

twitter:AnonyOps twitterde op dinsdag 28-10-2014 om 14:45:06 The FBI has reportedly raided the home of a "2nd Snowden". Watch how they treat them for an example of how they would have treated Snowden reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Feds identify suspected 'second leaker' for Snowden reporters
The FBI recently searched a government contractor's home, but some officials worry the Justice Department has lost its 'appetite' for leak cases
The FBI has identified an employee of a federal contracting firm suspected of being the so-called "second leaker" who turned over sensitive documents about the U.S. government's terrorist watch list to a journalist closely associated with ex-NSA contractor Edward Snowden, according to law enforcement and intelligence sources who have been briefed on the case.
The FBI recently executed a search of the suspect's home, and federal prosecutors in Northern Virginia have opened up a criminal investigation into the matter, the sources said.
But the case has also generated concerns among some within the U.S. intelligence community that top Justice Department officials — stung by criticism that they have been overzealous in pursuing leak cases — may now be more reluctant to bring criminal charges involving unauthorized disclosures to the news media, the sources said. One source, who asked not to be identified because of the sensitivity of the matter, said there was concern "there is no longer an appetite at Justice for these cases."
Marc Raimondi, a spokesman for the Justice Department, declined to comment on the investigation into the watch-list leak, citing department rules involving pending cases.
As for the department's overall commitment to pursue leak cases, he added: "We're certainly going to follow the evidence wherever it leads us and take appropriate action."
Another source familiar with the case said: "Investigators are continuing to pursue it, but are not ready to charge yet."
The case in question involves an Aug. 5 story published by The Intercept, an investigative website co-founded by Glenn Greenwald, the reporter who first published sensitive NSA documents obtained from Snowden.
Headlined "Barack Obama's Secret Terrorist-Tracking System, by the Numbers," the story cited a classified government document showing that nearly half the people on the U.S. government's master terrorist screening database had "no recognized terrorist affiliation."
The story, co-authored by Jeremy Scahill and Ryan Devereaux, was accompanied by a document "obtained from a source in the intelligence community" providing details about the watch-listing system that were dated as late as August 2013, months after Snowden fled to Hong Kong and revealed himself as the leaker of thousands of top secret documents from the NSA.
This prompted immediate speculation that there was a "second leaker" inside the U.S. intelligence community providing material to Greenwald and his associates.
That point is highlighted in the last scene of the new documentary about Snowden released this weekend, called "Citizenfour," directed by filmmaker Laura Poitras, a co-founder with Greenwald and Scahill of The Intercept.
Greenwald tells a visibly excited Snowden about a new source inside the U.S. intelligence community who is leaking documents. Greenwald then scribbles notes to Snowden about some of the details, including one briefly seen about the U.S. drone program and another containing a reference to the number of Americans on the watch list.
"The person is incredibly bold," Snowden says. Replies Greenwald: "It was motivated by what you did."
In an interview on the radio show "Democracy Now," Scahill, who also briefly appears in "Citizenfour," says the new source described in the film provided him with a document that "outlines the rulebook for placing people on a variety of watch lists." The source is "an extremely principled and brave whistleblower" who made his disclosures "at great personal risk," Scahill says in the interview.
Contacted Monday, Scahill declined any comment about his source, but said neither he nor The Intercept had been notified by federal officials about the investigation. He added, however, that he is not surprised to learn of the probe: "The Obama administration in my view is conducting a war against whistleblowers and ultimately against independent journalism."
John Cook, editor of The Intercept, said the website's stories had revealed "crucial information" about the excesses of the U.S. watch-listing system. "Any attempt to criminalize the public release of those stories benefits only those who exercise virtually limitless power in secret with no accountability," he told Yahoo News.
Sources familiar with the investigation say the disclosures prompted the National Counterterrorism Center to file a "crimes report" with the Justice Department — an official notification that classified material has been compromised and a violation of federal law may have taken place.
The documents in question disclose multiple details about how federal intelligence agencies provide entries and track suspects on the Terrorist Identities Datamart Environment, or TIDE — a master database with over 1 million names that provides the basis for watch-listing individuals and placing them on "no fly" lists when there are sufficient links to terrorism.
One document is stamped as "Secret" and "NOFORN," meaning it cannot be shared with foreign governments. These, however, are far less sensitive than some of the NSA materials leaked by Snowden.
During Obama's first five years as president, the Justice Department and the U.S. military brought seven criminal prosecutions for national security leaks — more than twice as many as all previous presidents put together.
But the Obama administration's aggressive anti-leak efforts triggered a firestorm of criticism last year after disclosures that, in pursuing these cases, prosecutors had secretly subpoenaed phone records from the Associated Press and filed a search warrant identifying a Fox News reporter as a potential "co-conspirator" under the Espionage Act for his efforts to coax information from a confidential source.
Since September of last year, when a former FBI agent pleaded guilty to disclosing details about an al-Qaida bomb plot to the AP, the Justice Department has brought no further leak cases. Attorney General Eric Holder — who sources say was personally stung by the criticism — has also unveiled new "guidelines" that restrict how the Justice Department would seek information from the news media in leak cases.
Holder, who recently announced his plans to step down, also appeared to signal that he was eager to avoid further confrontations with the press when he was asked whether he would seek to incarcerate New York Times reporter James Risen if he refused to testