. He did it all with gonzo flair, publicly labeling himself “Cobra Commander” after the cartoon character, addressing fellow activists by video from bubble baths while drinking wine, and the like.
His new book tears apart the error-ridden blather of five influential pundits and calls for their replacement by populist researchers and activists equipped with the Internet. He envisions a sort of cyber-Library of Alexandria, a more lateral space for public discourse based on the historical record rather than on opinion, often reckless or incoherent, paraded as fact and bestowed from above.
But the kind of inanity he blasts in Keep Rootin' for Putin is now aimed at him by the government. He faces more than a century in prison chiefly for sharing a hyperlink, allegedly, to cancelled credit card data from the Stratfor hack, which landed five million of the Austin-based intelligence firm's emails on WikiLeaks. The credit card data didn't come from him; he just pointed fellow researchers to it during the media buzz generated by the hack. His prosecutors shared the same link by putting it in his indictment, right there on Page 1. So it's okay, ethically, for the Department of Justice to share the link, but not for him to do it?
The government's stupidity extends to charging him for allegedly making threats against the FBI agent who raided his and his mother's homes. In addition to Brown's now-infamous YouTube rants against Special Agent Robert Smith, the prosecution cited his disapproving tweet quoting Fox News analyst Bob Beckel saying of WikiLeaks founder Julian Assange: “A dead man can't leak stuff...illegally shoot the son of a bitch.” They argue Brown's quoting of Beckel represents a threat against the FBI agent. But Assange is “not the alleged victim” Smith, Brown's lawyers say dryly in their January motion to dismiss the threat charges. “Mr. Beckel, to wit, remains unindicted.”
In that motion, the defense points out Brown's much-cited video quote that he was “going to ruin [Smith's] life and look into his fucking kids” was immediately preceded by the words “I don't say I'm going to kill him.” They point out the First Amendment requires such statements to rise to the level of a “true threat” of “physical harm” to become offenses. The motion lists the prosecution's selections from Brown's videos and Twitter timeline and shows which statements don't threaten bodily harm, which are conditional, and so on. Further, the context in the videos and on Twitter suggested he meant the sort of journalistic investigation/character assassination widely practiced by Anonymous.
Such Department of Justice stupidity is shielded by the sorts of pundits Keep Rootin' for Putin criticizes, because their professional output is noisy bullshit behind which the authorities can conspire unexamined. Brown aims to burn down the pundits' credibility.
First on the book's hit list is Thomas Friedman, unfortunately a bestselling author and twice-weekly columnist for the New York Times. He told readers in 2001 to “keep rootin' for Putin” as the man to reform Russia, in a column that paid attention to Moscow sushi bars but not the wily leader's creepy backstory. Brown points out that in 1999, Putin had been director of the Federal Security Service, the successor of the KGB, while the Kremlin was planning to bomb Moscow and blame it on Chechen terrorists. Agents from the Service were caught planting explosives in the city; other bombings were attributed to Chechens. Putin, elevated to prime minister, used the supposed attacks as a pretext to invade Chechnya, a war so popular it helped propel him to the presidency. Friedman ignored this deadly intrigue, and instead complimented the “California-Kremlin” rolls.
By itself, Friedman's mistake would be a story of a failed prediction and misplaced focus, but it gets worse. In an August 2008 column entitled “What Did We Expect?” Friedman mocked the Clinton and George H. W. Bush administrations for “short-sightedness” in foreign policy choices the columnist said fueled Putin's rise to power—with nary a word about his own, earlier propaganda for the Russian politician. These are day-in, day-out mistakes for Friedman, the book shows, but the New York Times has been feeding them to us for two decades straight.
The Washington Post gives us the same sort of serial nonsense, Brown explains, taking on Richard Cohen and Charles Krauthammer, two pundits for the paper whose columns have hit newsstands nationwide for 30 years. He traces how Cohen in 2007 accused Hillary Clinton of “forever” lying, then a year later blamed those who made the same claim, accusing them of committing a “ferocious mugging of memory.” He proves Krauthammer has been wrong about basically “every military and foreign policy matter on which he's opined from 1999 to 2010.” As Keep Rootin' for Putin piles up evidence, you begin to realize the mainstream media isn't there to inform you, but, whether through design or sheer incompetence, to distract you.
Brown wipes out William Bennett, host of a nationally syndicated talk radio show, anti-intellectual chairman of the National Endowment for the Humanities and Secretary of Education under President Reagan, and author of such bestsellers as The Children's Book of Virtues. As drug czar under President George H.W. Bush, Bennett said beheading drug dealers would be morally appropriate (“I used to teach ethics—trust me,” he explained to talk show host Larry King) and blamed addiction on Satan. “Bennett is so full of horse shit,” Brown writes. “He could fertilize every bombed-out coca field from the Yucatan to Bolivia.”
The book's last target is Martin Peretz, editor-in-chief of The New Republic for 37 years. Brown ridicules Peretz's writing style, quoting this example: “The New York Post and Reuters both report not exactly that Bernie Madoff has cancer. But that he's told his fellow inmates that he has cancer, pancreatic cancer, at that. Which means that, if the tale is true, he'll be a goner soon, very soon. Unless there's a medical miracle, as sometimes there is even in such terrible afflictions of the pancreas.” Peretz's logic is no less tortured.
Keep Rootin' for Putin, in contrast, is a quick, fun read. You can knock it out in two or three sittings, and you need not be a news junkie to follow the arguments and get most of the jokes. It's written in a bloggy style, with interludes of Led Zeppelin lyrics and surreal examples. “Let us say that I am a Roman pundit named Barriticus,” Brown writes at one point, “and I am living a few years after the initial food riots have occurred. When I givemy magnificent oration, after first having made love to several high-born young ladies...” There are also plenty of Easter eggs for bookworms, with allusions to such writers as H.G. Wells and Dostoevsky.
The book is certainly not dumbed down. His analysis ranks up there with the best of the brilliantly paranoid political authors. You have to hope the Texas juries in his April and May trials scrutinize his case as closely as he does the pundits. Given that gag agreement, it seems Brown's prosecutors fear his intelligence.
Keep Rootin' for Putinis a manifesto, not just some book version of Media Matters, the liberal fact-checking outfit whose articles you email your right-wing uncle to refute the articles he emails you. Brown argues the Internet is our superpower for removing the pundits. It allows us to catalog and cross-reference their mistakes, making a book such as his easier to produce. He has an admirable way of calling for taking up arms without scolding us. “We have a chance to dismantle the obsolete media structure that has already crippled our nation to some great extent and will cripple it further,” he says, “unless those of us who recognize this problem take some sort of, like, action.”
Cutting through the hubris of the pundits, he points out, will clear the way for our own communications. “The most important fact of the 21st century is that any individual on the planet can now communicate with any other individual on the planet,” he says, explaining that we are no longer beholden to nationalist pundits who, as leech-like intermediaries, filter and firewall information. With global networks, we can conduct our own projects for news, analysis, and action. If you want to communicate with revolutionaries the pundits ignore until it's profitable, as Brown and Anonymous did to support the Arab Spring uprisings, you can. If you want to crowdsource research into leaked emails of the government's shady contractors, as Brown's ProjectPM did, you can.
That is, unless the government shuts you down—as they're trying to shut down Brown. This new power for the people, the Internet, with its ability to forge bonds between activists worldwide and publicly archive forbidden data on sites such as WikiLeaks, terrifies the authorities. He takes it all in stride. “Life is full of possibilities,” he notes, “most of them sarcastic.”
Brown, who pleaded not guilty to every charge, is ready for the courtroom battle. On his team is legal heavyweight Charles Swift, who represented former Guantanamo Bay prisoner Salim Hamdan before the Supreme Court in the most significant case to date dealing with the war on terror, winning Geneva Conventions protections for the prisoners and limits to presidential power. Hamdan was ultimately acquitted of all charges. Attorney Ahmed Ghappour, an expert in national security cases, is also on Brown's team. Free speech advocates Reporters Without Borders, the Committee to Protect Journalists, and the Electronic Frontier Foundation have rallied to his defense.
The prosecution, despite the gag agreement, is already losing on the media front. This month, on House of Cards, a show popular enough to be mentioned on President Obama's Twitter timeline, the hacker character Gavin told the FBI to drop all of Brown's charges. Venues big and small, from this one to the New York Times to WhoWhatWhy, have been questioning the government's case.
Keep Rootin' for Putin has its faults. It could have been buttressed a bit with some statistically-minded analysis of the flows of capital and patronage that put the media institutions and their pundits in power. His asides sometimes get a little distracting, as when he states, “I'm also increasingly irritated by my own writing style.” But for the most part, the style is jazz.
As a generalist, Brown tended to shift focus, which allowed him to draw connections between disparate subjects, but gave the book a bit of a rocky history. He started writing it in 2006, then stopped, then finished it in 2010 before diving into the wild world of Anonymous. The book was originally contracted with Cambridge House Press to be published under the title Hot, Fat, and Clouded: The Amazing and Amusing Failures Of America’s Chattering Class.
If you're at all interested in the media and its failures or the Internet and its potential, you'll find Keep Rootin' for Putin entertaining and, despite the pundits' ridiculousness, inspiring. To get a copy, visit the Free Barrett Brown website and follow @FreeBarrett_on Twitter for announcements. The book will be available for donors to his legal defense fund.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Barrett Brown Signs Plea Deal in Case Involving Stratfor Hack
Barrett Brown, whose case became a cause cÚlŔbre after he was charged with crimes related to the Stratfor hack, has agreed to a plea deal with prosecutors, according to court filings.
Prosecutors filed a motion this week in a Texas court agreeing to seal the plea agreement, which the court granted (.pdf).
Brown’s attorney, Ahmed Ghappour, won’t discuss the matter, due to a court-ordered gag, but another document filed by the government this week (.pdf) hints at the nature of the deal.
In the document, which supercedes two of Brown’s previous three indictments, the government charges Brown with two crimes: allegedly assisting the person who hacked Stratfor after the fact, and obstructing the execution of a search warrant targeting Brown.
The first charge is a new one and relates to assistance Brown allegedly gave the person who hacked Stratfor “in order to hinder and prevent [his] apprehension, trial and punishment.”
According to the government Brown worked to create confusion about the hacker’s identity “in a manner that diverted attention away from the hacker,” which included communicating with Stratfor after the hack in a way that authorities say drew attention away from the hacker. The hacker is not named, and it’s not clear if it’s convicted Stratfor intruder Jeremy Hammond, or an earlier hacker who’s known to have penetrated the company first.
The obstruction charge relates to an attempt by Brown and his mother to hide a laptop from authorities during a search of her home in March 2012. Brown’s mother was separately charged with obstruction and given six months probation.
The two charges greatly reduce the amount of time he could face at a sentencing hearing, which previously had been estimated at more than 50 years.
Brown’s earlier indictments were poised to become a First Amendment test case. He was charged with 12 counts centered around a link he posted in a chat room that pointed to a file containing data stolen in 2011 from the intelligence firm Stratfor, or Strategic Forecasting. The data, stolen by Hammond, a member of the loosely affiliated Anonymous collective, included company emails as well as credit card numbers belonging to subscribers of Stratfor’s service.
Brown didn’t steal the data but simply copied a hyperlink from one public chatroom and reposted it to another.
Eleven of his charges accused him of aggravated identity theft for possessing and trafficking in stolen authentication features — which authorities identified as the three- and four-digit card verification value (CVV) printed on the back of the cards.
Last month prosecutors dropped these eleven charges against Brown, after his attorney filed a motion to dismiss on grounds that Brown’s alleged conduct did not violate identity theft statutes as written.
The twelfth charge, for access device fraud, had remained in place. That one accused Brown of illegally possessing the stolen cards — presumably cards that were found on his computer after he downloaded the Stratfor cache himself.
But that charge has disappeared from the superceding document the government filed this week, which replaced the indictment. In its place is the new charge for accessory after the fact.
Brown is scheduled to be re-arraigned, on the charges on the superceding document, on April 29 in Texas.
Brown is also facing charges related to threats he allegedly made against an FBI agent. It’s unclear if the plea agreement will cover that indictment as well. If it does, and the two cases are combined, Brown’s maximum statutory sentence would likely be five years.
Brown has been in custody since he was arrested in 2012 while in the middle of an online chat.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Cyberguerilla:
quote:
quote:Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Every time I see something like this happen, I won’t lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and “1337-ness” can get caught, I think my hacker comrades are doing something wrong.
When members of LulzSec started getting captured, it was because proxy and VPN services complied to federal request and handed over the private information of its users. I think this is wrong for a number of reasons—foremost, people should be able to have their own privacy respected. Today’s Null Byte will be demonstrating one of the methods around this: Chaining VPNs.
A VPN allows you to connect to a remote network, and over all ports, encrypt and forward your traffic. This also changes your IP address. Chaining VPNs is a tricky task, though there is a simple and uncommon method I know of. Using multiple VPNs together has the huge perk of being completely anonymous.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:F.B.I. Informant Is Tied to Cyberattacks Abroad
WASHINGTON — An informant working for the F.B.I. coordinated a 2012 campaign of hundreds of cyberattacks on foreign websites, including some operated by the governments of Iran, Syria, Brazil and Pakistan, according to documents and interviews with people involved in the attacks.
Exploiting a vulnerability in a popular web hosting software, the informant directed at least one hacker to extract vast amounts of data — from bank records to login information — from the government servers of a number of countries and upload it to a server monitored by the F.B.I., according to court statements.
The details of the 2012 episode have, until now, been kept largely a secret in closed sessions of a federal court in New York and heavily redacted documents. While the documents do not indicate whether the F.B.I. directly ordered the attacks, they suggest that the government may have used hackers to gather intelligence overseas even as investigators were trying to dismantle hacking groups like Anonymous and send computer activists away for lengthy prison terms.
The attacks were coordinated by Hector Xavier Monsegur, who used the Internet alias Sabu and became a prominent hacker within Anonymous for a string of attacks on high-profile targets, including PayPal and MasterCard. By early 2012, Mr. Monsegur of New York had been arrested by the F.B.I. and had already spent months working to help the bureau identify other members of Anonymous, according to previously disclosed court papers.
One of them was Jeremy Hammond, then 27, who, like Mr. Monsegur, had joined a splinter hacking group from Anonymous called Antisec. The two men had worked together in December 2011 to sabotage the computer servers of Stratfor Global Intelligence, a private intelligence firm based in Austin, Tex.
Shortly after the Stratfor incident, Mr. Monsegur, 30, began supplying Mr. Hammond with lists of foreign websites that might be vulnerable to sabotage, according to Mr. Hammond, in an interview, and chat logs between the two men. The New York Times petitioned the court last year to have those documents unredacted, and they were submitted to the court last week with some of the redactions removed.
“After Stratfor, it was pretty much out of control in terms of targets we had access to,” Mr. Hammond said during an interview this month at a federal prison in Kentucky, where he is serving a 10-year sentence after pleading guilty to the Stratfor operation and other computer attacks inside the United States. He has not been charged with any crimes in connection with the hacks against foreign countries.
Mr. Hammond would not disclose the specific foreign government websites that he said Mr. Monsegur had asked him to attack, one of the terms of a protective order imposed by the judge. The names of the targeted countries are also redacted from court documents.
But according to an uncensored version of a court statement by Mr. Hammond, leaked online the day of his sentencing in November, the target list was extensive and included more than 2,000 Internet domains. The document said Mr. Monsegur had directed Mr. Hammond to hack government websites in Iran, Nigeria, Pakistan, Turkey and Brazil and other government sites, like those of the Polish Embassy in Britain and the Ministry of Electricity in Iraq.
An F.B.I. spokeswoman declined to comment, as did lawyers for Mr. Monsegur and Mr. Hammond.
The hacking campaign appears to offer further evidence that the American government has exploited major flaws in Internet security — so-called zero-day vulnerabilities like the recent Heartbleed bug — for intelligence purposes. Recently, the Obama administration decided it would be more forthcoming in revealing the flaws to industry, rather than stockpiling them until the day they are useful for surveillance or cyberattacks. But it carved a broad exception for national security and law enforcement operations.
Mr. Hammond, in the interview, said he and Mr. Monsegur had become aware of a vulnerability in a web-hosting software called Plesk that allowed backdoor access to thousands of websites. Another hacker alerted Mr. Hammond to the flaw, which allowed Mr. Hammond to gain access to computer servers without needing a user name or password.
Over several weeks in early 2012, according to the chat logs, Mr. Monsegur gave Mr. Hammond new foreign sites to penetrate. During a Jan. 23 conversation, Mr. Monsegur told Mr. Hammond he was in search of “new juicy targets,” the chat logs show. Once the websites were penetrated, according to Mr. Hammond, emails and databases were extracted and uploaded to a computer server controlled by Mr. Monsegur.
The sentencing statement also said that Mr. Monsegur directed other hackers to give him extensive amounts of data from Syrian government websites, including banks and ministries of the government of President Bashar al-Assad. “The F.B.I. took advantage of hackers who wanted to help support the Syrian people against the Assad regime, who instead unwittingly provided the U.S. government access to Syrian systems,” the statement said.
The court documents also refer to Mr. Monsegur’s giving targets to a Brazilian hacker. The hacker, who uses the alias Havittaja, has posted online some of his chats with Mr. Monsegur in which he was asked to attack Brazilian government websites.
One expert said that the court documents in the Hammond case were striking because they offered the most evidence to date that the F.B.I. might have been using hackers to feed information to other American intelligence agencies. “It’s not only hypocritical but troubling if indeed the F.B.I. is loaning its sting operations out to other three-letter agencies,” said Gabriella Coleman, a professor at McGill University and author of a forthcoming book about Anonymous.
During the prison interview, Mr. Hammond said that he did not have success hacking a large number of the Plesk websites that Mr. Monsegur had identified, and that his ability to create a so-called back door to a site depended on which operating system it ran on.
Continue reading the main story
Recent Comments
TN
10 minutes ago
I hope the FBI kept a tighter leash on these informants than they did on Whitey Bulger, but I doubt it. Last I checked, neither Brazil nor...
FC
10 minutes ago
Given the current foreign situation between the US and Iran, Syria and Pakistan, I can understand the interest in gathering as much...
Norman Pollack
31 minutes ago
More evidence of the National Security State under Obama as a threat to US civil liberties, in this case, the FBI, presumed to operate only...
See All Comments
Write a comment
He added that Mr. Monsegur never carried out the hacks himself, but repeatedly asked Mr. Hammond for specific details about the Plesk vulnerability.
“Sabu wasn’t getting his hands dirty,” he said. Federal investigators arrested Mr. Monsegur in mid-2011, and his cooperation with the F.B.I. against members of Anonymous appears to have begun soon after.
In a closed hearing in August 2011, a federal prosecutor told a judge that Mr. Monsegur had been “cooperating with the government proactively” and had “literally worked around the clock with federal agents” to provide information about other hackers, whom he described as “targets of national and international interests.”
“During this time the defendant has been closely monitored by the government,” said the prosecutor, James Pastore, according to a transcript of the hearing. “We have installed software on a computer that tracks his online activity. There is also video surveillance in the defendant’s residence.”
Mr. Monsegur’s sentencing hearing has been repeatedly delayed, leading to speculation that he is still working as a government informant. His current location is unknown.
Exactly what role the F.B.I. played behind the scenes during the 2012 attacks is unclear. Mr. Hammond said he had been in constant contact with Mr. Monsegur through encrypted Internet chats. The two men often communicated using Jabber, a messaging platform popular among hackers. Mr. Monsegur used the alias Leondavidson and Mr. Hammond used Yohoho, according to the court records.
During a conversation on Feb. 15, 2012, Mr. Hammond said he hoped all the stolen information would be put “to good use.”
“Trust me,” Mr. Monsegur said, according to the chat logs. “Everything I do serves a purpose.”
Now, sitting in prison, Mr. Hammond wonders if F.B.I. agents might also have been on the other end of the communications.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:More context for Jeremy Hammond's allegations against FBI
New York Times - F.B.I. Informant Is Tied to Cyberattacks Abroad - April 23, 2014
nytimes.com/2014/04/24/world/fbi-informant-is-tied-to-cyberattacks-abroad.html
"But according to an uncensored version of a court statement by Mr. Hammond, leaked online the day of his sentencing in November, the target list was extensive and included more than 2,000 Internet domains."
The article refers to a previous paste, http://pastebin.com/xy8aQY9W
In view of NYT's reporting, we would like to add some additional context to this statement, with 3 previously unpublished paragraphs from Jeremy.
- -
On August 22, 2013, on what was supposed to be the eve of the sentencing of Hector Monsegur, aka “Sabu,” a former Anonymous comrade turned FBI informant, I released a short statement about the FBI’s use of Sabu, and by extension, me and my co-defendants, to break into the websites of numerous targets of the government’s choosing – including those belonging to foreign governments. The following day, we learned that Sabu’s sentencing was again postponed. The reasons behind these adjournments are not publicly known. But in any case, Sabu is not the real issue. What is important is how the FBI used him, and how they may still be using other hacktivists to gather intelligence and illegally break into websites without oversight, accountability or reprisal.
In my case, the FBI used Sabu to infiltrate and monitor hundreds of public and private hacker chatrooms where he was able to gain influence within Anonymous by claiming responsibility for hacks carried out by others, bragging to the media with hyperbolic quotes, accusing others of being sellouts and snitches, and encouraging hacks into government and corporate websites. He enabled hackers and facilitated hacks by supplying several servers for storage of hacked emails and databases, cracking encrypted password lists, suggesting specific targets, and offering step-by-step technical advice to people as they were breaking into systems. Impressionable and less experiences hackers, eager to please a visible Anonymous "leader" would send him their half-finished vulnerability findings; Sabu would then pass this information along to skilled hackers to finish the job.
The United States government hypes the hacker threat and celebrates convictions in order to justify the multi-billion dollar cyber security industrial complex, but they are guilty of the same crimes they aggressively prosecute and claim to work to prevent. Manipulating hackers to break into international websites to steal emails and databases is a previously undisclosed aspect of the wide-ranging cyber and surveillance operations being carried out by the NSA and other agencies. The government hopes that my conviction will legitimize the abusive tactics and illegal objectives it sponsors. I took responsibility for my actions, now it is time for the government to answer for its own crimes.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:Online hacktivist collective Anonymous has announced that it is working on a new tool called Airchat which could allow people to communicate without the need for a phone or an internet connection - using radio waves instead.
Anonymous, the amorphous group best known for attacking high profile targets like Sony and the CIA in recent years, said on the Lulz Labs project's Github page: "Airchat is a free communication tool [that] doesn't need internet infrastructure [or] a cell phone network. Instead it relies on any available radio link or device capable of transmitting audio."
The idea is that people all over the world, including those in rural areas and developing countries, will one day be able to communicate for free without the need for a mobile phone network, phone line or internet access.
While the project is workable at the moment, it is simply a proof of concept at this stage and Anonymous has revealed Airchat in the hope to get more people involved in developing the technology as well as raising funds.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:Anon_Cherry twitterde op vrijdag 25-04-2014 om 23:01:11 #Anonymous We are everywhere, even in #GTST lol 😁 #RTL4 #DutchSoapSerie http://t.co/1aRFziTZdL reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Barrett Brown lawyer: US tried to 'kill a fly with a sledgehammer'
Ahmed Ghappour speaks out after gag order was lifted and says effect of prosecutorial overreach is 'chilling to free speech'
The lawyer for Barrett Brown, the activist-journalist in jail in Texas on charges related to his involvement with computer hackers, has called for an overhaul in the way technology cases are handled by the criminal justice system to counteract potential abuses and excessive prosecutorial aggression on the part of the US government.
In his first substantive comments since a gagging order on Brown and his legal team was lifted last week, Ahmed Ghappour told the Guardian that in his opinion, the US government had tried to "kill a fly with a sledgehammer”. He accused prosecutors of imposing overly broad charges that had put unnecessary strain on the system, had profound personal implications for Brown who has been in custody for more than 500 days, and sent a chill across public debate.
“There needs to be discussion about how we avoid this kind of prosecutorial overreach in future. Prosecutors need to be more cautious in how they deal with complex cases like these to make sure the charges better reflect the conduct described, otherwise the effect is chilling to free speech,” Ghappour said.
He added: “The government’s original allegations did not fit the evidence, or the conduct, character or reputation of Barrett Brown.”
Last month the US government dropped 11 of the 17 counts it had brought against Brown, who faces three separate indictments. The dismissed allegations all related to a breach of the website of the private intelligence firm Stratfor that was carried out in 2011 by the hacking collective Anonymous.
The main instigator of the hack, Jeremy Hammond, was sentenced to 10 years in prison last November.
Brown was charged, most notoriously, with transferring stolen property, because he had posted a hyperlink on his own personal chat room, Project PM, to a website containing the hacked Stratfor material. Technology commentators warned that such a prosecution posed a threat to free speech on the internet because it raised a barrier to linking across sites on which so much of the culture of the web is based.
A day after Ghappour and the defence team filed a motion to dismiss those charges, the prosecution rolled over without explanation and dropped them.
“The government had no choice to drop the charges because they contained errors that were so wide of the mark they could not be put right by re-indicting him,” Ghappour said.
In a document released after the gagging order was lifted, the precise nature of Brown’s involvement with Anonymous over the Stratfor hack has been revealed. Paradoxically, far from attempting to commit fraud or to profit personally from the computer breach, Brown offered to contact the CEO of Stratfor to ask him whether the company wanted any redactions to be made in the hacked material before it was posted.
The document, which signed by both Brown and US attorney Sarah Saldana as a truthful account of events, quotes from internet chats between the journalist and the Anonymous hacker who carried out the Stratfor breach, named only as “O”. Brown writes to the hacker: “It occurred to me that it might be a good idea to tell Stratfor that you guys will consider making any reasonable redactions to emails that might endanger, say, activists living under dictatorships with whom they might have spoken… If they fail to cooperate, it will be on them if any claims are made about this yield endangering anyone”.
Ghappour told the Guardian that he found it ironic that the government had accused Brown of something so vastly different from what he actually did. “The government charged Brown with criminally transferring credit card information, when in fact what he did was to offer to redact sensitive material.”
The lawyer, a former computer engineer with considerable experience in super-computers, and who now teaches at the University of Texas law school, said hacking cases and other prosecutions involving new technology were so complex that grand juries and attorneys alike were often bamboozled by the evidence. “That makes the potential for abuse by the government much greater, so safeguards have to be better established.”
Brown will appear on court on Tuesday to plead guilty to all the remaining charges against him. The charges include: acting as an accessory after the fact to the Stratfor hack, threatening an FBI agent in a YouTube video, and interfering with a law enforcement officer serving a warrant on him.
The charges carry a maximum punishment of more than eight years, but Brown’s legal team will argue that the sentences should run concurrently and that given the insubstantial damage caused by the YouTube video, he should be released on time served. “Barrett expresses deep regret for what he did in making the threat, which he did impulsively at a time when he felt cornered and was unable to make rational decisions,” Ghappour said.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:The previously unreleased transcript of Barrett Brown’s September 4 gag hearing in Dallas, obtained by WhoWhatWhy, shows just how far the government tried to go to shut up a “hacktivist journo” who challenged the status quo.
The lead prosecutor, Candina Heath, told the judge that, during the trial, Brown should be forbidden from publishing criticism of the government. That conversation, revealed in the transcript, was out of earshot of those in the gallery when WhoWhatWhy attended the hearing.
At the time of that hearing, Brown faced more than a century in prison for, allegedly, threatening an FBI agent, sharing a link to credit card data publicized during a hack, and conspiring to hide his laptops. Free speech advocates, such as Reporters Without Borders and the Committee to Protect Journalists, labeled the charges nothing less than retribution for his anti-establishment work.
But prosecutors sought to go further, with a gag order that undoubtedly would have been among the most sweeping restrictions on an American journalist’s free speech—reminiscent of the eighteenth-century Alien and Sedition Acts, which jailed writers and editors for criticizing the authorities.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Anonymous, Cambodja, FBI.
quote:
Het gaat verder.quote:The National Police were cooperating with the FBI to conduct an investigation on [hacking] when we found out these two suspects hacked the NEC…and other government institutions." - Lieutenant General Chhay Sinarith, Cambodia's Ministry of Interior internal security department ************************************************************************************************* inviting the FBI in to your country to bust Anonymous is a bad idea. anyone reading this should be wondering why the FBI are even in Cambodia, is this US tax payer dollars at work, chasing students engaging in online protest around the world? th prime minister of Cambodia, Hun Sen has kept himself in office more than 27 years, does that sound like a democratic ruler to you? there are a lot of questions here:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


^Anonymous.
^Flikkerkindertjes die de meme nooit hebben begrepen en geloven dat er een organisatie is
-
Verder staat de hele op vol met onjuistheden maar ok.
SPOILEROm spoilers te kunnen lezen moet je zijn ingelogd. Je moet je daarvoor eerst gratis Registreren. Ook kun je spoilers niet lezen als je een ban hebt.Vraag yvonne maar hoe tof ik ben, die gaf mij er ooit een tagje voor.


Jij bent juist degene die het niet heeft begrepen. Anon is geen organisatie.quote:Op zaterdag 3 mei 2014 01:38 schreef BaajGuardian het volgende:
images?q=tbn:ANd9GcQrLeycrjOqzVNWfVNntroPgk26e8LRYPK77bNzNcOwIjtR2DgNtw
^Flikkerkindertjes die de meme nooit hebben begrepen en geloven dat er een organisatie is


Dat zeg ik, anonymous is een fucking internet grap, altijd al geweest. Het begon met dat mensen de vraag stelden of alle anon op chan niet ÚÚn persoon was, en toen ging dat dus leven. Het werd net zoiets als de fingerboxes, doen alsof iedereen er van wist en je kreeg een gevoel van er bij horen als jij het ook ging doen. EFG had eerst geen gezicht, toen kreeg het het masker van V als gezicht, toen begonnen mensen de grap 'anon' te versterken door 'het dat gezicht te geven. Alleen sommige mongolen namen het 'te' serieus, nadat wat random kutkinderen/newfags gestuurd door oldfag bullshit raid threads voor de lulz wat 'grote dingen' gingen doen met de low orbit progjes, raids waren gewoon domme kutgrappen, er was geen serieus doel bij behalve dan chaos zaaien en kunnen lachen als het op het nieuws kwam. Dat evolueerde en evolueerde tot je dus de white knight ultra imbecielen kreeg die zich gingen organiseren op demonstraties en dergerlijke statements.quote:Op zaterdag 3 mei 2014 01:54 schreef Nemephis het volgende:
[..]
Jij bent juist degene die het niet heeft begrepen. Anon is geen organisatie.
Toen werd dus het idee ge-forward dat anon een organisatie was met leiders, dat het wat voorstelde, een leger/hackerscollectief had, elk groepje scriptkiddies noemde zich opeens deel van anon en ging op irc faalgroepgesprekjes houden (die makkelijk gemonitord werden
En dat allemaal gebaseerd op dus de illusie dat anon in eerste zin 'ÚÚn persoon' was en uiteindelijk 'een organisatie'.
Terwijl de werkelijkheid is dat anonymous geen organisatie is, en ook geen leden heeft.
Het is een beetje als alqaeda, het bestaat in weze niet werkelijk maar iedereen roept na een aanslag dat ze er bij horen.
-bron: een van de oudste ancientfags/true oldfags.
Vraag yvonne maar hoe tof ik ben, die gaf mij er ooit een tagje voor.


Ach gut, een miskende oldfag. "Ik was er bij" "Ik weet het beter" 
Als je de afgelopen jaren nou wat zinnigs had bijgedragen aan deze thread, maar nee hoor. Meneer ligt een paar jaar te maffen en komt dan zeuren dat het niet goed is.
Loser.
Als je de afgelopen jaren nou wat zinnigs had bijgedragen aan deze thread, maar nee hoor. Meneer ligt een paar jaar te maffen en komt dan zeuren dat het niet goed is.
Loser.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Glenn Greenwals heeft al zijn documenten. Hij komt binnenkort met een boek over documenten die meer aandacht verdienen dan een enkel krantenartikel.quote:Op zaterdag 3 mei 2014 12:40 schreef polderturk het volgende:
Het is lang geleden dat Snowden iets gelekt heeft. Zou hij nog iets achter de hand hebben?
NWS / Monitoring NSA in de VS en erbuiten, deel 8
[ Bericht 9% gewijzigd door Papierversnipperaar op 03-05-2014 12:52:41 ]
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Ik heb genoeg gedaan nog voordat een samenraapsel 12 jarigen dacht dat ze wat deden door maskertjes te dragen. Voordat wikileaks bestond, voordat ATS bestond al. En dat noemt mij een loserquote:Op zaterdag 3 mei 2014 08:52 schreef Papierversnipperaar het volgende:
Ach gut, een miskende oldfag. "Ik was er bij" "Ik weet het beter"
Als je de afgelopen jaren nou wat zinnigs had bijgedragen aan deze thread, maar nee hoor. Meneer ligt een paar jaar te maffen en komt dan zeuren dat het niet goed is.
Loser.
Vraag yvonne maar hoe tof ik ben, die gaf mij er ooit een tagje voor.


Was jij dat, die het internet bedacht heeft?quote:Op zaterdag 3 mei 2014 19:34 schreef BaajGuardian het volgende:
[..]
Ik heb genoeg gedaan nog voordat een samenraapsel 12 jarigen dacht dat ze wat deden door maskertjes te dragen. Voordat wikileaks bestond, voordat ATS bestond al. En dat noemt mij een loser


Jullie kennen mij duidelijk niet, vooral niet wat mijn werk anno 2001-2006 betrof.quote:Op zaterdag 3 mei 2014 19:48 schreef Nemephis het volgende:
[..]
Was jij dat, die het internet bedacht heeft?
Vraag yvonne maar hoe tof ik ben, die gaf mij er ooit een tagje voor.


Nou, spreek niet in raadselen en licht het toe dan svp. Ik ben geen helderziende.quote:Op zaterdag 3 mei 2014 19:48 schreef BaajGuardian het volgende:
[..]
Jullie kennen mij duidelijk niet, vooral niet wat mijn werk anno 2001-2006 betrof.


quote:http://0paste.com/5897
Anonymous / @Anarchoanon / #Every5th
MEDIA ALERT
FOR IMMEDIATE RELEASE
Contact: @anarchoanon anarchoanon@riseup.net
(We operate anonymously to avoid retaliation by police, but we are real
people wiling to work with you to help you tell this story as you see
fit.)
Denver 5/5- Wednesday, May 5th saw the 7th monthly “Every 5th” protest in
the streets of Denver. The loose internet-based activist collective known
as “Anonymous” has been holding these events to call attention to
different issues in the city and the nation. The last event on April 5th
was a protest against police brutality, which was predictably attacked by
the Denver Police Department. This month's protest was to call for an
“end to Denver's war on free speech,” to call attention to the
unconstitutional anti-protest measures often taken by the police
department. The number of marchers fluctuated between 30 and 100
throughout the day. With slogans and banners calling attention to police
brutality and free speech issues, the march went all around downtown,
passed through the Auraria college campus, and visited the 16th st mall.
While the march was on the sidewalk outside Rock Bottom Brewery on 16th
st, a line of riot police charged the march and violently pushed several
people, including elderly women and children, to the ground in addition to
making several unprovoked arrests. After a tense standoff outside Rock
Bottom, the march went back up 16th st to disperse at the capitol
building. As people dispersed to leave the protest, squads of Denver
police stalked people leaving the protest, ambushing groups and
individuals in parking lots and streets, apparently as “revenge” for their
protest against the Denver Police Department. It was very apparent to
eyewitnesses that Denver Police were maliciously targeting protesters in
an attempt to intimidate them into ceasing first amendment-protected
protest activity. The Denver Police continue to claim that their actions
were to keep the public safe, which is very odd when reconciled with the
sounds of innocent bystanders screaming as the police rushed and attacked
people who were standing on the sidewalk. The protest was not hurting
anyone, there was no danger and no acts of destruction. The only danger
present was that crowds of people on the 16th street mall might see that
there are people ready to stand up against the privatized, militarized,
and gentrified direction Denver has been taking of late.
An account by a mother who was violently knocked to the ground by DPD
during the attack on the crowd outside Rock Bottom Brewery:
“I was walking on the sidewalk, playing my drum when the police suddenly
attacked the crowd. A police officer pushed me to the ground, someone
picked me up, and then another police officer picked me up and threw me
into a man standing nearby. The officer then yelled at me to “get off of
him!” after the police themselves threw me into this man. This was my
first protest in Denver, and I never said “fuck the police.” I was
conducting myself in a peaceful and legal manner, and the police really
opened up my eyes in terms of how they deal with protests in this city. I
did not feel safe and in fact felt endangered by the officers' aggressive
behavior. I asked who was in charge, but no officers would tell me who is
in charge. Who is responsible for this? This is not ok.”
The person who provided the above eyewitness account is available for
interviews upon request. We can provide other eyewitnesses as well.
“A group of us was calmly walking away from the protest, heading towards
the Capitol Hill neighborhood. As we passed through a parking lot, a
group of police officers on bicycles suddenly surrounded us, rammed our
friend's bike with their bike, knocking him to the ground. They proceeded
to chase him and arrest him without explaining themselves. Another
individual present was punched in the face although he was never detained
or accused of a crime. This kind of behavior by Denver Police is clearly
a direct retaliation against us exercising our first amendment rights to
publicly denounce the corruption and brutality of this city's police
force. Today, I am ashamed to be a taxpayer in the city of Denver,
because my tax dollars are financing the violent repression of peaceful
dissent.”
Video of police assaulting the crowd outside Rock Bottom Brewery:
A very interesting conversation between Denver Police twitter account and
“Your Anon News” an influential anonymous twitter account with 1.2 million
followers:
pic.twitter.com/KzelGDN08B
pic.twitter.com/h8HBqICijn
pic.twitter.com/lVoZZR6Pcj
pic.twitter.com/9ZcDM1WZgQ
pic.twitter.com/2AHAw8bkxr
pic.twitter.com/mhr8ygqN5T
pic.twitter.com/oVgmNpWxhk
pic.twitter.com/uTqlYl1fbi
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Protesters set up camp at net neutrality rally outside FCC headquarters
Occupy-style protest against proposed 'open internet' rules that protesters say will give control of the web to major corporations
Protesters set up camp outside the Federal Communication Commission (FCC) on Wednesday to fight plans they say will create a two-tier internet and hand control of the web to major corporations.
The rally – reminiscent of the Occupy-style rallies that started in 2011 – started outside the FCC’s Washington headquarters at noon with protesters from Fight For the Future, Popular Resistance and others unfurling banners reading “Save the Internet”.
Protesters then announced they intend to camp out outside the FCC until 15 May when the regulator is expected to announce new rules for the internet that will formalise plans for higher speed internet for those able to pay for it. On Wednesday Google, Facebook and Amazon joined around 100 other technology companies in signing a letter to the FCC rejecting "individualised bargaining and discrimination" for internet traffic.
"[The FCC must] take the necessary steps to ensure that the internet remains an open platform for speech and commerce," the letter says.
Public interest groups have become increasingly concerned that the new rules will end “net neutrality” – the concept that all internet traffic should be treated equally on the web. FCC chairman Tom Wheeler has defended his plans for what he calls the “open internet”.
The future of net neutrality has effectively been in limbo since a federal court struck down most of the FCC’s open internet order in January in a case brought by Verizon. The loss paved the way for fast lanes that have the major broadband providers have lobbied hard for, and for which they plan to charge extra to their biggest users.
"We don’t have armies of paid lobbyists at our disposal but we can not let the freedom of the internet be hijacked by giant monopolies,” said Evan Greer of Fight For The Future.
More than a million people have now signed petitions to the FCC calling for them to enshrine net neutrality rules and prevent a tiered system.
A group of 86 organizations, including the American Civil Liberties Union, Free Press and Reddit, are asking the FCC to reclassify broadband companies as "telecommunication services", which would give the commission the authority to impose net neutrality rules on them.
Wheeler has said the FCC’s new rules will protect net neutrality.
“The Internet will remain like it is today, an open pathway,” Wheeler wrote in a FCC blogpost in April. “If a broadband provider (ISP) acts in a manner that keeps users from effectively taking advantage of that pathway then it should be a violation of the Open Internet rules.”
Critics charge, however, that cable firms will successfully challenge any new rules to tie their hands unless the FCC’s regulatory control over them is increased and point out cable firms have already effectively created a two-tier system. After the FCC lost to Verizon in January, a tiered system has already started to emerge with Netflix and others striking deals for a faster service with cable firms.
“The internet is as necessary to our society as shelter and water, people should have equal access to it,” said Greer. “We have seen an unbelievable amount of support from people since these new rules emerged. It may seem technical but it affects everyone’s life and people are not going to just stand by and let this happen.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:It seems like the FBI is not quite finished with one of its most valuable assets, Hector Monsegur (aka Sabu) the former Anonymous and LulzSec member who had his sentencing postponed for a seventh time on Wednesday.
Monsegur was due before Judge Loretta Preska in New York on Thursday but he has once again had his sentencing postponed, according to sources speaking to the Daily Beast website.
No new date has been set for Monsegur's next court appearance yet, giving us no indication of whether or not the FBI want to keep using Monsegur for a long or short period of time. His sentecning was last adjourned on 8 May.
Monsegur will face punishment for crimes associated with the 50 Days of Lulz campaign he and his fellow hackers carried out which saw them attack companiess such as Sony and EA as well as law enforcement agencies including the CIA and SOCA.
The former Anonymous hacker has already pleaded guilty to 12 criminal charges, including multiple counts of conspiracy to engage in computer hacking, computer hacking in furtherance of fraud, conspiracy to commit access device fraud, conspiracy to commit bank fraud and aggravated identity theft.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Autistic Hacker Helped FBI Nail Anonymous Boss
Criminal charge was dropped after man, 26, cooperated with the feds
Het artikel gaat verder.quote:MAY 13--In an effort to identify leaders of Anonymous, the FBI arrested an autistic New York man and then used him as a cooperating witness to help snare a notorious fellow hacker who was subsequently indicted for his central role in a series of high-profile online attacks, The Smoking Gun has learned.
In return for the hacker’s cooperation--and in light of his autism--Department of Justice officials initially agreed to defer prosecution on a criminal complaint charging the man with hacking Gawker Media, an illegal incursion that yielded registration information for more than a million individuals who signed up with the popular blog network.
Federal prosecutors eventually dropped the hacking charge altogether, according to court records that were kept under seal long after the hacker’s arrest by a team of FBI agents. Investigators were concerned that if the man’s cooperation became public, he would be harassed by hackers then being targeted by the FBI. Additionally, disclosure of his cooperation, prosecutors contended, “would jeopardize substantial ongoing investigations into the defendant’s former co-conspirators, many of whom are suspected of carrying out substantial computer hacks against several businesses.”
So, to “help ensure the defendant’s safety,” Thomas “Eekdacat” Madden became, for a time, “John Doe.”
The 26-year-old Madden, whose cooperation has not been previously disclosed, lives with his parents in Troy, a city 10 minutes outside Albany. An only child, Madden graduated in December 2010 from Rensselaer Polytechnic Institute, where he completed a double major in computer science and mathematics, according to school records.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Report claims Anonymous will protest Glenn Greenwald for ties to PayPal billionaire
The Internet hacktivist group Anonymous is calling for protests against author and civil liberties advocate Glenn Greenwald because of his relationship with eBay founder Pierre Omidyar.
In a release posted to Pastebin, the secretive activist group is calling for members to attend and disrupt scheduled book signings where Greenwald will be promoting his new book, No Place to Hide: Edward Snowden, the NSA, and the U.S. Surveillance State.
The point of contention between Greenwald and the group stems from his relationship with First Look founder and eBay billionaire Pierre Omidyar.
eBay purchased PayPal in 2002.
Representing the “PayPal 14,” — a group charged under the Computer Fraud and Abuse Act after they attempted to disrupt PayPal’s operations in retaliation for PayPal’s refusal to process donations to WikiLeaks — Anonymous stated that the 14 are “struggling to raise more than $80,000 in court-ordered restitution” that must be paid to eBay/PayPal.
Anonymous claims that, while the 14 face jail and fines, Greenwald and Omidyar have been cashing in on the “digital information war.”
“Greenwald and Pierre occasionally express tepid ‘support’ for the PayPal14. But where’s the $80,000? That’s lunch money to Greenwald or Pierre. For the PayPal14, it’s a crushing financial burden,” they wrote. “Pierre, according to Forbes, rakes in $7.8 billion per year while the PayPal14 struggle to stay afloat. Pierre started off First Look, Greenwald’s news media outlet, with $50 million in funding — tens of millions more than $80,000.”
Anonymous is also complaining that Greenwald and Omidyar are watering down the “hacktivist movement” by not publishing all of Edward Snowden’s documents, or heavily redacting them, thereby keeping “aggressive, non-celebrity journalists from finding answers and pro-freedom hackers from building better defenses.”
Anonymous members are instructed to attend Greenwald’s book signings to protest, record their activities, hand out fliers, and explain the relationship between the author and his financial benefactor.
The “YourAnonNews” Twitter account expressed support for the campaign on Monday, along with the account representing Occupy Wall Street.
The Twitter account for WikiLeaks also backed the campaign, though they suggested that only PayPal — and not Greenwald — should be targeted.
. #Paypal14 are rightly fuming about Paypal boss @Pierre Omidyar (though the proxy attack on @GGreenwald is harsh) http://t.co/r4EauU1wTd
— WikiLeaks (@wikileaks) May 12, 2014
Omidyar has previously called for leniency for the PayPal 14, saying they should have been cited for a misdemeanor instead of facing felony charges.
Raw Story has requested a statement from Glenn Greenwald.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous projected sign: ‘United Stasi of America Don’t Spy on Us’
Hacktivist group Anonymous projected another message on the USA embassy in Berlin on Thursday night before heading away in an unidentified van. Disguised in capes and Guy Fawkes masks, the Anonymous members used a generator and a projector to display the message: ‘United Stasi of America Don’t Spy on Us.’ This is the third time the group has projected their protest against the US.
The action comes one week after Edward Snowden’s latest document ‘black budget’ was published in the Washington Post, outlining how the NSA use encryption codes, similiar to those used in banking systems, to trade data on medical records, web searches, Internet chats, and phone calls of citizens around the world.
The Guardian, who Snowden released NSA secret files to, published an article on Friday morning stating how the NSA uses internet traffic to access communications around the world and how to avoid getting spied on.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:State Watchdog threatens to block Twitter under new blogger bill
A senior official from Russian control agency Roskomnadzor says new restrictions would apply to all bloggers who write in Russian, even if they live abroad, adding that whole platforms can be blocked inside the country for refusal to cooperate.
The new law defines ‘popular bloggers’ as those having 3,000 or more visitors per day and demands that such people were registered under their real names and follow some basic rules similar to those mentioned in the Law on Mass Media – verify their reports and abstain from posting slander or anything that can be described as ethnic, religious or social hatred. The law must come into force on August 1 this year.
However, the law has no provisions connected with the global and trans-border nature of blogs and the internet as a whole. The document is not saying directly if it applies to cases in which both the authors of blogs and the blog platforms are based outside Russia.
Deputy head of Roskomnadzor Maksim Ksendzov said that this would not matter.
“The law is not tied to the territorial registration or passport data. If someone writes in Russian or any other language used by the peoples of the Russian Federation, if he or she is seeking to attract the Russian audience’s attention and if they use Russian sites for this, such people will have to observe the law,” the official said in an interview with popular daily Izvestia.
Ksendzov added that as the law offers no means to influence the foreign-based bloggers the Russian agency would most likely have to block the whole blog platform or social network in Russia, but only after they refuse to take down the illegal content. Roskomnadzor already practices such scheme as part of the enforcement of the federal law that bans the dissemination of terrorist and extremist information and also the federal law on protection of children.
The official said that major companies like Twitter and Facebook were still reluctant to cooperate, unlike Google that had been removing offensive and illegal videos from its YouTube portal for some time already.At the same time, the way Twitter was encoding its traffic would lead to complete blocking of the microblogging service on the Russian territory even after Roskomnadzor blocks only one tweet, he noted.
Ksendzov suggested in the interview Twitter’s objectives in Russia were not only commercial, but also political and this was the reason of the uncooperativeness.
“Twitter is a global tool for distribution of political information. When they interact with us they use the audience as a means for reaching their goals. At the same time the value users and their interests for the company is extremely low,” the head of the Russian watchdog said.
“By gradually refusing to comply with our demands they are deliberately creating the conditions in which the blocking of this resource on our country’s territory becomes practically inevitable,” Ksendzov complained.
Following the release of the interview senator Ruslan Gattarov also blasted Twitter’s uncooperativeness at a Friday session of the Upper House’s commission for development of information society.
“The ugliest situation of all is that we have with Twitter. This company is not observing the Russian laws and only slightly reacts to the Roskomnadzor demands,” Gattarov said.
At the same time, Russian Prime Minister Dmitry Medvedev, known for his fondness with technology and gadgets, has played down the situation in his Facebook account.
“As an active user of social networks, I hold that the Russian laws must be observed by everyone – the networks and the users alike. But certain civil servants, responsible for the development of the industry must sometimes turn their brains on and give no interviews that announce the shutdown of social networks,” Medvedev wrote.
Vladimir Putin’s press secretary Dmitry Peskov has said that the authorities in the Kremlin were convinced that all foreign companies must observe all laws in force on the Russian territory. “The law exists to be observed,” Peskov told Interfax.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:Anonymous, the online hacktivist collective, is calling on people to read and disseminate a pirated copy of Glenn Greenwald's new book about Edward Snowden, in protest at his links to eBay founder Pierre Omidyar.
The campaign is a bid to raise awareness about the plight of the PayPal 14, a group of Anonymous members who were convicted of taking part in a cyber-attack against PayPal in 2010.
The campaign is trying to help raise the $80,000 (ú51,170) the group has been court ordered to pay PayPal in compensation for the damage it caused during the attack.
At the time of publication, the the GoFundMe page has raised $6,514 of the total.
The campaign, which was announced by Anonymous on Monday, called on supporters to physically protest at events Greenwald was taking part in this week to promote his book called No Place to Hide, which details his publication of a trove of top secret documents stolen by Edward Snowden and relating to governmental spying at the NSA and GCHQ.
Billionaire backer
In the press release published by Anonymous, the group said:
"As Greenwald gets a book tour, the PayPal14 get sentencing hearings. He is traveling the world to promote his book about Snowden's NSA leaks, and the 14 are struggling to raise more than $80,000 in court-ordered restitution for eBay/PayPal, companies ultimately overseen by Greenwald's billionaire backer, Pierre Omidyar."
Greenwald announced earlier this year that he would be working as one of the editors of a new website called The Intercept, which is owned by First Look Media - a company belonging to Omidyar.
PayPal is a wholly-owned subsidiary of eBay, which is why Omidyar is being targeted.
The Anonymous campaign calls on people to help promote the fundraising drive, to engage Greenwald and Omidyar on Twitter by using the hashtag #PayPal14 and to physically protest at Greenwald's book signing.
Pirated copy
While not a part of the original press release, many of the prominent Anonymous Twitter accounts - including @YourAnonNews which has more than 1.2 million followers - have been promoting links to a pirated electronic copy of Greenwald's book.
Greenwald kicked off his book tour on Tuesday in New York before travelling to Washington and Boston. While a member of Anonymous has claimed to IBTimes UK that there we people their in Anonymous' name, at least at some of the events, it doesn't seem as if they had much impact on the signings themselves.
Greenwald has yet to respond publicly to the campaign and both he and Omidyar have not responded to requests for comment from IBTimes UK.
Wikileaks, which was the reason the attack on PayPal happened in the first place, has pledged its support to the fundraising drive and protest campaign against Omyidar, but said the "proxy attack" on Greenwald was "harsh".
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:It appears likely that Edward Snowden was involved with CryptoParty. Cryptome has uncovered a public key for cincinnatus@lavabit.com, which is the same alias he used to contact Glenn Greenwald — and it’s associated with the organizing of an event in Honolulu, Hawaii in December 2012, where the now-famous NSA whistleblower was then living. Here’s the original page via Wayback Machine. Although I’m awaiting official confirmation from his lawyers, the odds are very high that it was him. CryptoParty is a global movement that was spawned nearly two years ago from an idea by Asher Wolf, an Australian activist.
quote:There’s also the video that Snowden created which I discovered in July last year, and has since been confirmed by Greenwald; a tutorial on GPG encryption for journalists, which was credited to “Anonymous 2013″ and posted by the Vimeo user anon108. Although setting up PGP proved too difficult for Greenwald, behind the voice-changing effect is someone who sounds extremely knowledgable about the mechanisms of digital security. Combined with the EFF and Tor Project stickers pictured on his laptop, the Anonymous and CryptoParty connections show a man attuned to the struggle for our rights on the internet; one with his eye on those communities.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Waarom doneert Gabriella Coleman aan de #Paypal14
quote:PayPal14
In December 2010 when Wikileaks was stirring the pot of controversy with its hard hitting leaks, cowardly companies like PayPal and Visa caved into hidden but significant political pressure and blocked Wikileaks. This act of blatant censorship infuriated many citizens who expressed their dismay on every available online channel. Anonymous was well poised to harness the fury ball of anger and did so by coordinating one the largest DDoS campaigns the Internet has yet witnessed, variously called Operation Avenge Assange or Operation Payback.
Media attention was frenzied, catapulting this collective of collectives out of relative obscurity and into the international spotlight. In the New York Times, one of the Internet’s original patron saints—John Perry Barlow— prophetically cast the Anonymous campaign as “the shot heard round the world—this is Lexington.” In quoting Emerson’s poem “Concord Hymn,” Barlow hearkens to the first gunshot fired in the American Revolutionary war at the Battle of Lexington, which marked the outbreak of armed combat between the Colonies and the Kingdom of Great Britain. The information war, well under way, had seen a decisive battle.Months later, a slew of ordinary participants were arrested for their contributions.
For many who supported the protest, this once spectacular and exciting collective outcry has likely faded from memory. But for those facing the charges, it never went away. They have endured three years of expensive, time consuming and stressful battles against a mighty and well resourced US DoJ. Thanks to excellent legal support, they have accepted a plea bargain and the fine they are collectively facing is now a lot less than what it could have been: $86,000.
The DDoS is understandably a controversial political among geeks, hackers, and citizens. It has its limits and strengths and I myself am far from being a staunch fan. Whatever you may think of the DDoS (and I recommend looking out for this book on the DDoS by Molly Sauter), the Pay Pal 14 were driven by conviction. They have explained it with candor on their fundraising website: “They were not spreading malware, hacking servers, or even damaging the systems themselves. . . These people were making a statement and publicly exposing PayPal in front of their shareholders and the world on behalf of those of us who value freedom of information.” Their intervention also came at the right time helping to keep the issue of corporate censorship under the public limelight for a few precious weeks.
The time has come for those of us who believe in the right to dissent online to help them raise the funds so the can resume their interrupted lives.The government banks on the fact that activist movements, especially those running on spontaneity, often dissipate, fracture, and vanish. They bank on the fact that putting activists through an expensive legal wringer will cower many others into silent submission. We can prove them wrong. Lending support sends a strong message back: under adversity, the movement can preserve and take care of their own.
Yesterday I pledged $350 and if matched in 36 hours, I promised to double the amount. I was thrilled to see it took less than five hours for that to happen. I hope you consider donating what you can and spreading the word.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
De column gaat verder.quote:As I described in a previous column, the copyright monopoly cannot be enforced without mass surveillance. There is no way to tell a private conversation in a digital environment from a monopolized audio file being transferred, not without actually looking at what’s being transferred. At that point, the secrecy of correspondence has been broken and mass surveillance introduced.
The copyright industry has been continuously and relentlessly pushing for more mass surveillance, including surveillance of citizens who aren’t under any suspicion (“mass surveillance”) for this reason. They defended the now-illegal Data Retention Directive, which logs everybody’s communications and location all the time (specifically including yours), as well as similar initiatives.
Most notably, the copyright industry is known for using child porn as an argument for introducing mass surveillance, so that the mass surveillance can be expanded in the next step to targeting people who share knowledge and culture in violation of that industry’s distribution monopolies. This is a case study in taking corporate cynicism to the next level.
This mass surveillance is also what feeds the NSA, the GCHQ, and its other European counterparts (like the Swedish FRA). It is continuously argued, along the precise same lines, that so-called “metadata” – whom you’re calling, from where, for how long – is not sensitive and therefore not protected by privacy safeguards. This was the argument that the European Court of Justice struck down with the force of a sledgehammer, followed by about two metric tons of bricks: it’s more than a little private if you’re talking to a sex service for 19 minutes at 2am, or if you’re making a call to the suicide hotline from the top of a bridge. This is the kind of data that the spy services wanted to have logged, eagerly cheered on by the copyright industry.
This has a direct connection to free speech as such.
In Germany, the effect of this logging and violation of people’s privacy has been studied extensively. According to a study conducted by polling institute Forsa before the data retention was in place, over half of German citizens would refrain from placing communications that could be used against them in the future – drug helplines, psychologists, even marriage counseling. A significant portion of Germans had already refrained from taking such contacts for that reason.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:How did security firm Mandiant put names to two previously unknown Chinese hackers who, it says, steal American corporate secrets for the Chinese government? With a little inadvertent help from Anonymous.
Mandiant's 74-page report covers a particular hacking group referred to as "APT1" and contends that the group works for or under the direction of the Chinese government as part of the military's secretive "Unit 61398." The report ties a huge string of hacks over the last few years to Unit 61398 and goes on to show the building where the hacks might be hatched. The report is stuffed with detail uncommon in these types of stories, and even includes a translated Chinese document showing a local telecom company agreeing to Unit 61398's request for additional fiber optic connections in the name of state security.
The Mandiant researchers then tried to go one step further, putting at least a few real names to the coders involved. (BusinessWeek recently did something similar, with fascinating results.) Mandiant began with a malware coder who goes by the name "UglyGorilla"—a name which is left repeatedly in code tied to the APT1 group.
Back in 2007, for instance, Mandiant says that UglyGorilla "authored the first known sample of the MANITSME family of malware and, like any good artist, left his clearly identifiable signature in the code: 'v1.0 No Doubt to Hack You, Writed by UglyGorilla, 06/29/2007'[sic]." But despite all the uses of the name "UglyGorilla" buried in code samples, leads to the person's actual identity were hard to come by—until Anonymous hacked security firm HBGary Federal in early 2011.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:#OpPayBack: Anonymous Takes Down US Army, Air Force, Marines and Navy websites
Earlier today, the online hacktivist group Anonymous conducted a massive Denial-of-service attack (DDoS) on defense related websites of the United States.
Attack was conducted under the banner of Operation PayBack. As a result, nineteen high profile websites belonging to US Army, US Marines, US Air Force and US Navy were taken down.
The news of successful DDoS attack was announced by Anonymous via their Twitter handle @Anon_Centre. While the list of all targeted websites is available here.
tangodown-anonymous-takes-down-us-army-air-force-navy-and-marines-websites-for-oppayback-2
The army.mil domain was down for hours as seen in the below given screenshot:
It is unclear if Anonymous will keep on attacking these domains or there are some other targets in the list. Stay in touch as we will keep you posted with more on this attack.
At the time of publishing this article, all targeted websites were restored and working online.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Weev stuurt de rekening.
quote:An open letter to members of the New Jersey District Court, FBI, and DOJ, consisting of an invoice.
To the Honorable Susan D. Wigenton, US Attorney Paul J. Fishman, Assistant US Attorney Zach Intrater, and FBI Special Agent Christian Schorle,
"Whether 'tis nobler in the mind to suffer the slings and arrows of outrageous fortune, or to take arms against a sea of troubles, and by opposing end them?" -Shakespeare
It has long been one of the fundamental pillars of our system of law that when one commits a crime against another, they are made to give restitution to their victims.
I have, over the course of 3 years, been made the victim of a criminal conspiracy by those in the federal government. This was a conspiracy of sedition and treason, perpetrated with violence by a limited number of federal agents to deprive me of my constitutional rights to a fair trial and unlawfully put me in prison. This is not a hallucination on my part. These claims were in fact verified by the Third Circuit Court of Appeals when they vacated the false judgement against me imposed by the court of Judge Susan D. Wigenton. Perhaps you haven't read the opinion of the appeals court exposing all of you as liars and seditionists yet. If so, here you go: https://www.eff.org/files/2014/04/11/weev.pdf
On January 18th, 2011 I was kidnapped at gunpoint by the US Marshals from Fayetteville, Arkansas, the town where I was born, based off a criminal complaint based on complete falsehoods written by FBI Special Agent Christian Schorle. The complaint alleged I had broken into AT&T's servers (I hadn't, as confirmed by the appeals court which verified no evidence was presented that any of my accesses bypassed security restrictions) and that New Jersey was the jurisdiction because AT&T was headquartered there. In actuality, AT&T was headquartered at the time in Houston, Texas. This sort of blatant falsehood is verifiable by a simple Google search.
Thus I was taken from Arkansas, the nicest place I ever lived, and brought to Newark, New Jersey, a place worse than any of the many third world countries I have visited. I was held under bail conditions where the government refused to allow me to work in my industry, told me where I could live (I was not allowed to return to my birthplace of Arkansas where I lived at no expense, and instead forced to pay rent in New Jersey), and was subject to the indignity and expense of regular mandatory travel to the Newark courthouse to urinate in front of a federal employee. I was told where I could travel, and where and how I could sleep. My time and life was completely monopolized by the federal government during this period, again based off false statements from a lying piece of shit in the federal government.
I then spent a swath of the next years struggling to find an attorney because the overworked federal defender I was given told me to plea to false charges because even if I was innocent there was no way I'd win. I then struggled to get this attorney enough resources to fight the case while he was struggling to keep the lights in his office on.
Going to trial two years later, the United States Attorneys and FBI repeatedly perjured themselves in order to wrongfully convict me. FBI Special Agent Phillip Frigm claimed that the manufactured evidence was "secured" by MD5 signatures. This was factually wrong and perjurously asserted as true under oath-- MD5 signatures do not work in the manner he implied. Assistant US Attorney Michael Martinez claimed that I committed a crime because my use of the Internet was "not like going to ESPN and checking my favorite sports team's scores", and Assistant US Attorney Zach Intrater claimed that I had committed a crime because I automated web requests with a script. This, of course, ignores the fact that the vast majority of web requests are programmatic and automated-- total API requests and automated GET per year are approaching the quadrillions. Lie after lie after lie stacked up in open court on behalf of the agents of the government. If there was any integrity left in the justice system there would be special prosecutors appointed to charge you with the perjuries you committed.
Orchestrating this circus was the judge, Susan D. Wigenton, who not only ignored my constitutional right to a trial in a reasonable location but blatantly allowed manufactured evidence and perjury on the part of FBI and DOJ employees in her courtroom. The rights I have enumerated in the Constitution (and, in some cases, even The Declaration) were violated with near completion.
At sentencing, I made the following statement to Judge Wigenton:
"I don’t come here today to ask for forgiveness. I’m here to tell this court, if it has any foresight at all, that it should be thinking about what it can do to make amends to me for the harm and the violence that has been inflicted upon my life."
It is time, now that the fraud and violence committed against me has been exposed by the appeals process, to begin making amends to me for the harm her court has done.
My current market-determined hourly rate is 1 Bitcoin an hour. I was taken from my childhood home at gunpoint on January 18th, 2011, and I was not allowed to freely exercise my liberties as a citizen until April 11th, 2014. That's 1179 days that you used my time that I am now billing you for (I gave you a discount by not including the last day). I am owed 28,296 Bitcoins. I do not accept United States dollars, as it is the preferred currency of criminal organizations such as the FBI, DOJ, ATF, and Federal Reserve and I do not assist criminal racketeering enterprises.
Know that all this wealth will be directed towards a good and charitable cause. I am building a series of memorial groves for the greatest patriots of our generation: Timothy McVeigh, Andrew Stack, and Marvin Heemeyer. You see, In the "Special Housing Unit", which is Bureau of Prisons codespeak for "solitary confinement" and "torture", I had enough time to think about the current state of federal government.
The federal government has declared war on We the People. I am but the latest casualty of the unjust and seditious war being waged against honest Americans and defenders of the Constitution. At Waco the FBI directed the murder of 76 men, women, and children. At Ruby Ridge the FBI murdered both a 14-year-old boy and a woman cradling her infant child. All federal agents are, in fact, murderous thugs and seditious terrorists. Sedition is the charge for crimes which undermine the Constitution with violence. I can assure you that violence was used against me, and the Third Circuit Court of Appeals has already verified that the case against me undermined the Constitution.
28,296 Bitcoins. This is my invoice. It will only come once. As government criminality continues to be exposed on a daily basis, there is an urgent question which our government must answer: by what civil and peaceful means can those of us harmed by government perjury, fraud, and violence be compensated for the losses we have experienced? My Bitcoin address: 1JTeYcsx37XTq5NRgjepAHDqaLHTZUL88a
Now the government's answer, or lack of it, will be permanently preserved in the Bitcoin block chain as a matter of public record. PAY ME MY MONEY, YOU LYING SUBHUMAN GARBAGE. You also should resign from your posts, as you've shown yourselves to be collective disgraces to rule of law and enemies of the United States Constitution. Those of us who actually love this country should take your places.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous puts Indonesia on notice over West Papua
The global activist network Anonymous has launched a campaign to raise attention on censorship and the killings of indigenous West Papuans in Indonesia's eastern region.
Anonymous, which is known for its activist stunts and disruptions to government and corporate websites, says West Papuans have been silenced for too long by Indonesia's military and government.
Anonymous also says the United Nations should take responsibility for the sham referendum it sanctioned in 1969 which incorporated the former Dutch New Guinea into Indonesia.
Indonesia denies that it censors media coverage of West Papua, and claims it is steadily bringing in development to improve the lives of people there.
However Indonesia's military insists it will continue to respond firmly to separatism.
Anonymous asks for a UN peacekeeping force, the withdrawal of all non-organic Indonesian troops in West Papua, and a free and fair referendum so Papuans can decide their own destiny.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Surf champ accused of hacking
An alleged Anonymous hacker accused of targeting the Indonesian Government and personal details of thousands of AAPT customers is a surf lifesaver and cancer support fundraiser living in a beachside property in Scarborough.
Adam John Bennett has appeared in Perth Magistrate's Court charged with hacking into the database of telecommunications company AAPT and obtaining sensitive information - including credit card and Medicare details, addresses and phone numbers.
As of this week, the 40-year-old was a fundraising manager for Cancer Support WA. He previously held a position as a company director with Paynes Find Gold Limited. In his spare time, Mr Bennett is an experienced surf lifesaver, prominent within the Scarboro Surf Life Saving Club, and a participant in national lifesaving championships.
Cancer Support WA was yesterday doing its own inquiries into the allegations.
"We are aware that a staff member, Adam Bennett, was charged on Thursday and that he is assisting with a Federal police investigation," it told _The Weekend West _. "We take the matter very seriously and are investigating internally."
Federal authorities will allege Mr Bennett, operating under the online pseudonym of "Lorax", hacked AAPT servers in 2012 and obtained more than 200,000 names and 100,000 email addresses.
He is also accused of compromising Indonesian Government web servers.
A teenage accomplice in NSW is accused of hacking into data belonging to the ACT Government and the Netspeed ISP based in Canberra.
After Government and Australian Communications and Media Authority investigations were launched into the security breaches, law enforcement agencies began a hunt for the two hackers associated with Anonymous.
In the past few days, the Scarborough property was raided and several hard drives were seized, which will take police months to analyse.
Mr Bennett did little to hide his social media profile, with his personal Twitter, LinkedIn and Facebook pages open for all to see. The online Anonymous persona Lorax is also one of the most open on the internet, hosting regular online radio broadcasts.
Part of Mr Bennett's bail conditions imposed by a Perth magistrate was that he not use the internet for any other purposes than for banking, employment and legal advice.
Lorax's last post on a Facebook page, entered last week, read: "Goodbye and thanks for all the fish!"
After the arrests, Tim Morris - the AFP's national manager high tech crime operations - said online attacks could have a big impact on government and business services.
"Hacking activities can affect everyone from small businesses right up to large government organisations," Assistant Commissioner Morris said.
"These acts can cause serious disruption to government and business networks, which in turn can be catastrophic for people who rely on these networks to run their small business or administer their entitlements or personal finances.
"The impairment or disruption of communications to or from computer networks is a criminal act, not harmless fun."
Mr Bennett is due to appear in court next month.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:On January 23, 2013 Brown was indicted once more on charges related to the raids on his apartment and his mother’s house. The FBI accused Barrett of “knowingly and corruptly conceal[ing] and attempt to conceal records, documents and digital data contained on two laptop computers”. His mother would later receive six months probation and a $1,000 fine for her role in hiding computers for her son.
At this point the lead prosecutor, Assistant United States Attorney Candina S. Heath, began working to convince Judge Sam Lindsay that Barrett Brown was attempting to manipulate the media while in prison. Recently unsealed court documents reveal the prosecution’s fears that Brown’s media connections would paint the government in an unfavorable light. Ms. Heath argued that silencing Brown’s attorney’s, Charles Swift and Ahmed Ghappou, was necessary to protect the jury, and Barrett himself, from being tainted by media portrayal of the case.
The transcript of the proceedings that led to the gag order reveal a fearful government attempting to silence a rising voice in independent media. The prosecution attempted to limit Barrett’s ability to write while in prison based on an article where “He is critical of the witnesses that will be called. He is critical of the government which has the tone, and I mentioned the tone of the article was problematic.” Ms. Heath claimed criticism of the government would affect the FBI agents she wanted to call as witnesses. Judge Lindsay did not buy the claim however. “I think at this point what you are saying, Ms. Heath, is too broad. I think it is overly broad, and I really do not think if I put something like that in the order that it would pass constitutional muster.”
Eventually the court would decide on a gag that forbid Brown or his attorneys from speaking to the media, but did allow Brown to write articles unrelated to the case and for the Free Barrett Brown organization to continue making statements regarding fundraising.
Another telling part of the unsealed documents relates to media connections Brown maintained. Ms. Heath told the court that after listening to recorded phone calls made from the county jail between Barrett Brown and Kevin Gallagher she worried more articles would be written about the case. Gallagher is the head of Free Barrett Brown. The prosecution discussed conversations between Brown and Gallagher where the two discuss journalists who may be interested in writing about the case. The documents mention Michael Hastings, Janet Reitman of Rolling Stone (listed as Jenna Wrightman), and Glenn Greenwald.
Het artikel gaat verder.quote:While Barrett Brown sits in prison awaiting sentencing on August 18 the implications of his trial are already being felt. What does it mean for journalists and activists who are arrested under false or exaggerated claims? Does having well known friends in the media, or being a journalist alone justify a gag order? Are we likely to see similar orders issued in the future? If one judge can be convinced that maintaining a media presence is tantamount to manipulating public opinion it is likely that others will follow suit.
Kevin Gallagher believes, The message sent by the DOJs gagging technique is clear. It says that in cases involving dissidents and political activists, not only will we listen to and transcribe all of your calls from jail and monitor all letters and communications, but we will drag family, friends and the media into the case, and try to prevent the defendant from defending theirself in the press.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:BiellaColeman twitterde op zaterdag 24-05-2014 om 12:28:48 In all my years studying Anonymous this case is the most troubling + puzzling: Hacker, Creeper, Soldier, Spy https://t.co/s5yH9j98xB reageer retweet
quote:
quote:MILTON, ONT., APRIL 2014 Guards at the Maplehurst Correctional Complex, a maximum-security jail near Toronto known to inmates as the Milton Hilton, came to rouse their newest prisoner from a concrete bed in the intake holding cells. Pulling back the hoodie covering his face, they found his T-shirt had been yanked up and twisted around his throat as a ligature.
The distraught prisoner was Matt DeHart, a 29-year-old American who had been brought to jail days earlier by a Canada Border Services Agency official and five police officers, who arrested him at the apartment he shares with his parents while fighting for refugee protection here.
Pulled from the cell and taken to hospital, he appeared to suffer no serious physical injury but underwent a mental health assessment. After returning to jail, Matt then dived headfirst from his bunk onto the concrete floor of his cell, requiring another urgent hospital visit. He told doctors he had crashed on purpose because he “had no hope.”
Days later, Matt appeared by video link at a detention review before a tribunal of Canada’s Immigration & Refugee Board (IRB). It took half an hour for jail guards to retrieve him from a one-to-one suicide watch cell and sit him in front of the camera. Matt peered into the lens. He looked dreadful: unshaven and unkempt, his eyes red and swollen, his lids heavy from medication. He squinted and grimaced.
It’s not that I’m not patriotic — I am. I voted for Bush. My family is military, pretty gung ho. But everything has changed.
— Matt DeHart
Gone was his bravado and the wide, almost goofy smile he seemed shy about flashing during many meetings with the National Post over the past eight months, while he was on bail from immigration detention on strict conditions. His father, Paul DeHart, a retired U.S. Air Force major who worked in the powerful National Security Agency, sat grim-faced, watching his son on the video monitor.
“We’re here on a claim of torture,” Paul said, his voice straining as he stated Matt has been diagnosed with post-traumatic stress disorder. “To visit your son in a maximum-security prison in a suicide smock … more heavily medicated than he’s ever been … For anyone with PTSD to be treated that way, much less your own child … is very disturbing.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Government Seeks Seven-Month Sentence for LulzSec Leader ‘Sabu’
As a reward for his extensive cooperation helping prosecutors hunt down his fellow hackers, the government is seeking time served for the long-awaited sentencing of top LulzSec leader Hector Xavier Monsegur, also known as “Sabu.”
After delaying his sentencing for nearly three years, the government has asked a federal court to sentence Monsegur to time served — just seven months — calling him an “extremely valuable and productive cooperator” in a document that details for the first time his extensive cooperation providing “unprecedented access to LulzSec.”
Monsegur, who has long been despised by members of LulzSec for his reported snitching, faced a possible sentence of between 259 and 317 months imprisonment under U.S. sentencing guidelines. But the U.S. Probation Office and prosecutors have asked for a reduced sentence “without regard to the otherwise applicable mandatory minimum sentence in this case” in a motion submitted to the U.S. District Court (.pdf) in the Southern District of New York on Friday.
A top leader of the hacking group LulzSec, Monsegur turned informant after he was secretly approached by authorities in June 2011, providing information that led to the subsequent arrest of other top members of LuzSec and Anonymous, including Jeremy Hammond, aka “Anarchaos”of Chicago, who was sentenced last year for his role in the hack of private intelligence firm, Stratfor.
The court document provides a timeline of events around Monsegur’s cooperation with authorities that many have suspected for years, including his efforts to draw fellow hackers into incriminating conversations.
Calling his cooperation “complex and sophisticated” the document describes, for example, his close involvement with law enforcement agencies in several jurisdictions to investigate Hammond in Chicago, while coordinating with FBI agents in New York, physical surveillance teams deployed in Chicago, and an electronic surveillance unit in Washington, D.C.
Hammond was sentenced last year to ten years in prison.
Monsegur, an unemployed father of two, formed LulzSec in the spring of 2011 with about five other core members, who went on a rampage over the next couple of months, targeting about 250 victims, including media outlets, government agencies and contractors, and private companies during their crime spree. Monsegur led the loosely organized group of hackers from his apartment in a public housing project in New York, working as a key player to analyzed victim web sites for vulnerabilities that could be exploited and providing other technical assistance.
The group, which also operated under the name Internet Feds, hacked a number of high-profile victims including HB Gary — a private intelligence firm that bragged it had identified members of Anonymous — the reality TV show “X-Factor,” PBS, Sony Pictures, Senate.gov, Nintendo, and a Georgia-based affiliate of the FBI’s Infragard organization.
Monsegur, as Sabu, was one of the most outspoken and brazen of the LulzSec crew before falling silent that summer, leaving behind a parting Tweet that quoted the The Usual Suspects film.
When he reappeared in September, many members of the anonymous hacking group suspected that Sabu had been arrested, since fellow hackers had outed him by publishing information about his identity online. Sabu denied at the time that he’d been snagged by the feds. But according to the government’s motion, his demise as leader of LulzSec was swift and painless and within hours after being interviewed by authorities, “he was back online cooperating proactively.”
According to the document, authorities approached Monsegur at his New York home on June 7, 2011 at which point he needed little convincing to cooperate. He quickly admitted guilt to criminal conduct before he was even charged with any crime and even spilled the beans to authorities about past crimes he had committed for which they had no knowledge of his role.
He admitted, for example, to participating in DDoS attacks against PayPal, MasterCard, and Visa, which were targeted after the companies blocked donations to WikiLeaks. Monsegur also admitted to hacking thousands of computers between 1999 and 2004, engaging in various hacktivism activities as well as carding activity — stealing and selling credit card information for financial gain or to pay off his own bills. He also admitting to selling marijuana, illegally possessing an unlicensed firearm, and purchasing stolen electronics and jewelry.
“Monsegur admitted his criminal conduct and immediately agreed to cooperate with law enforcement,” the document notes. “That night, Monsegur reviewed his computer files with FBI agents and provided actionable information to law enforcement. The next morning, Monsegur appeared in court on a criminal complaint charging him with credit card fraud and identity theft, and was released on bail, whereupon he immediately continued his cooperation with the Government, as described further below.”
Monsegur entered a guilty plea to the court on August 15, 2011, for an indictment charging him with twelve counts in New York, including nine counts related to computer hacking; one count related to credit card fraud; one count of conspiring to commit bank fraud; and one count of aggravated identity theft. The plea resolved four other cases filed against him in the Eastern and Central Districts of California, the Northern District of Georgia, and the Eastern District of Virginia).
But Monsegur apparently violated the terms of his agreement in 2012. According to the document, in May 2012, his bail was revoked over “unauthorized online postings” he made, and he was arrested on May 25th, before being released on a revised bail December 18, 2012. Monsegur has been free since that time, while cooperating with authorities, and has spent only a total of seven months in prison since 2011.
In court records, Monsegur was generally identified only as CW-1 and was praised extensively (.pdf) for “actively cooperating with the government.” Authorities in fact petitioned the court several times to delay Monsegur’s sentencing during his continued cooperation.
According to authorities, part of Monsegur’s post-arrest cooperation included providing information to help repair hacked systems belonging to PBS and Senate.gov. He also provided authorities with information about hacks involving servers belonging to the Irish political party Fine Gael and the Sony Playstation Network.
But his most extensive assistance led to the arrest of fellow LulzSec members, including Ryan Ackroyd, aka “Kayla” of Doncaster, United Kingdom; Jake Davis, aka “Topiary” of London; Darren Martyn, aka “pwnsauce” of Ireland; Donncha O’Cearrbhail, aka “palladium” of Ireland; Mustafa Al-Bassam, aka “T-Flow” in the UK; as well as Hammond, Ryan Cleary and Matthew Keys, a former Reuters employee accused of inciting members of Anonymous to hack one of his former employers.
Monsegur provided “crucial, detailed information regarding computer intrusions committed by these groups, including how the attacks occurred, which members were involved, and how the computer systems were exploited once breached,” the government reveals.
This assistance “contributed directly to the identification, prosecution and conviction of eight of his major co-conspirators, including Hammond, who at the time of his arrest was the FBI’s number one cybercriminal target in the world. On top of that, Monsegur engaged in additional, substantial proactive cooperation that enabled the FBI to prevent a substantial number of planned cyber attacks,” the government noted.
Working at the direction of law enforcement for three years, sometimes into the late evening and early morning, Monsegur drew his fellow hackers into online chats designed to confirming their identities and whereabouts.
“During some of the online chats, at the direction of law enforcement, Monsegur convinced LulzSec members to provide him digital evidence of the hacking activities they claimed to have previously engaged in, such as logs regarding particular criminal hacks,” the government notes. “When law enforcement later searched the computers of particular LulzSec members, they discovered copies of the same electronic evidence on the individuals’ computers. In this way, the online nicknames of LulzSec members were definitively linked to their true identities, providing powerful proof of their guilt.
“Other times, at the direction of law enforcement, Monsegur asked seemingly innocuous questions designed to elicit information from his co-conspirators that, when coupled with other information obtained during the investigation, could be used to pinpoint their exact locations and identities,” the document reveals.
Ackroyd has been sentenced to 30 months in prison; Davis was sentenced to two years in a juvenile detention facility; Al-Bassam was sentenced to 20 months, which was suspended for two years; Martyn and O’Cearrbhail received probation and a fine; Cleary was sentenced to 32 months in prison; the case of Keys is pending.
Monsegur also helped “disrupt or prevent at least 300 separate computer hacks” that authorities say targeted U.S. Armed Forces, Congress, unidentified U.S. courts, NASA, and a number of private companies.
“Although difficult to quantify, it is likely that Monsegur’s actions prevented at least millions of dollars in loss to these victims,” the government states effusively. “Monsegur also provided information about vulnerabilities in critical infrastructure, including at a water utility for an American city, and a foreign energy company. Law enforcement used the information Monsegur provided to secure the water utility, and the information about the energy company was shared with appropriate government personnel.”
The government notes that because Monsegur’s cooperation was publicly exposed shortly after his arrest, he and his family faced severe threats, causing authorities to relocate him and some of his family members.
“Monsegur repeatedly was approached on the street and threatened or menaced about his cooperation once it became publicly known,” prosecutors note. “Monsegur was also harassed by individuals who incorrectly concluded that he participated in the Government’s prosecution of the operators of the Silk Road website.”
In one case, a reporter had to be removed from the school where the journalist had sought to interview children for whom Monsegur served as guardian.
Monsegur’s sentencing is set for May 27.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:wikileaks twitterde op zondag 25-05-2014 om 01:58:50 Page 11 of "#Sabu" sentencing doc contains apparent reference to FBI operation against WL http://t.co/9eCiFxStK1 See http://t.co/Ex6qZMkKgf reageer retweet
quote:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:Edpilkington twitterde op dinsdag 27-05-2014 om 17:54:53 Judge at "Sabu" hacker informant sentencing "salutes" his "extraordinary cooperation" with FBI - lets him walk with time served reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


http://resetthenet.tumblr.com/quote:Join us on June 5th to Reset the Net
The NSA has corrupted the Internet. On June 5, we will Reset the Net. We hope you’ll join us.
June 5 is the one-year anniversary of the first documents leaked by Edward Snowden. While EFF has been fighting NSA surveillance for years, 2013 marked a new chapter in our battle against mass spying. The documents made it clear to everyone why we care so much, and why they should too.
Surveillance affects everyone, in the United States and internationally. Millions of innocent people have had their communications swept up by the NSA’s dragnet surveillance. Thomas Drake, former NSA official and whistleblower described recently retired NSA chief General Keith Alexander’s surveillance philosophy: “He is absolutely obsessed and completely driven to take it all, whenever possible.” This philosophy clearly underpinned his nearly nine year tenure at the NSA. In addition to this collect-it-all strategy, the NSA has used tactics such as deploying malware, trying to weaken encryption, and other sophisticated techniques that make the Internet less secure.
Mass surveillance is toxic for the Internet. The Internet is a powerful force that can promote democracy, innovation, and creativity, but it’s being subverted as a tool for government spying.
That’s why EFF has joined with dozens of other organizations in calling for a day of action to Reset the Net. On June 5th, Reset the Net is asking everyone to help by installing free software tools that are designed to protect your privacy on a computer or a mobile device. Reset the Net is also calling on websites and developers to add surveillance resistant features, like HTTPS and forward secrecy.
Don’t wait for your privacy and freedom. Start taking it back.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Japan’s Government Party LDP Sponsored and Cultivated the Right Wing in Underground Anonymous 2channel Board
In Japan, there is a massive discussion board with 230 million page views per day called 2channel. It has played an important role on the Japanese internet for 15 years. It is an anonymous textboard, attracting the most Net traffic in the country.
Since Feb 19 2014, however, a conflict between Hiroyuki Nishimura ( the founder of 2channel and, until recently, its manager ) and his business partner Jim Watkins (an ex-U.S Army commander ) regarding its administration and ownership suddenly became clear. Consequently, Mr Watkins secured the domain name, administrative rights and everything by exploiting his status as a 2channel administrator. He then expelled Nishimura from the site, and now maintains it himself.
Through this internal strife, the existence of a paid service to delete postings of 2channel was uncovered on April 2, by a sudden announcement from Hiroyuki’s business partner, Mr Uchiyama, Hotlink, Inc‘s president .
Mr. Uchiyama’s company, Hotlink, has been tied up with 2channel in an exclusive contract, and offered to monitor and delete negative threads and comments about its customers. And it was detected that among its customers was listed Japan’s ruling government party, the LDP. This information was uncovered by anonymous 2channel users. In fact, this privileged access to delete opinions was not widely known by internet users, and caused considerable alarm.
This service is, though its overall figure is unknown, thought to have administrative access rights to 2channel:
(From a company press release. after the Merger and Acquisition Process, Hotlink is now a member of this ”Net Defamation Basters” team.)
Further, according to Hotlink, the data is supplied exclusively from 2 channel. Since anyone can see 2channel’s posts freely, one question that occurs is ”What kind of data did the ex-administrators sell?” They may have included personal data Hiroyuki collected without the permission or knowledge of users. This suspicion is corroborated by a 2013 scandal where personal information of 40,000 2channel customers was leaked; administrators recorded the user name, address, phone number, post logs, credit card number and security code, all without the users' consent. For what purpose did they collect all this personal data unless it was to sell it?)
Among several shady channels, Hotlink’s customers included Japan’s ruling government party, the LDP, alongside several business giants. And as for official announcements stated below, the LDP used the service offered by Hotlink in the 2013 House of Councillors election.
Then, the contracts and money goes from LDP to Hotlink and then to the Hiroyuki-owned 2channel. Therefore, the sponsor of 2channel is, in reality, Japan’s Government Party LDP. Those disclosures were shocking because, according to its own official announcement, 2channel is a discussion board with no commercial interest. Administration is done by unpaid volunteers, and everybody was told that the highest value of the board was nothing but FREE SPEECH.
Suspicion about this tie-up with Hotlink goes even further; how far did the scope of their services go? One serious issue is whether or not Hiroyuki gave a privileged deal to the Government Party LDP. Hotlink officially boasts they can control and ”extinguish the fire” of harsh criticism in internet communities.
If so, had they abused the data from 2channel administrators in order to stop the spread of information or opinions that the Japanese government disliked on 2 channel? Also, in some 2channel boards, administrators have special access to permit or deny the creation of threads. Those with an agenda on 2channel could have intentionally dismissed the creation of topics, or arbitrarily deleted comments or threads which Japanese Government Party LDP did not want to allow discussion of. So, the LDP sponsored Hiroyuki may have manipulated the opinions of a self-professed "independent discussion board".
This hypothesis is not as absurd as it may have sounded a few years ago. As the Wall Street Journal pointed out, it is widely recognized that Japan has seen a recent increase in Right Wing thought. And this tendency has been stronger on 2channel, where hate speech is particularly prevalent. Also, anti-nuclear activists or politicians (like Naoto Kan, Mizuho Fukushima, Junichiro Koizumi) were fiercely defamed. But now, strangely, the attacks against those figures suddenly ceased since the LDP-linked Hiroyuki lost his administrative rights on 2channel.
This is the 1st page of Google results when you google ” South Korea history ” in Japanese. Most of the results are nationalistic hate speech towards South Korea. They are 2channel and affiliate sites led by Hiroyuki and his business partners. Also, Google’s 1st suggestion when you enter ”South Korea history” is ” South Korea history fabrication”.
Propaganda activity on the internet is not exclusive to Japan. Mr. Edward Snowden taught us that:
(Documents from the article released by Mr Glenn Greenwald)
In my observation, many governments are obsessed with penetrating and controlling internet discussion secretly. Now, 2channel is completely ”occupied” by ex U.S. Army officer Mr. Jim Watkins.
Both 2channel and Social Media may not be the perfect egalitarian forums for discourse that netizens once thought. However, we have to face and understand that fact in order to make rules and institutions on the internet.
[Takanori Eto]
Translated and mirrored from http://echo-news.net/en/l(...)ymous-2channel-board with permission
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:Falkvinge twitterde op zaterdag 31-05-2014 om 20:34:26 According to Swedish oldmedia, Peter Sunde (@brokep) was just arrested by police, having formally been a fugitive since the TPB pretendtrial reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous dreigt met cyberaanval op WK-sponsors
Het hackerscollectief Anonymous heeft gedreigd een cyberaanval te willen plegen op de sponsors van het Wereldkampioenschap voetbal in BraziliŰ. Bedrijven zoals Adidas, Emirates Airlines, Coca-Cola en Budweiser moeten vrezen voor hun websites, zo meldt Reuters.
Het WK voetbal dat op 12 juni in SŃo Paulo van start gaat, kon al op heel wat verzet rekenen. Demonstranten protesteren tegen de Braziliaanse overheid die miljarden dollars aan het sportevenement uitgeeft, terwijl het Zuid-Amerikaanse land aan armoede ten onder gaat.
De actievoerders hebben nu een nieuwe bondgenoot. Anonymous liet aan Reuters weten de belangrijkste sponsors van het WK onder de loep te nemen. 'We zijn nagegaan welke sites het meest kwetsbaar zijn en hebben al een plan opgesteld.' De bewuste bedrijven willen niet reageren op de bedreiging.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Hello crypto-lovers. Letten we even op?
quote:Bombshell TrueCrypt advisory: Backdoor? Hack? Hoax? None of the above?
A sampling of theories behind Wednesday's notice that TrueCrypt is unsafe to use.
quote:Wednesday's bombshell advisory declaring TrueCrypt unsafe to use touched off a tsunami of comments on Ars, Twitter, and elsewhere. At times, the armchair pundits sounded like characters in Oliver Stone's 1991 movie JFK, as they speculated wildly—and contradictorily—about what was behind a notice that left so many more questions than answers. Here are some of the more common theories, along with facts that either support or challenge their accuracy.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:TrueCrypt krijgt doorstart
Enkele Zwitserse activisten van de Piratenpartij werken aan een doorstart van de bekende encryptiesoftware TrueCrypt, die deze week offline ging.
De mysterieuze ontwikkelaars van TrueCrypt trokken eerder deze week de stekker uit het project. Ook waarschuwden ze dat het programma onveilig zou zijn. Ze raadden gebruikers aan te migreren naar Bitlocker. Op de originele TrueCrypt-site staat nog slechts TrueCrypt 7.2, waarmee het alleen mogelijk is om versleutelde TrueCrypt-bestanden te decrypten.
Zwitsers Thomas Bruderer en Joseph Doekbrijder, ex-president en ex-vicepresident van de Zwitserse Piratenpartij, zijn nu TrueCrypt.ch gestart als een soort doorstart. De laatste werkende versie, TrueCrypt 7.1a, is door de Zwitsers weer online gebracht, hoewel zij ook waarschuwen voor mogelijke beveiligingsproblemen.
Fork
De Zwitsers willen met hun project meewerken aan een 'fork', een afsplitsing van het originele TrueCrypt. Die zou waarschijnlijk wel een andere naam krijgen. De huidige ontwikkelaars van TrueCrypt zijn onbekend. Dat zou volgens de Zwitsers voor hun fork juist niet moeten gelden.
De Zwitsers wachten voor de fork op de uitkomst van het
Crypto Open Audit-project. Het onderzoek is nog maar gedeeltelijk afgerond.
Oproep voor hulp
De Zwitsers doen ook een oproep voor mensen die willen helpen om beveiligingsrisico's in kaart te brengen. Ook wordt gezocht naar experts die kunnen helpen om juridische problemen op te lossen. Met de hosting in Zwitserland zou de juridische dreiging al minder zijn.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Reddit, Imgur and Boing Boing launch anti-NSA-surveillance campaign
The Reset the Net campaign aims to encourage direct action, urging visitors to install privacy and encryption tools
Some of the world's largest websites are planning a coordinated day of action on Thursday to oppose mass surveillance online.
The sites, which include Reddit, Imgur and BoingBoing, will be taking part in the campaign, called "Reset the Net", in a number of ways.
Some will showing a splash screen to all users, reminiscent of the one used in the successful protests against SOPA, the US copyright bill which many feared would damage the backbone of the internet. But rather than telling users to write to their electoral representatives, this protest will push more direct action, encouraging visitors to install privacy and encryption tools.
Other sites have committed to improving their own privacy as part of the campaign, by enabling standards such as HTTPS, which prevents attackers from eavesdropping on visitors. Such security standards are common in the world of ecommerce, but rarer for sites which don't think of themselves as holding sensitive information.
"We can take back control of our personal and private data one website, one device, one internet user at a time," said Reddit's General Manager Erik Martin. "We’re proud to stand up for our users’ rights and help Reset the Net."
The campaign is being co-ordinated by Fight for the Future, whose co-founder Tiffiniy Cheng said "Now that we know how mass surveillance works, we know how to stop it. That’s why people all over the world are going to work together to use encryption everywhere and make it too hard for any government to conduct mass surveillance.
"There are moments in history where people and organisations must choose whether to stand on the side of freedom or tyranny. On June 5th, the internet will show which side it’s on.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Agriculture Giant Monsanto Hacked
Monsanto says March breach saw some financial data compromised
Agriculture provider Monsanto has admitted to a breach of its servers, affecting 1300 farmers, with some credit card information leaked.
A letter dated 14 May from the company’s Precision Planting unit to the Office of the Attorney General in Baltimore warned that a number of citizens in the area had been affected by the breach.
Monsanto breached
The breach was detected on 27 March, when Monsanto uncovered unauthorised access to its systems from an outside party, who compromised files on the affected servers with personal information, including customer names, addresses, tax identification numbers, social security numbers and in some cases financial account information.
Some human resources data was stored on the servers too, including tax forms that contained employee names, addresses and social security numbers and some driver’s license numbers.
“We believe this unauthorized access was not an attempt to steal customer information; however, it is possible that files containing personal information may have been accessed and therefore we are making this notification,” said Reuben Shelton, senior counsel for Monsanto, in the letter.
“The incident has been contained and we have partnered with a leading forensics firm to understand and remediate this issue. In addition, we have asked the Federal Bureau of Investigation for assistance.
“We are not aware of any misuse of any information from this incident, but we are notifying all of the affected individuals and providing them with free one-year membership of credit monitoring and identity theft insurance.”
On 24 May, an Anonymous group called Operation Green Rights claimed it had attacked Monsanto and a range of other firms in an effort to shine a light on what it called the “polluting and contaminating” of natural resources.
Later in the month, the group said: “ We have found many confidential documents within an account of a former Monsanto employee.
“Therefore, we are following up by obtaining archives from two other Monsanto subsidiaries and are investigating further.”
It has not yet taken credit for the March breach. An Anonymous group claimed to have hacked Monsanto in 2011.
Protests against Monsanto were held last month too, as demonstrators sought to express their anger over alleged aggressive business practices and their dislike of genetically modified crops.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:#OpWorldCup: Brazil Government websites hacked by DK Brazil Hackteam
An anonymous affiliated hacker group called as "DK Brazil Hackteam & An0nнat" targeting Brazil government and defaced several Brazil Government websites in recent days.
The hack is part of an ongoing operation called "#OpWorldCup" which. The operation is appeared to be a protest against the upcoming 2014 FIFA World Cup that is scheduled to take place in Brazil.
The group has defaced two Brazil government websites www.saobento.ma.gov.br and Brazil's Barro Municipality (barro.ce.gov.br/).
The group has defaced plenty of Brazil Government sites at the end of last month. They hacked the following the websites so far: www.novaluzitania.sp.gov.br/, indaial.sc.gov.br/, igarapedomeio.ma.gov.br/, procon.sp.gov.br.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Why Anonymous threats should not be ignored
International hacktivist group Anonymous is causing fear within the business and technology community once again, after a supposed Anonymous spokesperson warned that World Cup sponsors are next on the hit list.
In an interview with Reuters, a masked hacker going by the name of Che Commodore revealed that preparations have already begun for a full-scale cyber-attack on sponsors such as Coca Cola, Budweiser, Emirates Airlines and Adidas.
The hacktivist group, which claims to use cyber-attacks as a method to target social injustice, has been known to target high profile networks in the past, generally relying on DDoS attacks as the weapon of choice. Last year Google Malaysia was targeted by hacktivists who spread the message "Google Malaysia STAMPED by PAKISTANI LEETS”. Similarly, the New York Times website was taken offline by an attack leaving readers unable to access content for several hours.
This time the Anonymous is said to be angry at the Brazilian government for their decision to host the World Cup at the expense of millions, despite the poor social standards of many Brazilian citizens. As previous threats from the hacktivist group have proven to be real, corporations and international governments alike must treat this latest threat with the severity it deserves.
What is most worrying is that Anonymous may have already laid the groundwork of its malicious attack and any organization that hasn’t taken the necessary steps to protect against stealth attacks, could be at serious risk. Che Commodore has already sinisterly claimed to be searching for the back doors into the network having “conducted late-night tests to see which of the sites are more vulnerable.”
Such attacks as those previously carried by Anonymous usually rely on Advanced Evasion Techniques (AETs) to exploit vulnerabilities in network gateways and allow Advanced Persistent Threats (APT) to be delivered. Unless measures have been taken to detect these evasion techniques, it is likely an APT could already have penetrated deep into the network of any organisation targeted by Anonymous.
AETs are methods of disguise used to target networks undetected and deliver malicious payloads. Often, AETs take advantage of rarely used protocol properties in unexpected combinations. Using AETs, an attacker can split apart an exploit into pieces and bypass traditional security methods such as a firewall or IPS appliance. Once inside the network, the attacker can then reassemble the code to unleash malware and continue APT attack.
Most IPS and firewalls are not capable of detecting AETs, as while many can pass industry tests with high ratings, those ratings are based on protection against a limited number of threats. Although the exact number of AETs is unknown, it is close to hundreds of millions – many of which are not covered by standard firewalls. As such, the stealth-like presence of AETs means that they can go undetected on a network for weeks, or even months, at a time.
In a recent study by McAfee, it was uncovered that on average, those who experienced a security breach in the last 12 months reported a cost to their organization of over ú600,000, which of course doesn’t taken into account reputational damage As such, those threatened by Anonymous must act fast.
If AETs have been used by the hacktivist group, those targeted by Anonymous may already be compromised. The trap may already be set, with malware lying dormant on organizations' networks, ready to attack. It is therefore important that these brands take serious measures to identify such threats and remove them as soon as possible, before Anonymous has a chance to strike.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Hackers face life sentences in Britain
To reflect the damage they might cause.
Tough new penalties for computer hackers who jeopardise national security may come into effect in Britain under measures introduced in the Queen's Speech overnight.
The UK Government wants life sentences to be imposed on hackers that sabotage computer networks and cause deadly civil unrest through cutting off food distribution, telecommunications networks or energy supplies, under a new Serious Crime Bill.
The UK government will seek to amend the 1990 Computer Misuse Act "to ensure sentences for attacks on computer systems fully reflect the damage they cause."
Currently, the law provides for a maximum sentence of ten years' imprisonment for those who commit the offence of impairing a computer. A new, aggravated offence of unauthorised access to a computer will be introduced into the Computer Misuse Act by the government, carrying far longer sentences.
A hack that causes deaths, serious illness or injury, or is found to seriously damage Britain's national security will be punished by life in prison under the proposed new law.
Environmental damage, or serious hurt to the economy through hacking could land offenders with a fourteen year stretch in gaol if the government gets its way.
As of today, Britain has suffered no such serious cyber attacks. The UK government's National Security Strategy [PDF] nonetheless puts hacking on par with terrorists incidents, international miltiary crises and major accidents or natural hazards, as the country's highest priority risk.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:In early 2012, members of the hacking collective Anonymous carried out a series of cyber attacks on government and corporate websites in Brazil. They did so under the direction of a hacker who, unbeknownst to them, was wearing another hat: helping the Federal Bureau of Investigation carry out one of its biggest cybercrime investigations to date.
A year after leaked files exposed the National Security Agency's efforts to spy on citizens and companies in Brazil, previously unpublished chat logs obtained by Motherboard reveal that while under the FBI's supervision, Hector Xavier Monsegur, widely known by his online persona, "Sabu," facilitated attacks that affected Brazilian websites.
The operation raises questions about how the FBI uses global internet vulnerabilities during cybercrime investigations, how it works with informants, and how it shares information with other police and intelligence agencies.
After his arrest in mid-2011, Monsegur continued to organize cyber attacks while working for the FBI. According to documents and interviews, Monsegur passed targets and exploits to hackers to disrupt government and corporate servers in Brazil and several other countries.
Details about his work as a federal informant have been kept mostly secret, aired only in closed-door hearings and in redacted documents that include chat logs between Monsegur and other hackers. The chat logs remain under seal due to a protective order upheld in court, but in April, they and other court documents were obtained by journalists at Motherboard and the Daily Dot.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Hundreds sign up to protest outside GCHQ in Cheltenham
Hundreds of people have signed up to protest against Cheltenham-based listening post GCHQ.
The event, organised on social media site Facebook, aims to say “enough is enough” to the organisation following the Edward Snowden leaks.
Running from August 29 to September 1, it is organised by the group Anonymous.
A statement on the page said: “With all the latest leaks coming out about the power of GCHQ, the NSA and Five Eyes it is high time that we showed our faces and said enough is enough.”
A GCHQ spokes person said: "People have a right to protest peacefully within the law.
"All of GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight, including from the Secretary of State, the Interception and Intelligence Services Commissioners and the Parliamentary Intelligence and Security Committee. All our operational processes rigorously support this position."
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:#OpHackingCup_
=======================================================================================================================================
:00 - The Motivation_
--------------------------------------------------------------------------------------------------------------------------------------
:00:00 ::
Hello, citizens of the world; we are Anonymous.
As time for World Cup approaches, we have witnessed a crescent frequency of hacking attacks for the Anonymous ideal. Only for the last week there were two invasions with big repercussion on the media, one that was the leaking of Itamaraty Palace documents - central to the Ministry of External Relations. Among these papers, the most are considerate sigilous.
We'd like to clarify for what reasons cyberactivists act in these ways.
How many billions of dollars from public funds were spent to build and reform the stadiums that will host the Cup, aside other builds that will bring very little or no legacy to the population. What does justify, for example, to build a new stadium at Manaus city, at state of Amazonas? In which ways were executed the fiscalization of how the public money is being used on these builds, principally the ones that need to be finished in matter of urgency due to delays - many times resulted by increase of costs (it's estimated that the cost of the stadiums have increased 163% compared to the initial prevision). It is valid to remember that the promess included the private initiative would take the outgoing of building the stadiums.
We can't accept pacifically any more the violations on people's basic rights practised because of this event. For preparation we can understand: 1. hygienization and elitization of the cities, denominated to it for, above all, the property speculation and for the violence against the local population on scale of streets occupying the big centers;
2. unjustifiable outlay to intensify the security (and the repression) against the manifestations that may happen during the games, allied to draft laws which marginalize and criminalize the manifestants;
3. to guarantee that no one - except for the locals and people with tickets - approach the stadiums on game days, aside the non-authorized vendors won't be allowed to open certain hours before and after the games, even that for this the freedom of come and go be limited, forbidding things like visits to the local people, among other situations.
The on-line actions, just as the protests on the streets, are part of a resistance against this model that has become so evident to ordain and dis ordain of this mega corporation which is FIFA on this country, against the influence of economic power on political decisions and against polarization of the profit counterpointing the basic right of a whole population, and, therefore, are legitimate.
"There is no fairness on following unfair laws", said Aaron Swarz, infamous programmer and fighter for a free internet.
About the cybernetic security on Brazil:
Right after the leaks Edward Snowden revealed - National Security Agency (N.S.A.) ex-functionary, - department which would be monitoring the Brazilian government, which got to a Inquiry Parliamentary Commission (aka C.P.I.) to be opened to investigate the case, which is already closed, with the most obvious conclusion: there is vulnerability in the whole cybernetic governmental system, clearly for lack of investment. The C.D. Cyber (Center of Army's Cybernetic Defense), responsible for Brazilian cybernetic security have had their amount cut for years: about forty nine and half millions of dollars in the year of twenty-twelve, forty millions last year and thirty-one millions in this very year, even after Snowden's leaks.
The eyes of the world will be turned to Brazil: we will show to everyone how fake is and always was this Brazilian government and FIFA.
=======================================================================================================================================
:01 - The Communication_
--------------------------------------------------------------------------------------------------------------------------------------
:01.00 :: Twitter Account @AnonBRNews
=======================================================================================================================================
:02 - The Targets_
--------------------------------------------------------------------------------------------------------------------------------------
:02:00 :: The Tweets indicating the targets will start at 2014-06-11T14:00:00Z;
=======================================================================================================================================
We are Anonymous
We are Legion
We do not forgive
We do not forget
Expect us
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Het artikel gaat verder.quote:Anonymous Denmark targets Socialist Party (SF) for signing mass surveillance bill
The online hacktivist Anonymous has target Denmark’s political party (Socialistisk Folkeparti, SF in Danish language) for signing and passing mass Internet surveillance bill from the parliament yesterday.
Despite criticism from experts and human right organizations, the Danish parliament approved bill that will allow government to keep track of user’s activity on the Internet. This has been done through an approval of the controversial bill on the Center for Cyber Security.
Anonymous Denmark seems unhappy with the surveillance bill and decided to leak confidential information of officials at Socialistisk Folkeparti, SF party. Anonymous left a brief message on Pastebin along with personal details of 22 officials and database of SF party’s official website.
The leaked data contains names, emails, encrypted passwords, social security numbers, addresses, city and zip codes. While the message states that:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


SPOILEROm spoilers te kunnen lezen moet je zijn ingelogd. Je moet je daarvoor eerst gratis Registreren. Ook kun je spoilers niet lezen als je een ban hebt.Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous hackers bring down websites just hours before kick-off
HACKERS have targeted a number of World Cup-related websites in a large scale cyber attack ahead of the tournament opener.
Well known group Anonymous, who have brought down the US defence website, Amazon and other large websites in the past, are purposefully disrupting the sites to send a message to the Brazilian government.
The cyber attackers are using a system called DDos, Distributed Denial of Service , which forces websites to crash by sending high levels of traffic.
Hackers at Anonymous Brazil say they want the government to respect the people's needs.
One of those involved, known as Che Commodore, said: "Companies and institutions that work with a government that deny the basic rights of its people in order to promote a private, exclusive and corrupt sports event will be targeted.
"We had a busy last few days and there is more still to come."
The World Cup has become hugely unpopular in the country.
Expensive security measures, brand new stadiums and poor transport options have caused uproar among workers and residents close to World Cup sites.
Brazilians have called for much more organisation and planning from the government in the future.
In reaction, the hackers have targeted government websites and intelligence agencies.
There are said to be 27 websites linked to government activity that have been brought down by Anonymous, one of which is the Matto Grosso state site.
A spokeswoman for the local government said: "Our site was hacked.
"We were able to take it off the air and restore the service within 30 minutes."
Sites belonging to the Sao Paulo police, the Sao Paulo Metro (where workers are striking) and the Brazilian Football Confederation.
The names are included on a long list but some companies and bodies have denied being hacked.
Last month, it is believed Anonymous hackers infiltrated the foreign ministry's email service.
They were able to see dozens of classified documents including a list of foreign leaders planning to attend World Cup matches.
Computer experts are now warning it may be too late with many sites already infected.
William Beer, a cyber security analyst said: "Even though people are starting to realize there are problems, a lot of sites have probably already been attacked and are infected."
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Hackers Warn Of Cyber Attacks On Oil Companies In Saudi, UAE, Qatar
The threat has been issued by Anonymous, a politically motivated group of hacktivists, according to Symantec.
A Middle East-based group of hackers has issued a threat warning of cyber attacks against oil, gas and energy companies in the Middle East, security firm Symantec has revealed.
The threat, made by Anonymous, a politically motivated group of hacktivists, states that they are planning to attack before, during, and after June 20, 2014.
This is due to Anonymous disagreeing with the US dollar being used as the currency to buy and sell oil, Symantec said.
According to the security firm, governments that may be attacked include those in Saudi Arabia Kuwait and Qatar.
Some of the possible company targets include Kuwait Oil Company, Petroleum Development Oman, Qatar Petroleum, Saudi Aramco, ADNOC, ENOC and Bahrain Petroleum Company.
While there are limited details regarding the tools that will be used, based on previous observations, Symantec said the attacks will most likely include distributed denial of service (DDoS) attacks, phishing/spear-phishing emails, intrusion and data-theft attempts, vulnerable software exploration, web application exploits, and website defacement.
“Public announcements by these groups are often used as a means to gain notoriety or media attention and can be of highly volatile credibility,” the company said.
The Middle East’s petrochemical industry has been vulnerable to cyber attacks over the last few years, and Saudi Aramco, the world’s biggest oil producer, was hit by a major virus infection in August 2012.
Security experts have warned that the region is not well-prepared to deal with cyber crime and is susceptible to attacks.
Symantec said it has detection measures in place regarding the recent threat and also issued the following recommendations:
Ě Use a layered approach to securing your environment, including enterprise-wide security monitoring.
Ě Deploy network intrusion detection/prevention systems to monitor network traffic for malicious activity.
Ě Ensure all operating systems and public facing machines have the latest versions and security patches, and antivirus software and definitions up to date.
Ě Ensure all web servers are patched, configured to minimise the impact of DoS/DDoS attacks, and hardened against external threats.
Ě Utilise web application firewalls as a front-line defense against attacks.
Ě Ensure your IT and IT security staff are prepared and know what they need to do in the event of attack.
Ě Discuss DoS/DDoS mitigation strategies with your upstream provider and ensure they are aware of this threat.
Ě Ensure relevant third party vendors are also aware and accessible.
Ě Utilise DDoS protection services.
Ě For technologies not monitored/managed by MSS, ensure all signatures are up to date, including endpoint technologies.
Ě Ensure systems have a running firewall, unnecessary ports are closed/blocked, and unused services are disabled.
Ě To reduce the impact of latent vulnerabilities, always run non-administrative software as an unprivileged user with minimal access rights.
Ě Do not follow links or open email attachments provided by unknown or untrusted sources.
Ě Ensure staff is educated on social engineering and phishing techniques
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Massive security flaws allowed for Stratfor hack, leaked report reveals
The intelligence firm at the center of a notorious cybersecurity breach that affected top government officials failed to institute standard security measures prior to the attack, according to a newly leaked report.
In December 2011, a group of skilled hackers broke into the network of Strategic Forecasting, Inc. (Stratfor), compromising the personal data of some 860,000 customers, including a former U.S. vice president, CIA director, and secretary of state, among others.
The hackers, known collectively as AntiSec, exfiltrated approximately 60,000 credit card numbers and associated data, resulting in a reported $700,000 in fraudulent charges. Roughly 5 million internal emails were obtained by the hackers and later released by the whistleblower organization WikiLeaks as the "Global Intelligence Files."
For Stratfor, a Texas-based geopolitical intelligence and consulting firm, the incident was an international embarrassment that caused roughly $3.78 million in total damages—and all of it could’ve been avoided by meeting common fraud prevention requirements.
Based on confidential internal documents obtained by the Daily Dot and Motherboard, Stratfor employed substandard cybersecurity prior to the infiltration that left thousands of customers vulnerable to potential identity theft. The documents also lend credibility to statements made by Hyrriiya, a relatively unknown hacker who claimed responsibility for the breach.
The Daily Dot–Motherboard investigation is based on a cache of sealed court documents—roughly 3 gigabytes of previously unseen chat logs, warrants, and various government reports—some of which was collected by Hector “Sabu” Monsegur, a hacker-turned-informant. Evidence provided by Monsegur was used to convict eight members of Anonymous, including Jeremy Hammond, who is currently serving the remainder of a 10-year sentence for his role in the attack.
According to the documents, Stratfor engaged Verizon Business/Cybertrust to “conduct a forensic investigation” into the breach on Dec. 30, 2011, and requested that findings be shared with the Federal Bureau of Investigation. Verizon's security team inspected the computers at Stratfor's office shortly after the attack, as well as servers later confiscated by federal agents from CoreNAP, an Austin-based data center that hosted Stratfor's customer information.
In a 66-page report filed Feb. 15, 2012, Verizon concludes in painful detail that Stratfor had insufficient control over remote access to vital systems, and that those systems were not protected by a firewall and lacked proper file integrity-monitoring. (Editors’ note: The full report can be viewed below. Only Internet protocol addresses and private customer information have been redacted.)
"In light of a confirmed system breach,” Verizon reports, “it should be noted that several distinct vulnerabilities and network configurations existed that allowed this breach and subsequent data compromise to occur.”
For starters, at the time of the attack, no password management policy existed within Stratfor. Passwords were at times shared between employees, and nothing prevented the same passwords from being used on multiple devices. “Users commonly use the same password to access email as the password to remotely access a system containing sensitive information,” the report states.
According to Verizon, no anti-virus software had been deployed on any of the examined systems, which left Stratfor “wide open to not only the more sophisticated and customized hacker attempts, but also to other viruses.” While a firewall was in place for the office portion of the Stratfor network at the time of the breach, it was not properly configured to retain any useful information.
Moreover, Stratfor would have been immediately notified of attempts to exfiltrate its customer data and internal emails had it implemented a proper file-monitoring solution. Such a security precaution could have prevented Stratfor's customer data from being stolen by AntiSec in the first place.
Another "significant factor" in the breach was the design of Stratfor's e-commerce environment, which facilitated the electronic transfer of payments by its customers. According to the report, this system was accessible, needlessly, from anywhere within the company's network, "as well as the Internet directly."
Verizon also discovered traces of exfiltrated cardholder information from the e-commerce environment within Stratfor's mail server. That indicates that there were latent flaws in the architecture of the company’s network.
“This finding highlights the inherent problems around the lack of network segregation between the corporate Stratfor environment and the payment and e-commerce environment," the report claims.
Verizon concluded that Stratfor's customer payment system, at the time of the attack, met only three out of the 12 fraud prevention requirements maintained by the report, which were taken from Visa’s fraud control and investigations procedures. Eight of those requirements, which were not met, directly contributed to the breach.
“Typically you’ll find a company deficient in one or two key areas,” noted Kevin Cunningham, the president and founder of SailPoint, a leading independent identity and access management provider. “This is an extreme case and a breakdown of a magnitude I’ve never seen before.
“Security is an interesting dynamic between risk and flexibility,” he continued. “You have to define your policy and ensure that controls are in place. In this case, it doesn’t look like they had any policies defined. It’d be like not only leaving your front door unlocked and your windows open, but also your family jewels on the kitchen table.
“It was an accident waiting to happen.”
Along with the names, credit card numbers, and affiliated data for Stratfor's customers, AntiSec hackers obtained card verification values, the three-digit number located on the back of payment cards. It’s against payment card industry data security standards (PCI DSS) for merchants to retain those codes, according to the PCI Security Standards Council. (The report speculates that since Stratfor outsourced its payment processing functions, the organization may not have been directly required to adhere to these payment industry standards.)
PCI DSS also require credit card numbers to be encrypted when digitally stored by merchants. Stratfor’s founder and CEO previously admitted to storing unencrypted data in an official statement. It was this cardholder information that was stolen by AntiSec in December 2011.
Stratfor ultimately settled a class-action lawsuit with its customers over the losses in June 2012 for a reported $1.75 million.
Interestingly, Verizon also found evidence of another breach that accessed cardholder information: “Analysis of the Zimbra mail server provided Verizon Business with evidence that the intruder(s) created the database dump file (which was later exfiltrated from the STRATFOR environment) on November 16, 2011.”
That discovery appears to further validate the claims of Hyrriiya, an Anonymous hacker known for his cyberattacks on Syrian government websites. In a May 2012 letter sent to Hammond’s attorneys, Hyrriiya confessed to hacking Stratfor and providing AntiSec with access.
“This initial hack of Stratfor occurred approximately TWO week BEFORE anyone involved in #antisec (including Sabu and Hammond) had ANY knowledge or involvement in Stratfor,” Hyrriiya wrote. “After reviewing the data I was able to access in Stratfor, I realised that the customer details included all pertinent credit card information for both individuals and a multitude of corporate entities, military institutions and espionage agencies. Upon this realisation, I promptly decided that I wanted this information to be public.”
A previous Daily Dot investigation found that—contrary to the FBI’s official statements—the Stratfor breach was orchestrated by informant Hector Monsegur. Chat logs show Monsegur obtained critical information about Stratfor’s vulnerabilities privately from Hyrriiya, and then arranged for Hammond to meet with Hyrriiya and gain access to Stratfor.
Monsegur was released in late May on time served. Barrett Brown, a journalist who pleaded guilty in April to being an accessory after the fact in the Stratfor hack, is scheduled to be sentenced in August.
Verizon Wireless did not respond to multiple inquiries. Stratfor declined to comment on this article.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:The online hacktivist Anonymous is back in news with another high profile hack. This time Anonymous Brasil has hacked and defaced the official website of famous Brazilian actress Glˇria Pires.
The 50 years old actress had her website (http://www.gloriapires.com.br/) defaced exactly 5 hours ago with a YouTube documentary video ‘Beyond Citizen Kane; (Muito alÚm do CidadŃo KAN) in Brazilian Portuguese.
Pires works for Rede Globo media group, the largest in Brazil and it seems the main target of Anonymous was Rede Globo media group, as Beyond Citizen Kane (Muito alÚm do CidadŃo KAN) documentary discusses the Globo group’s influence, power, and political connections.
Tweet confirming the hack was done by Anonymous Brazil:In March 2014, Anonymous had vowed to attack Brazilian government and companies sponsoring the World Cup in Brazil. As a showcase, Anonymous took official website of Military Police of SŃo Paulo following with the official website of New York’s Board of Elections against world cup.twitter:AnonBRNews twitterde op maandag 23-06-2014 om 15:38:48 #OpHackingCup #OpWorldCup the game continues #Deface Globo TV actress website. http://t.co/Wge0NoRVM2 http://t.co/RTgZRbb1FS reageer retweet
Let’s see what else coming from Anonymous.
At the time of pubishing this article, Glˇria Pires’s website was restored and working online.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Gabriella Coleman vs Anonymous Digital
Chat with Biella Coleman and Anonymous Digital July 15th, 3pm EST | 20:00 BST | 7pm GMT
IRC: || Channel #AnonDigital
[ClearNet] irc.cyberguerrilla.org || PORT 6667 || SSL PORT 6697
[TOR] 6dvj6v5imhny3anf.onion || PORT 6667 || SSL PORT 6697
[I2P] 127.0.0.1:6669 || See I2P || PORT 6669
For our security-conscious clients:
The below fingerprints may be used to verify the identity of IRC cyberguerrilla server’s.
[ClearNet] SHA-1: 94:1C:FF:7D:BF:19:C1:AA:04:49:0C:57:38:89:71:B3:1F:71:AC:EF
[TOR] SHA-1: DB:CB:9B:31:9C:E3:32:85:80:4E:AD:59:2D:D4:07:D2:97:0F:3E:B7
[I2P] SHA-1: F8:B3:65:10:01:F4:71:0E:8F:FD:6E:71:55:6E:A4:A3:CF:8F:72:0D
HowTo’s:
IRC Client setup || Connect via I2P || Connect via TOR
IRC Identifying with CERTFP || IRC with OTR Encryption
WebChat:
Via cyberguerrilla.org || WebIris
Via TOR || WebIris
KiwiIRC
Discuss her new book
“Hacker, Hoaxer, Whistleblower, Spy: The Story of Anonymous”
http://t.co/tHX0gd4wdH
Also hacking, protests, politics, hacktivists and how Keith Alexander is sure to save the world from DDoS attacks for $600k a month
The NSA will be joining us so it’s a guaranteed good time.
The FBI will be giving away National Security Letters as door prizes.
Out of this chat there will be a radio show made
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Hacken voor Dummies:
twitter:SimonZerafa twitterde op dinsdag 24-06-2014 om 08:23:17 Wanna know the password for Brasil World Cup security centre WiFi? It's on the whiteboard ;-) -> http://t.co/vONTc6210d [ cc @thegrugq] reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Zin in een avondje theater?
quote:Teh Internet Is Serious Business
A 16-year-old London schoolboy and an 18-year-old recluse in Shetland meet online, pick a fight with the FBI and change the world forever.
Tim Price gets behind the code with the original Anonymous members and creates an anarchic retelling of the birth of hacktivism. A fictional account of the true story of Anonymous and LulzSec, the collective swarm who took on the most powerful capitalist forces from their bedrooms.
Tim Price, author of Protest Song about the Occupy movement and National Theatre of Wales’ The Radicalisation of Bradley Manning continues his interrogation of contemporary revolutions.
Tim Price’s theatre credits include: Protest Song at The Shed at the National Theatre, I’m With The Band directed by Hamish Pirie at the Traverse, Praxis Makes Perfect (with Neon Neon, at National Theatre Wales), Demos at the Traverse, The Radicalisation of Bradley Manning for National Theatre Wales, For Once for Pentabus and Hampstead Theatre, tour), Salt Root and Roe, as part of the Donmar Warehouse’s Trafalgar Studio season, which was nominated for an Olivier Award and Will and George. Tim is one of the founders of Cardiff’s leading fringe new writing company Dirty Protest. Launched in 2007, the company has worked with over one hundred Welsh writers, staging new sell-out plays in alternative venues, from pubs and clubs, to kebab shops, hairdressers and a forest. The company took over the Jerwood Theatre Upstairs last summer, as part of Surprise Theatre in the Open Court festival.
Hamish Pirie is Associate Director at the Royal Court and this will be the first time he has directed here. He has worked with Tim Price on three of his shows, directing I’m With The Band and Demos at the Traverse, Edinburgh (where he was previously Associate Director) and Salt Root and Roe for the Donmar Warehouse’s Trafalgar Studio season. His credits at the Traverse include Quiz Show by Rob Drummond, Love With A Capital ‘L’ by Tony Cox, 3 Seconds by Lesley Hart, Most Favoured by David Ireland, Bravo Figaro by Mark Thomas, The Last Bloom by Amba Chevannes and 50 Plays for Edinburgh.
Age guidance 14+
Multi-Buy Offer – Save over 20% with tickets at just ú25.
To use the multi-buy deal purchase three or more Jerwood Theatre Downstairs productions (The Nether, Teh Internet Is Serious Business, Hope or How To Hold Your Breath). Only valid on full price, top-price tickets. Must be booked by 31 July 2014.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous Hacktivists Prepare For Strike Against ISIS 'Supporters'
The hacktivist group Anonymous is planning to launch a series of digital attacks against nations it accuses of funding or arming the radical Islamic terror group ISIS.
Sources within Anonymous told me the campaign will be called Operation NO2ISIS and will target three states suspected of offering support to the Islamic State of Syria and al-Sham (ISIS). Government websites will be blasted with DDoS attacks with Anonymous planning to “unleash the entire legion” upon its enemies.
One of the targets will be Saudi Arabia, a Sunni Muslim nation that has long been suspected of supporting ISIS and other hardline terror groups. However, the Saudi government has dismissed Iraqi prime minister Nouri al-Maliki’s claims that it arms and funds ISIS, describing the “false allegations” as a “malicious falsehood”. The Saudis are thought to be terrified of blowback from the wars in Iraq and Syria, so have taken steps to ban private individuals from donating cash to ISIS militants.
The hacktivists of Anonymous do not believe Saudi Arabia, which is known as the homeplace of Osama Bin Laden and is a long-standing supporter of terrorism. A number of other countries have also been warned to prepare for attacks, which are expected to begin next week. Donors in Kuwait and a number of other Middle Eastern nations are thought to have funded ISIS in the past, making them fair game for Anonymous.
“We plan on sending a straightforward message to Turkey, Saudi Arabia Qatar and all other countries that evidently supply ISIS for their own gain,” the source said. “In the next few days we will begin defacing the government websites of these countries so that they understand this message clearly.
“We are unable to target ISIS because they predominately fight on the ground. But we can go after the people or states who fund them.”
Although ISIS is known to be a savvy user of social media, it has not yet flexed its digital muscles like the Syrian Electronic Army, which famously hacked a number of targets including The New York Times and Forbes itself.
This may be set to change, as Anonymous has already started to lock horns with hackers claiming to be associated with ISIS.
Last week, a Twitter TWTR -1.23% account called @theanonmessage was taken over by ISIS supporters and dozens of graphic images of violence were posted to its timeline. The activist who operates the account admitted that Anonymous were shocked at the attack, which appeared to mimic the tactics already employed by the Syrian Electronic Army itself.
“To be honest, we were taken off guard,” he said. “We didn’t expect a bunch of ragtags to any damage. The ISIS hacking techniques were very similar to hacks done by the Syrian Electronic Army, so that’s pretty interesting.”
As with any cyberattack, it’s difficult to know exactly how much damage will be caused. Anonymous itself once petitioned the White House to make DDoS attacks a form of legitimate protest, which suggests its supporters feel the digital attacks are more useful as a publicity tool than as an actual weapon of war.
This assessment is backed up by security experts. Commenting on a recent threat to attack sponsors of the World Cup, the security firm Symantec SYMC +1.02% summed up the nature of the threat posed by Anonymous like this: “Public announcements by these groups are often used as a means to gain notoriety or media attention and can be of highly volatile credibility. These attacks are typically low scale consisting of DDoS activity against publicly accessible webservers, website defacement efforts, or data exploitation. Symantec does take these threats seriously and has detection in place.”
Perhaps the most dangerous effect of any Anonymous campaign will be the inevitable reprisal. So far, ISIS supporters have largely shunned online attacks, but this could easily change. If the Anonymous claims of a link up between the Syrian Electronic Army and ISIS are to be believed, the damage they could wreak on Western targets could be much more than simply symbolic. Let’s not forget that one false tweet from an AP account wiped more than $90billion from the US stock market. Provoke ISIS’ digital supporters and they will strike back, possibly bringing the fight to America without a single shot being fired.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:Sitting inside a medium-security federal prison in Kentucky, Jeremy Hammond looks defiant and frustrated.
“[The FBI] could've stopped me,” he told the Daily Dot last month at the Federal Correctional Institution, Manchester. “They could've. They knew about it. They could’ve stopped dozens of sites I was breaking into.”
Hammond is currently serving the remainder of a 10-year prison sentence in part for his role in one of the most high-profile cyberattacks of the early 21st century. His 2011 breach of Strategic Forecasting, Inc. (Stratfor) left tens of thousands of Americans vulnerable to identity theft and irrevocably damaged the Texas-based intelligence firm's global reputation. He was also indicted for his role in the June 2011 hack of an Arizona state law enforcement agency's computer servers.
There's no question of his guilt: Hammond, 29, admittedly hacked into Stratfor’s network and exfiltrated an estimated 60,000 credit card numbers and associated data and millions of emails, information that was later shared with the whistleblower organization WikiLeaks and the hacker collective Anonymous.
Sealed court documents obtained by the Daily Dot and Motherboard, however, reveal that the attack was instigated and orchestrated not by Hammond, but by an informant, with the full knowledge of the Federal Bureau of Investigation (FBI).
In addition to directly facilitating the breach, the FBI left Stratfor and its customers—which included defense contractors, police chiefs, and National Security Agency employees—vulnerable to future attacks and fraud, and it requested knowledge of the data theft to be withheld from affected customers. This decision would ultimately allow for millions of dollars in damages.
The documents also confirm the integral role of a shadowy hacker, operating under the handle “Hyrriiya,” who provided key access for the now-infamous attack.
The FBI’s official version of the Stratfor hack, as reported by the New York Times, is that the bureau was made aware of the breach on Dec. 6, 2011, after hackers were already “knee-deep” in confidential files. The FBI claims Hammond informed hacker-turned-informant Hector Xavier Monsegur—also known by the online alias Sabu—of the vulnerability at Stratfor. In turn, the FBI immediately notified the intelligence company, though at that point it was already “too late.”
During his trial, Hammond claimed that the roles were actually reversed: It was Monsegur—released last week on time served—who first introduced him to an anonymous hacker, now known as Hyrriiya, who “supplied download links to the full credit card database as well as the initial vulnerability access point to Stratfor’s systems."
I had never even heard of Stratfor until Sabu brought it to my attention, Hammond said.
His statement echoed a May 2012 letter ostensibly written by Hyrriiya and provided to Hammonds legal defense team. I am stating and admitting, AS FACT, that I was the person who hacked Stratfor, wrote Hyrriiya, a skilled hacker, who's known primarily for his involvement in hacks of Syrian government websites for Anonymous, two months after Hammond was charged.
Previously, however, no public records have substantiated Hammonds and Hyrriiyas claims.
New information, obtained by the Daily Dot and Motherboard in April, not only affirms Hammond's version of events, but also longstanding accusations that federal investigators allowed an informant to repeatedly break computer-crime laws while in pursuit of Hammond and other Anonymous figures. Further, contrary to its prior statements, the FBI, through its surveillance of Monsegur, was aware of a security breach in the network of the private intelligence company well before it was too late.
The evidence on which the Daily Dot-Motherboard investigation is based was collected by Monsegur and his FBI monitors during his time as an informant from June 2011 to March 2012. The cache of court documents includes thousands of previously unseen chat logs, surveillance photos, and government documents, all currently sealed under a protective order upheld by a federal judge in the Southern District of New York.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Wie is hier hardleers?
quote:
Het artikel gaat verder.quote:ProtonMail was supposed to be an easy email encryption tool that would finally give us an answer to Internet surveillance around the world.
Instead, PayPal has frozen over $275,000 in donations to the project because, a PayPal representative told the company, the American payment service is not sure if ProtonMail is legal.
Of course, it is absolutely legal to encrypt email. The freeze remains in place.
Most incredible of all, the PayPal representative was unsure if ProtonMail has the necessary government approval to encrypt emails, as though anyone who encrypts needs a license to do so.
ProtonMail doesn’t need government approval, by the way, but it has it anyway. The encryption used by ProtonMail has been unquestionably legal since the 1990s. If that’s not enough, the Constitution’s First Amendment protects encryption code and its Fourth Amendment guarantees against unreasonable searches, exactly what encryption protects against.
“At this time, it is not possible for ProtonMail to receive or send funds through PayPal,” ProtonMail co-founder Andy Yen announced this morning. “No attempt was made by PayPal to contact us before freezing our account, and no notice was given.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous vows to unleash its 'wrath' on U.S. lawmakers over cybersecurity bill
A threat by the hacktivist group Anonymous over a new cybersecurity bill scheduled for committee markup next month is being taken seriously by the Washington D.C. capitol police.
The Cybersecurity Information Sharing Act of 2014 (CISA), authored by Senators Dianne Feinstein (D-Calif.) and Saxby Chambliss (R-Ga.), is being labelled by many constitutional groups, including the American Civil Liberties Union (ACLU), as the third installment of a much-despised piece of Internet legislation widely known as CISPA.
CISPA, or the Cyber Intelligence Sharing and Protection Act, was a hugely unpopular bill that has twice been dropped by the U.S. Senate. As a law, it would have permitted the U.S. government to share sensitive information with companies about the online habits of U.S. citizens, specifically, when deemed necessary to protect against rather ambiguously defined “cyber threats.”
Opponents of CISPA, such as the Electronic Frontier Foundation (EFF) and Fight for the Future, successfully derailed CISPA by painting it as a danger to American civil liberties. The bill, critics said, would have allowed the federal government too broad authority when it came to tracking users’ online activities.
Like its predecessor, CISA also allows the federal government to share information perceived as “cyber threats” with private companies. The recipients would also have considerable latitude when it comes to sharing the information with law enforcement agencies. Companies would enjoy extensive liability protection for information they share with the government as well, which means customers who feel their rights have been violated may have little or no legal recourse.
“It has come to our attention that Congress is planning to pass a bill that will jeopardize privacy and personal security across all forms of media,” Anonymous’ message against CISA supporters began. “We would like to inform you that despite our direct and crippling attacks on former cybersecurity bills like SOPA, PIPA, and CISPA, there is yet a new threat.”
What likely caught the attention of law enforcement wasn’t the theatrics typical of Anonymous videos, but a threat expressed later in the message: “Our legion's wrath will fall on each senator, representative, corporation, and official who voices support for this bill… If you value the sanctity of your loved ones as well as your own, it will be best for you to back down and drop this bill where it belongs.”
Capitol police, charged with the protection of U.S. senators and congressmen, became aware of Anonymous’ response to the bill on Monday, but said their policy is not to comment on any security protocols or investigations that may be taking place in response to threats.
Sens. Feinstein and Chambliss could not be immediately reached for comment.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Operation Syria Aid: #SaveAtarebHospital
Greetings citizens, we are Anonymous.
We bring you this message as a matter of life or death for over half a million people.
A vital hospital in a war zone will be shut down in less than 3 weeks.
We need to buy the hospital enough time until a large sponsor can pick it up.
As you may be aware the turmoil in the Middle East has significantly increased in the last few years. In Syria, over 100,000 people have been killed in the revolution that has engulfed the nation. The great majority of these deaths are civilian casualties caught in the middle of the fighting. Many have been deliberately slaughtered by rogue rebels, terrorists, or by the Assad regime's air raid campaigns on civilian populations as a form of collective punishment. Despite the many ways to die in Syria the most common is a direct result of the lack of medical attention and hospitals in many areas. What would be commonly a minor injury can very rapidly turn lethal.
To many outside the region the situation appears hopeless and it is hard to find an effective way to help but one hospital has stood out. According to the UK charity 'Hand in Hand for Syria', "the hospital is located just 30 km from Aleppo, one of the hardest-hit areas of Syria." "The hospital became famous when it was featured in the BBC Panorama programme Saving Syria’s Children in September 2013, linked here: ( ),after the hospital received casualties from a thermal-bomb attack on a local school where many innocent children, teachers, parents were severely hurt. Had the hospital not been there, dozens of school children would have perished from their wounds and infections from minor injuries as they do in other areas across Syria without hospitals.
We can't promise you that we can save everybody or provide aid to everyone throughout Syria. What we can tell you is that in the Aleppo area, Atareb hospital and all of it's heroic staff are trying their best to help as many people as they can. Day and night this hospital stands as a beacon of hope for over 500,000 people. According to the UK charity 'Hand in Hand for Syria',"When we first opened the hospital in May 2013, it was just a small A&E unit. We’ve grown it very successfully since then, and it now offers 68 beds and a wide range of services – from maternity and neo-natal facilities to many outpatient departments, three excellent operating theatres and a laboratory. It cares not only for those injured in the conflict but also non-conflict-related conditions such as cancer, heart disease, asthma and diabetes. It even has a dialysis unit. It provides FREE healthcare to anyone, regardless or political or faith affiliation."
From 'Hand in Hand for Syria':
Why is it closing?
The hospital’s funding comes from a European donor which supports global emergency response. This funding reaches Hand in Hand for Syria via an INGO partner. Although that funding is still very much in place, after one year our agreement with our INGO partner has come to an end – and the funding has to come through a partner.
Can’t we find another partner?
Despite the tireless efforts of our trustees and medical team, we have not been able to secure a replacement partner for Atareb Hospital. Because of the very particular situation in Syria, there are difficulties and risks for INGOs when it comes to delivering services there — difficulties which we, as a smaller, independent aid agency, face to a far lesser extent, but which we understand and respect. Only the last-minute intervention of a new partner can save Atareb Hospital now, and we welcome all enquiries from any INGO who may wish to become a partner in the project.
What will the impact of closure be?
One of the very few remaining kidney dialysis units left in northern Syria will shut. Essential and emergency maternity and neo-natal health services will no longer be available. Three excellent operating theatres will remain empty, instantly ending the 282 life-saving operations carried out there each month. 32,000 injured people a year will have no access to emergency care. 25,000 outpatient clinic appointments will be lost. The laboratory will close. Specialist departments including orthopaedics, ophthalmology, gynaecology, neurology, and many more will also shut. The hospital’s 98 staff will be left with no income, no longer able to support a further 400 family members between them."
In the last month 'Hand in Hand 4 Syria' has managed to recieve enough emergency funds to keep Atareb Hospital open for another 4 weeks. However it is still under threat of closure at the end of July 2014. The fate of over 500,000 people is in our hands; it is up to you and I to insure this hospital does not shut down. If it shuts down we can promise you many people will die from completely preventable deseases and treatable injuries.
What can you do to help?
Information blitzkrieg: Anonymous will release a copy of the information/ tweet blitzkrieg with instructions on Saturday July 5th at 6PM EST, you will help us spread awareness to millions of people.
Meanwhile you do the following:
Tell everyone you know, lobby hard and get everyone talking!
Take part in the #SaveAtarebHospital selfie campaign. http://www.handinhandfors(...)sthash.ktWqstPN.dpuf
Donate to help buy the hospital precious time, with your donations it can remain open while we find a permanant parthner: https://www.justgiving.com/HIHS-Atareb-Hospital/
We are Anonymous.
We are everywhere.
We are legion.
We are those you have left without a home.
We are those you have murdered.
We are voiceless no more.
The world will change. We'll change it.
Corporate Tyrants of the World,
Expect Us!
Join us. Help keep Atareb hospital open until a new partner for the project can be found.
The closing down of Atareb hospital will be a massive loss to the half a million people it serves.
Operation: Save Atareb Hospital
Hashtag: #OpSyriaAid. #SaveAtarebHospital
Location: Aleppo, Syria: https://www.google.com/ma(...)ia&source=newuser-ws
Anonymous Contact: @OpSyriaAid
Hospital Contact: @hands4Syr
#SaveAtarebHospital #OpSyriaAid
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:TORONTO — A fellow prisoner gave Matt DeHart a haircut, his first since his April arrest, in preparation for his refugee hearing scheduled to start Tuesday, during which the former U.S. airman was to officially chronicle his claims — of helping Anonymous hacktivists, his aborted attempt to defect to Russia and his subsequent torture at the hands of U.S. jailers — in his unusual bid for asylum in Canada.
But the buoyancy of his mood snapped.
Instead of appearing before a Toronto refugee tribunal Tuesday he was confined in a suicide watch cell after returning to jail from hospital, where he was treated after another suicide attempt.
“Makes me think something happened to him at the jail,” Mr. DeHart’s father, Paul, told the National Post. “A suicide attempt at this point makes no sense since we were all ready to appear and finally make our refugee appeal.”
He said his son was removed Thursday without notice from an immigration holding wing at Central East Correctional Centre, near Peterborough, Ont., and taken to Toronto East Detention Centre, where he was placed in general population.
Het artikel gaat verder.quote:While his story seems incredible, a five-part National Post investigation [link op de site] published in May revealed there is some truth behind some of the claims and many puzzling questions about what took place.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Norway’s financial sector under massive cyber attack, Anonymous claims ‘responsibility’
Norway’s top financial institutions came under massive cyber attacks on Tuesday. Anonymous Norway appears to be behind this attack.
The attack on Norway’s top financial institutions/banks, such as Danske Bank, Norges Bank, Sparebank and renowned insurance agencies Gjensidige and Storebrand had their services disrupted. Other than banks, a telecom company and three national airlines also came under attack.
In an interview with Dagens NŠringsliv business newspaper, Evry’s security team said: “The scale is not the largest we have seen, but it is the first time it has hit so many central players in the finance sector in Norway.” Evry provides IT services to some of the companies affected by the cyber attack.
It appears that hackers used a critical vulnerability in WordPress platform to conduct this attack. However, they weren’t able to hack or takeaway personal information of any user, it added. The investigation shows the source of these attacks was outside Norway, Evry said.
According to one of the biggest Anonymous News Twitter handle, Anonymous Norway claimed responsibility of this attack.
anonymous-ddos-norway-banks [link]
However, in below mentioned tweet you can see Anonymous Norway denying their involvement in this attack.
At the moment it is not clear who was behind these attacks, but one thing is certain that the attack was massive and disrupted many high profile Norwegian websites.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:YourAnonCentral twitterde op zondag 13-07-2014 om 13:49:30 Hackers from around the world are attacking #Israel sites under the #OpSaveGaza banner. #Anonymous #GazaUnderAttack #Gaza via @Op_Israel reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


De Stratfor-hack & de War on Drugs.
quote:
Het artikel gaat verder.quote:The Mexican police helicopter that flew into Arizona last month and fired shots near U.S. Border Patrol agents was no fluke—such incursions have become so frequent they amount to an internationalized shooting war along our southern border.
It’s not just Mexican police helicopters; Mexican military aircraft entered U.S. territory 49 times from 2010 through 2012. That’s according to a Customs and Border Protection list acquired through a Freedom of Information Act (FOIA) request made by WhoWhatWhy.
Along with other documents obtained independently by WikiLeaks, the recent incidents confirm that the U.S. has been taking a full-bore counterinsurgency approach to the border drug war. The possibility that was happening is something we told you about earlier.
Official statements and media reports about the Arizona incident have not come close to explaining the real significance of such cross-border operations. The facts are now clear: the Pentagon’s push to use counterinsurgency tactics against drug traffickers is giving Mexican armed forces the leeway to operate in the airspace above U.S. territory.
***
Specific Mexican military helicopter incursions and near-incursions are detailed in intelligence reports obtained by WikiLeaks and assessed by WhoWhatWhy. The reports were created by the Border Security Operations Center, an Austin nerve center run by the Texas state police that oversees hundreds of intelligence analysts and manages untold surveillance cameras. The reports came to WikiLeaks after hackers broke into the servers of private intelligence firm Stratfor, which got the documents from its sources.
These revelations about the extent of the cross-border war on drugs are the latest fruit of our investigative partnership with WikiLeaks to carefully assess selected documents from its vast trove. (Take a look at our earlier collaborations with the whistleblower group here and here.)
The Rio Grande Firefight
As the Pentagon faces sequestration funding cuts and a fighting force exhausted from Iraq and Afghanistan, the U.S. military is relying more and more on foreign armed forces, police and private contractors like Stratfor.
The close cooperation between U.S. and Mexican forces against drug traffickers follows from modern counterinsurgency strategy, which dictates that police should function like soldiers when necessary to deny funds to whichever rebels—or drug cartels—are out of favor.
This approach is on display in part of a report published by the Austin center on May 6, 2011. The document is marked “Law Enforcement Sensitive.” This means it was intended for law enforcement eyes only, according to intelligence analyst Kendra Miller. She was a contact point for those seeking access to the reports. [Email-ID 1966867, May 9, 2011]
The document describes a firefight about 30 miles from McAllen, Texas, during which a police chopper from that state provided targeting assistance to the Mexican military as an alleged drug smuggler was killed. It includes this photograph of a Mexican Air Force chopper flying above the Rio Grande:
CaptureThis apparent incursion, or near-incursion, was not included on the Customs and Border Protection list we obtained in response to our Freedom of Information request – indicating that Mexican military operations along the U.S. border are even more numerous than the FOIA document suggests.
It’s not clear if that Mexican chopper flew into U.S. airspace. But there’s no doubt the Americans took part in the gun battle, because the Texas state police helicopter guided the Mexican chopper and ground forces to the suspects, including one who was hiding in the brush.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Lawyers blocked our Black hat demo on de-anonymising Tor
Shelved Black Hat presentation would have explained why you don't have to be the NSA to break Tor
The Tor network promises online privacy by routing users' internet traffic through a number of servers – or layers – while encrypting data.
The surveillance whistleblower Edward Snowden is known to have used Tor to maintain his privacy, while the documents he leaked showed that the US National Security Agency (NSA) struggled to uncover identities of those on the network.
However, a presentation promising to detail flaws in the anonymising network has been cancelled, organisers of a major hacker conference have confirmed.
The talk, called "You don't have to be the NSA to break Tor: de-anonymising users on a budget", was due to be delivered by the Carnegie Mellon researchers Alexander Volynkin and Michael McCord, but a notice on the Black Hat conference website said lawyers from the university had stepped in.
The counsel for Carnegie Mellon said that neither the university nor its Software Engineering Institute (SEI), had given approval for public disclosure of the material set to be detailed by Volynkin and McCord, according to the Black Hat organisers.
Their talk was one of the most anticipated sessions at this year’s conference, which starts on 2 August in Las Vegas. They promised to explain how anyone with $3,000 could de-anonymise users of Tor.
Details on the presentation, which have now been removed from the Black Hat site, suggested that a determined hacker could “de-anonymise hundreds of thousands Tor clients and thousands of hidden services within a couple of months”.
Besides individual users, there are numerous criminal websites making use of Tor, including sites offering hitman services and illegal drugs, even though the most prominent example, Silk Road, was shut down in 2013.
Organisers from the Tor Project said they were working with the Computer Emergency Response Team (CERT) at Carnegie Mellon, which is sponsored by the US Department of Homeland Security, to release information on the problems identified by the researchers.
“We did not ask Black Hat or CERT to cancel the talk. We did (and still do) have questions for the presenter and for CERT about some aspects of the research, but we had no idea the talk would be pulled before the announcement was made,” said Tor Project president Roger Dingledine.
“We never received slides or any description of what would be presented in the talk itself beyond what was available on the Black Hat webpage. Researchers who have told us about bugs in the past have found us pretty helpful in fixing issues, and generally positive to work with.”
Carnegie Mellon had not responded to a request for comment by the Guardian at the time of publication.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Russia offers 3.9m roubles for 'research to identify users of Tor'
Analysts say tender for research on service that anonymises browsing sends signal to online community amid crackdown on Russian internet
Russia's interior ministry has offered up to 3.9m roubles (ú65,000) for research on identifying the users of the anonymous browsing network Tor, raising questions of online freedom amid a broader crackdown on the Russian internet.
The interior ministry's special technology and communications group published a tender earlier this month on the government procurement website offering the sum for "research work, Tor cipher".
Before changes to the tender were published on Friday, numerous news outlets reported that it originally sought "research work on the possibility to obtain technical information about users (user equipment) of the anonymous network Tor".
According to Andrei Soldatov, an expert on surveillance and security services, the interior ministry might be exploring possible ways to restrict Tor. But the fact that the tender was publicly announced meant that those seeking greater government control of the internet had defined their next target and were sending "yet another signal" to the online community, he argued.
"It's not important if the Russian government is able to block Tor or not," Soldatov said. "The importance is that they're sending signals that they are watching this. People will start to be more cautious."
The interior ministry refused to comment on Friday afternoon.
Originally developed by the US Naval Research Laboratory as an "onion routing project", Tor is a network of virtual tunnels that allows users to hide the source and destination of their internet browsing and keeps websites from tracking them. It is often used by whistleblowers and residents of countries where the authorities restrict access to the internet, but has also been known to be used for criminal activity. A famous example was the Tor-based online market Silk Road, which was known as an "eBay for drugs" before the FBI shut it down in 2013.
Although many news outlets reported on the recent tender as a reward for "cracking Tor", internet security experts doubted Tor could be successfully decrypted, let alone for a mere 3.9m roubles.
Of all countries, the fifth largest contingent of Tor users come from Russia, where the network's popularity more than doubled in June, going from about 80,000 directly connecting users to more than 210,000. The growth followed a "bloggers law" – signed by the president, Vladimir Putin, in May – requiring any site with more than 3,000 visitors daily to register with the government. Media experts argued that the legislation would stifle opposition voices and restrict government criticism on the internet.
The move was part of a wider campaign to regulate the internet which saw the authorities block three major opposition news sites as well as the blog of anti-corruption crusader Alexei Navalny in March. Users located in Russia can now only access the news sites through anonymising services such as Tor.
This week, Putin signed a law requiring internet companies to store Russian user data in-country, where intelligence services enjoy sweeping access to electronic information through telecoms companies. Critics worry that websites such as Facebook and Twitter, which the opposition used to organise a string of huge rallies in 2011-2013, would be forced to stop operating in Russia when it comes into effect in 2016.
Unlike the Chinese system of internet censorship, which directly blocks websites such as Google, the Russian one is built on intimidation so that users "themselves become more cautious, and internet companies think up ways to block certain sites," Soldatov said.
But blogger, journalist and web entrepreneur Anton Nosik doubted that the Tor research tender would have any effect, arguing that the interior ministry was not a serious player among the various government agencies surveilling the internet but was now "trying to make a name for itself".
"The only significance [of the tender] is the money being paid and the PR surrounding it, showing that the ministry of interior is seriously working on issues of anonymising technology, so that everybody's talking about it. And everybody is talking about it," Nosik said.
More worrying, Nosik said, was leading communications provider Rostelecom's investment in Deep Packet Inspection technology that would filter web traffic based on its content rather than its source. This would severely reduce users' anonymity on the web, although Tor should be able to somewhat limit DPI capabilities, Nosik said.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Herinnert U zich FinFisher nog?
quote:Politie gebruikt mogelijk omstreden spionagesoftware
Digitale activisten hebben een Duits-Brits bedrijf gehackt dat geheime spionagesoftware aan overheden en opsporingsautoriteiten verkoopt. De Nederlandse politie lijkt ook tot de klanten te behoren.
Gisteren verscheen op internet een enorme berg aan technische en klanteninformatie van het bedrijf Gamma International. Dat is de maker van FinFisher, een softwareprogramma waarmee computers kunnen worden ge´nfecteerd om op afstand bestanden te kopiŰren, beeldschermkopieŰn te maken en toetsaanslagen te registreren. Spionagesoftware dus, die alleen wordt verkocht aan overheden.
De hack is een grote overwinning voor burgerrechtenactivisten. FinFisher werd onder meer door de overheid van Bahrein gebruikt om de computers van dissidenten te bespioneren gedurende de Arabische Lente. Sindsdien liggen het programma en het bedrijf onder vuur. Er wordt onder meer gepleit voor exportregels voor dergelijke software.
Politie mogelijk ook klant
Ook de Nederlandse politie lijkt gebruik te maken van het programma. In de gehackte klantenbestanden werd een versleutelingscode gevonden die toebehoort aan een lid van de Nationale Eenheid, de landelijke politie in Driebergen. De match werd gevonden door de Nederlandse hacker Jurre van Bergen, die zich met andere digitale experts op de geopenbaarde informatie had gestort.
Vervolgens werd duidelijk dat deze klant, waarschijnlijk de Nederlandse politie dus, gebruik maakt van drie van Gamma's softwareprogramma's. De licentie zou lopen van 2012 tot 2015.
In Nederland is het op afstand hacken en overnemen van verdachte computers door de politie niet toegestaan. Er is een nieuwe wet in de maak (Wet Computercriminaliteit III), die daar verandering in moet brengen.
Wob-verzoek
'Het is raar dat de politie die producten nu al in gebruik heeft', zegt Rejo Zenger van digitale burgerrechtenorganisatie Bits of Freedom. 'Bovendien hebben ze dat altijd verzwegen.' Zenger diende in 2012 een Wob-verzoek in om te vragen naar het gebruik van spyware. Toen kreeg hij als antwoord dat er geen documenten over waren gevonden.
Een woordvoerder van het ministerie van Veiligheid en Justitie benadrukt dat het gebruik van spyware onder voorwaarden al is toegestaan. Dan gaat het om de installatie van deze software ter plekke, niet om het van afstand overnemen (en live volgen) van de activiteiten op de computer.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:AnonymousGlobo twitterde op vrijdag 08-08-2014 om 21:33:34 FinFinsher leaked: http://q7hglakwm35gxwii.onion/ Take care, information is contagious. #AntiSec reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:True to their word, the activists of Anonymous' #OPFerguson have released two hours of raw audio from police and EMS dispatch calls on August 9, the day 18-year-old unarmed Michael Brown was shot and killed by a police officer in Ferguson, Missouri.
In the interest of public transparency, we're posting the audio here before we've had a chance to go through all of it. Please consider helping us transcribe it or flagging significant events on the audio timeline for fellow readers in the comments below. We'll be updating and adding background along the way.
Note: This is not an exhaustive record of calls from that day. This particular file covers St. Louis County's dispatch; additional city of Ferguson police calls, which may offer more extensive information, have yet to be released.
Here is additional context provided by Anonymous, much of it confirmed by your contributions in the comments below:
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:Hacktivist collective Anonymous had a Twitter account suspended today after they named the wrong police officer in the Michael Brown cop shooting.
Police told NBC that the person who Anonymous had named online is a dispatcher and was not involved in the Ferguson shooting on Saturday.
In a comment today to MailOnline, a Twitter spokesperson said: 'We do not comment on individual accounts, for privacy an security reasons.'
Twitter rules state: 'You may not publish or post other people's private and confidential information, such as credit card numbers, street address or Social Security/National Identity numbers, without their express authorization and permission.'
Anonymous was now tweeting about Ferguson under a secondary account, @TheAnonMessage2.
On Wednesday, the hackers apparently released St Louis police dispatch tapes which reveal further details surrounding the cop shooting death of unarmed black teenager Michael Brown.
The computer hackers' collective posted two hours of the 911 calls online.
quote:The release of the dispatch tapes comes after Anonymous earlier threatened to launch an online attack on police departments over alleged brutality in the killing of the teenager.
Police have cracked down hard on demonstrators in Ferguson, a suburb of St Louis, who took to the streets after the 18-year-old was shot dead.
Despite calls for calm, officers fired tear gas and shot at least one person in a third night of rioting in the area on Tuesday. Police claimed the man shot had pulled a handgun on an officer.
As police tried to put the area on lock-down, messages posted on a newly-established Twitter account called Operation Ferguson, which appeared to be linked to Anonymous, announced: 'We have a deep source, and we have a name we BELIEVE to be the shooter [of Michael Brown]. It does NOT match any of the names being floated.
'We have our best operatives working as hard as they can to verify the leak on the shooter we were passed. PLEASE be patient.
'When we release the name of Mike Brown's killer, it will be in an unequivocal statement released through this Twitter account. No games.'
A little later another message suggested that the operation was proving more difficult than anticipated.
'To my fellow Anons, everyone remain chill,' it read. 'I realize this is an intense Op, and we are all trying our best. Let's fight cops not each other.'
There has been anger from the teenager's parents and their supporters after the Ferguson Police Department decided not to publish the name of the officer who shot their son.
At a rally in Ferguson on Tuesday, his mother, Lesley McSpadden, told the policeman who fired the shots: 'You take your punishment. If you were a man you'd stand up, you'd be a man, you would say you was wrong.'
Police have not disclosed the race of the officer, but witnesses said he was white.
The Ferguson police force has 53 officers, three of whom are black. About two-thirds of Ferguson's population of about 21,000 are black, according to U.S. Census figures.
In a video posted on Sunday night, a self-declared spokesman for Anonymous warned Missouri police 'we are watching you very closely'.
'If you abuse, harass or harm in any way the protesters in Ferguson we will take every web-based asset of your departments and governments offline,' said a disguised voice, speaking over news footage of protests.
'That's not a threat, it is a promise.'
In the video and a press release posted to the Pastebin website, the video says Anonymous will 'attack ever server and computer' belonging to the police departments involved, as well as 'release the personal information on every single member of the Ferguson Police Department, as well as any other jurisdiction that participates in the abuse.'
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:Among other things here at Linux Format we are also a bit clairvoyant. We decided that it was the right moment to look at 'anonymous' Linux distributions many weeks before mainstream media started discussing PRISM.
Of course, even if nothing like that existed, there would still be many good reasons to protect at least part of what you want or need to do online: the examples go from whistle-blowing to home banking or super-invasive advertising. In all these cases, proper configuration of (at least!) the tools you use for web surfing, email, instant messaging and file sharing is crucial.
Linux 'anonymous' distros are designed to help in just these kinds of situations. As a minimum, these systems are pre-configured to make it easier to surf the web without telling everybody in clear text where, or who, you really are.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Not Anonymous:
quote:Hackers Will Leak Syrian Stock Exchange Database Unless Assad Tackles ISIS
A group of hackers took down the website of Syria's only stock exchange this afternoon and are threatening to leak the exchange's database unless president Bashar al-Assad takes military action against the Islamic State.
The group, called Project Viridium, says that over the last several weeks, it has infected several Islamic State operatives' computers and have provided the Assad government with information about their whereabouts.
Earlier today, the group tweeted that it had successfully taken down the Damascus Securities Exchange. At the time of this writing, the exchange's website is still inaccessible, due to what appears to be a fairly common DoS (Denial of Service) attack.
A member of the group confirmed to me on Twitter that the site was taken down with a DoS attack, but said that the group had also gained access to the exchange's servers and databases.
Project Viridium says it's ready to release the exchange's database, which would include financial information and user login credentials, if Assad doesn't take action against the terrorist group.
"We have many members pwned," the hacker told me. "Soon to come, we'll post that."
About a half hour after taking down the stock exchange, Project Viridium published the following statement on DOXBIN, which you can gain access to with the Tor browser (message posted as it was written):
Statement regarding DSE DDoS/Hack:
First, let me introduce my(our)self. We are ProjectViridium (yes like the pokemon). We have fought silently for the last 4-6 years against blackhats and scammers. Only recently did we decide to start targeting Terrorist groups. We have been gathering inteligence on ISIS members for about 2 weeks now. So far we have 15 caged (i.e malware on pc/equiv) and about 40 prospects (not yet pwned, waiting). Our general goal is to make a dint, however big or small in the world of terror.
Why did we target syria exchange?
k, first. anonymous, you didnt ddos it fuck off and go play minecraft. Second, we did this attack in retaliation for Syrian/Assad regime ignoring our reports of ISIS member locations (1 member is exactly 3.4km from a fucking police station). The evidence of ISIS members location in this specific case is gathered without use of ANY malware, hacking or anything of the such. Adding that before someone mentions how assad cant act cause
evidence is from hacking (like he'd give a fuck)
Stay tuned.
-PV
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:The_MattGreen twitterde op zondag 31-08-2014 om 07:23:53 #Anonymous has begun #OpIceISIS, a new cyber operation to combat #ISIS digitally as violence continues to spread through Iraq and Syria. reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Top South America hackers rattle Peru's Cabinet
LIMA, Peru (AP) — The Peruvian hackers have broken into military, police, and other sensitive government networks in Argentina, Colombia, Chile, Venezuela and Peru, defacing websites and extracting sensitive data to strut their programming prowess and make political points.
Their latest stunt may be their most consequential.
Emails that the LulzSecPeru hackers stole from the Peruvian Council of Ministers' network and dumped online last month fueled accusations that top Cabinet ministers have acted more like industry lobbyists than public servants. They helped precipitate a no-confidence vote last week that the Cabinet barely survived.
The hackers are a compact, homegrown version of the U.S. and U.K-based LulzSec "black hat" hacker collective that grew out of the Anonymous movement, which has variously attacked the Church of Scientology and agitated on behalf of the WikiLeaks online secret-spillers and Occupy Wall Street.
A lot of "hacktivism" out of the United States and western Europe has waned or been driven underground after police pressure and arrests, said Gabriella Coleman, an anthropologist at McGill University, in Montreal, Canada, who has studied the phenomenon.
"The hackers in Latin America, however, never really stopped," Coleman said.
Of them, LulzSecPeru is widely considered the region's most skillful and accomplished hacktivist team, said Camilo Galdos, a Peruvian digital security expert, their signature exploit hijacking the Twitter accounts of Venezuela's president and ruling socialist party during elections last year.
"Happy Hunting!" the LulzSecPeru hackers — they say they are two young men — wrote last month when they dumped online the estimated 3,500 emails of then-Prime Minister Rene Cornejo, dating from February to July.
Cornejo told reporters: "The concern isn't so much for the information to be found there but for the fact that privacy was violated." His successor, Ana Jara, said some of the purloined emails may have concerned matters of "national defense."
But what reporters found instead was evidence of the inside influence of Peru's fishing and oil industry lobbies, putting the country's energy and finance ministers in the hot seat.
In one missive, a fishing industry executive asks the finance minister if the anchoveta season can be extended. She later gets her wish.
The energy minister, in a testy email exchange, impatiently dismisses objections by the environment minister to his coziness with an Australian oil company with offshore concessions. Oil industry technicians — not regulators — are best qualified to deem whether environmental impact studies are necessary for exploratory seismic testing, he says.
The "CornejoLeaks" spectacle, as the press dubbed it, delighted the hackers.
"We're mixed up in everything," one of the duo, who goes by the nickname Cyber-Rat, boasted in an encrypted online chat with The Associated Press into which he had tunneled, hiding his digital tracks. "There is no limit to the hacking."
Cyber-Rat says he's 17 and will quit before becoming an adult to avoid landing in prison. He handles the social networking, cultivates the Anonymous activists who help publicize LulzSecPeru's hacks and admits to "a tendency toward narcissism." His partner goes by Desh501, says he is between 19 and 23 and a university student.
Desh is the technical whiz, and more reserved.
"I'm very private. I don't have hacker friends in person, only virtually," Desh types.
Both say they are autodidacts. Cyber-Rat says he started programming at age 8; Desh at age 6.
Cyber-Rat says their hacking is not really ideologically driven.
"It's a quest for (the) ecstasy of doing something unprecedented," he said, of shaming administrators who claim their networks are bulletproof.
Their actions don't always mesh with that claim, however.
Desh said he is motivated by objections to "1. the abuse of power. 2. the lack of transparency."
Some of their hacks are clearly political. They defaced the website of the Peru-based Antamina copper mine in 2012 after the multinational consortium's slurry pipeline burst, sickening dozens. Rat's idea, said Desh.
And they defaced the Venezuelan ruling party's website again in February in support of anti-government protesters, entering through one of the backdoors they say they secretly leave in networks they penetrate.
Desh said they also retain access to the Chilean Air Force network, from which they removed and dumped online last month sensitive documents on arms purchases. They called it payback for Chile's spying on Peru's air force in a case uncovered in 2009.
The hackers, who have 30,200 Twitter followers, say they neither enrich themselves nor do damage with their exploits.
But many believe LulzSecPeru did do harm in accessing the network of the company that manages Peru's top-level domain. In October 2012, it dumped online a database of thousands of names, phone numbers, email addresses and passwords of affected sites included banks, security companies, Google — every domain ending with ".pe"
Desh said Rat did so without consulting him. "I almost killed him that day."
A company representative and leading Peruvian Internet activist, Erick Iriarte, said the hack occurred well before the upload and customers were notified in time to change their passwords. Desh confirmed that the break-in occurred six weeks before the upload.
Across Latin America, government-run networks are generally regarded by state workers as insecure and untrustworthy. A surprising number of senior officials use private email services instead.
Peruvian authorities call LulzSecPeru "cyber-pirates" and say they could face up to eight years in prison under Peru's new computer crimes statute.
But they first must be caught, and independent security experts say Peru's cyberpolice are badly outmatched. LulzSecPeru's first claim to fame was penetrating the Peruvian cyberpolice network in early 2012. It claims it still has hidden backdoor access.
The unit's commander, Col. Carlos Salvatierra, called such criticism unfounded. He would not discuss details of the LulzSecPeru investigation but said it includes "permanent coordination" with other affected governments and has been ongoing for months.
LulzSec as a moniker fuses 'lulz' — which derives from LOL (laughing out loud) and evokes in part the mischievous bliss of hackers who expose sloppy security ('sec'). And there is little greater 'lulz' for the pair than mocking Roberto Puyo, technology chief for Peru's Council of Ministers and the president of the Lima chapter of the Information Systems Security Association, the country's top cybersecurity group.
Puyo did not respond to attempts to reach him by phone and email seeking an explanation for how his network was violated.
Desh said getting inside took him a month.
He said he then routed a carbon copy of all traffic for nearly a month to an external server, capturing Cornejo's email password in the process. Desh said Cornejo's Gmail account was linked to the ex-premier's official email account and that he accessed a mirror of it on the network.
Rat said the hackers are staying away from the Council of Ministers' network for now. He says it now has "honey pots" — traps set to try to ensnare them.
The two say they are confident they cover their tracks sufficiently. And they said they don't tempt fate, keeping U.S. government networks off their target list because they don't want the FBI pursuing them.
"I don't worry that much, though I don't rule out the option that they will trap me," said Desh.
"Nobody is invincible."
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:GCHQ backlash? Anonymous website hacked following privacy rights protest
Anonymous UK’s website was recently targeted and taken down in the midst of a four-day privacy rights protest organized by the collective. The demonstration was held outside Britain’s Government Communications Headquarters (GCHQ).
A spokesman for the hacktivist group believes the targeted attack was carried out by GCHQ officials.
The protest, which began outside Britain’s Cheltenham-based spy base last Friday, was reportedly launched to highlight an ongoing assault on Britons’ privacy rights against a backdrop of increasing mass surveillance. But prior to the main day of protest scheduled for Saturday, Anonymous UK’s website was taken down. The incident occurred late Friday evening.
This is not the first time the group has had such an experience. A spokesperson for the hacktivist collective, who runs Anonymous UK's online radio station, insists they have been unjustly targeted by GCHQ on multiple occasions.
“One of our servers was destroyed and our UK radio station has been shut down,” the spokesperson told RT on Friday, adding that the group's site was also taken down following the launch of a campaign to feed homeless people.
Commenting on the cyber attack, the spokesman said that if a member of the public targeted a government site in this manner, they could "get up to five years in prison the UK." Yet “GHHQ has no one to answer to.”
“This is why we protest,” he stressed.
Although GCHQ allegedly attempted to liaise with Anonymous UK in advance of the demonstration, a spokesperson for the collective said the group declined to respond. The collective believes privacy rights advocates have a democratic right to protest peacefully, and shouldn't have to justify their desire to do so to UK authorities.
Probed as to whether Anonymous UK plans to issue a formal complaint about the targeting of its website, a spokesperson said “we can’t complain to anyone” because “GCHQ would just deny it.”
Central to the group’s privacy rights concerns is an alleged UK intelligence operation called Tempora. Covert documents sent to the Guardian by US whistleblower Edward Snowden state that the program facilitates British intelligence officers’ access to private data. Such information relates specifically to email, social networking, and telephone conversations.
Britain’s Investigatory Powers Tribunal is currently seeking to discern whether Tempora exists, and if it violates Article 8 of the European Convention on Human Rights – which deals with citizens’ right to privacy. A final judgment on the case is yet to emerge, and the group of high profile UK and international civil liberties groups that launched the proceedings is currently awaiting an outcome.
Anonymous UK told RT on Friday that the collective is doubtful the final judgement will favor the public’s right to privacy.
According to the hacktivist collective, approximately 60 protesters attended the demonstration over the weekend in a bid to raise awareness about the intrusive nature of GCHQ mass surveillance. Others estimate the number of attendees may have been more moderate. Anonymous UK stated all activists demonstrated in a peaceful and lawful manner, and there were no arrests. Nevertheless, its site remains inaccessible visitors.
The UK-based collective is a subset of Anonymous, a nebulous international network of activists and hacktvists known for politically charged, subversive maneuvers worldwide. Recent actions carried out by the broader group include efforts to tackle global inequality, operations to counter government attacks on citizens’ privacy rights, efforts to mitigate child pornography, and a “cyber assault” against Israel to counter IDF operations in Gaza.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:Have the UK police successfully broken anonymity on the internet? They certainly seemed to imply as much when the National Crime Agency proudly announced last week that it had made 660 arrests after an operation to identify people viewing indecent images of children online.
The announcement raises questions about just how anonymous it is possible to be online, particularly in the dark net and through systems like Tor, which is used by criminals, but also many others with legitimate reasons for wanting to remain anonymous such as journalists, whistleblowers, and political activists under repressive regimes.
We should also treat the NCA bust with some scepticism, given its very convenient political timing.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Lulz and Dissent: A New Book on Anonymous
Last March, I read Alice Marwick’s Status Update, a fascinating ethnographic account of Silicon Valley culture and how entwined that culture is in the design of the social media platforms that we use daily. It’s a world that presumes good things come to those who are smart and work hard and, within this meritocracy, everyone’s an entrepreneur with a personal brand to develop.
I’ve just finished reading another ethnography that provides a fascinating counterpoint. Gabriella Coleman, a cultural anthropologist at McGill University, has been studying Anonymous since 2008 and has a terrific book coming out this November from Verso, Hacker, Hoaxer, Whistleblower, Spy. Members of Anonymous and the tech workers who created Twitter, Facebook, and many other hot tech brands have some things in common. They resist hierarchy and value individuality. They socialize and develop projects using Internet channels. They aren’t intimidated by established institutions and resist government control.
But there’s a fundamental difference. The culture Marwick studied values aggregating wealth and attention. Anonymous abhors personal attention-seeking as a means of accumulating capital. While Marwick showed a culture that assumed individual striving could lead to entrepreneurial success, a form of success created by capturing data about social interactions online, the portrait Coleman develops of Anonymous is an anarchic collective that subsumes individuality to the pursuit of lulz (deviant humor) and the free flow of information. In a sense, it’s the free-wheeling ethos of the old Internet at war with the new, one that is dominated by giant companies that determine the rules about how we will interact online and promote personal branding to conduct monetizable surveillance. Remember the New Yorker cartoon, “on the Internet, nobody knows you’re a dog?” Now corporations operating through the internet not only know who you are, they know what brand of dog food you buy.
Coleman’s book starts with the disreputable roots of the Anonymous collective in the boisterous trolling conducted on 4Chan, which embraced anonymity and practiced extreme Rabelaisian permissibility. In a sense it was the “primordial stew” that gave rise to a movement that is characterized by deviance that is carnivalistic in the Bakhtinian sense and yet has a strongly moral bent when it comes to free speech. For an anthropologist, the self-organizing complexity of this constantly morphing group is a fascinating puzzle. Its anti-celebrity ethos, which also values individual rights, upends “the ideological divide between individualism and collectivism” while presenting an alternative approach to the society itself.
Anonymous began to recognize its potential as a political force when some members suggested their collective trolling power should be directed at the Church of Scientology, which was using strongarm tactics to suppress a video they objected to. Mass trolling worked. Coleman was able to observe how that initial protest came together and how it set the stage for other forms of dissent, including attacks against banks that tried to cripple WikiLeaks by cutting off access to donations. Anonymous began to take on other political causes. It (they?) played a significant role in the opening weeks of the Arab Spring and launched other actions, including some that have backfired, such as the recent release of an incorrect name when protestors at Ferguson demanded to know which officer shot Michael Brown. These actions are often what one Anon called a “moral pretzel,” very similar to the ethical issues that come with any disruptive political direct action, but with greater legal consequences. And like any protest movement that gets the attention of the authorities, it is subject to infiltration by informants and agents provocateurs.
Coleman does a fantastic job of chronicling Anonymous’s political turn while explaining her own moral pretzels as a researcher. She illuminates a movement that bucks the cultural trend to self-promote and examines the “fractal chaos” of a leaderless collective that is deliberately hard to pin down but looks a little bit like the Internet when it was young.
Reading studies like this and Marwick’s Status Update make me impatient to figure out how to better prepare our students to engage in the world by understanding the structures of information that are evolving around us. While students need to recognize what scholarship looks like so that they can learn about the ethical practices underlying scholarly discovery, the world of information exhibits its own fractal chaos that makes the oversimplified categories “scholarly” and “popular” misleadingly naive. That said, this book demonstrates how valuable it is to have scholars studying phenomena like the emergence of Anonymous as a radically collective political force
Hacker, Hoaxer, Whistleblower, Spy won't be released until November, but meanwhile you can read some of Coleman's articles about Anonymous in Wired, the Index on Censorship and elsewhere.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous - Message To Cameron and Obama
David Cameron and President Obama need to take action NOW! Rid the world of ISIS.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:Leiderman’s been called Anonymous’ lawyer of choice, and has defended or advised Anons from political refugee Commander X through LulzSec, AntiSec, incarcerated Anonymous spokesman Barrett Brown, and more. We asked him why he chose this field rather than something that might buy him a yacht or at least the ability to sleep at night. He replied that it was certainly anything but a calculated careerist move, and less his choice than the inevitable result of recent changes in the way the courts are used by The Powers That be.
quote:We first caught him on the cell at an airport thanks to a delayed flight from a location he is not allowed to disclose. Because thats just how he rolls. Heck, the man has his own Anonymous trading card. Next, we played Facebook and Twitter and email tag for some time, but finally re-connected via Skype; this time he was able to disclose that he was in his office, something we at the Cryptosphere had already surmised because his receptionist answered the phone. This interview has been stitched together from emails, PMs, DMs, calls via Skype, and calls via actual telephone over the course of some months. Its a long read: get yourself a beverage and comfortable chair. Its worth it.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Anonymous Rave wordt manifestatie in industriegebied
De Anonymous Rave gaat toch door, maar nu als manifestatie. Dat heeft de organisatie afgesproken met burgemeester Eberhard van der Laan. De manifestatie staat gepland op 27 september, de datum waarop de rave oorspronkelijk was gepland.
De Anonymous Rave werd in juli aangekondigd als illegaal feest in de binnenstad. Het was een protest tegen hoge drank- en entreeprijzen in de Amsterdamse horeca.
Binnen korte tijd hadden 54.000 mensen zich op Facebook aangemeld voor de Anonymous Rave. Er zouden vijf podia in de binnenstad worden opgebouwd, waar verschillende dj's zouden draaien. Entree zou gratis zijn en iedereen kon eigen drank meenemen.
De gemeente voorzag veiligheidsproblemen en kwam met behulp van nachtburgemeester Mirik Milan in contact met de organisatoren, aldus een woordvoerder. De uitkomst is dat het geen rave maar een manifestatie wordt. De locatie is niet in de binnenstad, maar in industriegebied Westpoort. De organisatie zal het evenement morgen op Facebook aankondigen. Hoe het er precies uit gaat zien, is nog niet bekend.
De mensen achter Anonymous Rave zeggen zich in de toekomst te willen richten op betaalbare evenementen. 'We willen het mogelijk maken dat elke doelgroep, rijk of arm, in Amsterdam kan uitgaan.'
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Putin considers plan to unplug Russia from the internet 'in an emergency'
Kremlin to discuss taking control of the .ru domain and measures to disconnect Russians from the web in the event of unrest
The Kremlin is considering radical plans to unplug Russia from the global internet in the event of a serious military confrontation or big anti-government protests at home, Russian officials hinted on Friday.
President Vladimir Putin will convene a meeting of his security council on Monday. It will discuss what steps Moscow might take to disconnect Russian citizens from the web "in an emergency", the Vedomosti newspaper reported. The goal would be to strengthen Russia's sovereignty in cyberspace. The proposals could also bring the domain .ru under state control, it suggested.
Russian TV and most of the country's newspapers are under the Kremlin's thumb. But unlike in China, the Russian internet has so far remained a comparatively open place for discussion, albeit one contested by state-sponsored bloggers and Putin fans.
The move comes at a time when Russia has been bitterly critical of the western media, which Moscow says has adopted a biased attitude towards events in Ukraine. Russian channels have portrayed the conflict in Ukraine as a heroic fight against "fascists" in Kiev. They have disputed western reports that Russian soldiers and heavy weapons are involved. A BBC team that went to investigate reports of Russian servicemen killed in Ukraine was beaten up this week.
According to Vedomosti, Russia plans to introduce the new measures early next year. The Kremlin has been wrestling for some time with how to reduce Russia's dependency on American technology and digital infrastructure, amid fears that its communications are vulnerable to US spying. It has mooted building a "national internet", which would in effect be a domestic intranet. These proposals go further, expanding the government's control over ordinary Russian internet users and their digital habits.
Andrei Soldatov, an expert on Russia's spy agencies, described the plans as big news. In an email from Moscow he said he "didn't actually believe" Russian officials would disconnect the internet. But he said the moves were a "real step forward in the development of a besieged fortress mentality".
He wrote: "Before, such ideas were mostly to do with so-called government communications (how to make them independent from western technologies). Now they want to expand this crazy idea to the entire internet of the country."
Soldatov said it would be technically possible for Moscow to shut off the internet because Russia has "surprisingly few" international exchange points. All of them are under the control of national long-distance operations, like Rostelecom, which are close to the authorities, he said.
The most ominous element, he added, was the security council's apparent proposal to take control over .ru, as well as the domains .su (for Soviet Union) and .рф (Russian Federation in Cyrillic). These domains currently belong to a non-government organisation, the coordination centre of the national domain, rather than to government. Many are currently hosted abroad.
"The thing might be approved very quickly, and this means it shows a way to the next step – to force all domains in the .ru zone to be hosted in Russia," Soldatov said. Kazakhstan, an authoritarian state intolerant of online criticism, did something similar two years ago, he said, adding that such a move would affect his own website Agentura.ru, which is hosted in Germany.
Putin's press secretary, Dmitry Peskov, confirmed the meeting would take place on Monday, adding that much of it was likely to be in closed session. The communications ministry declined to comment on Friday.
While Putin enjoys popular support, with his approval ratings boosted by Russia's takeover of Crimea from Ukraine in March, the danger of mass unrest is not lost on the Kremlin. In 2011-2012 tens of thousands of Russians protested in Moscow after Putin announced he was returning as president and shoving aside his temporary successor Dmitry Medvedev. The protests fizzled out following a series of arrests, harassment of opposition figures, and high-profile trials.
The Russian economy, which is already teetering on the verge of recession, is reeling from ever more stringent Western sanctions over Moscow's alleged support for separatists in eastern-Ukraine. Washington and Brussels have introduced several rounds of sanctions that are the toughest punitive measures since the cold war.
An employee of a large communications provider told Vedomosti Moscow did not want to unplug the world wide web but to protect Russian cyberspace in case of further western sanctions that may affect the internet.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
| Forum Opties | |
|---|---|
| Forumhop: | |
| Hop naar: | |



![Its Over 9000!!! [Original Video and Audio]](http://i.ytimg.com/vi/SiMHTK15Pik/default.jpg)






 And all this because man put in motion systems that returned to enslave him
And all this because man put in motion systems that returned to enslave him 

 "I just miss - I miss being anonymous." - Barack Obama” -.-
"I just miss - I miss being anonymous." - Barack Obama” -.- 




 In all my years studying Anonymous this case is the most troubling + puzzling: Hacker, Creeper, Soldier, Spy
In all my years studying Anonymous this case is the most troubling + puzzling: Hacker, Creeper, Soldier, Spy  Page 11 of "#Sabu" sentencing doc contains apparent reference to FBI operation against WL
Page 11 of "#Sabu" sentencing doc contains apparent reference to FBI operation against WL  Judge at "Sabu" hacker informant sentencing "salutes" his "extraordinary cooperation" with FBI - lets him walk with time served
Judge at "Sabu" hacker informant sentencing "salutes" his "extraordinary cooperation" with FBI - lets him walk with time served 






 Wanna know the password for Brasil World Cup security centre WiFi? It's on the whiteboard ;-) ->
Wanna know the password for Brasil World Cup security centre WiFi? It's on the whiteboard ;-) -> 



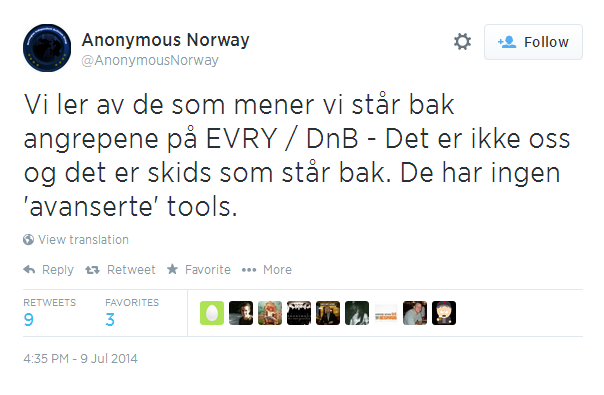
 Hackers from around the world are attacking
Hackers from around the world are attacking  FinFinsher leaked:
FinFinsher leaked: 




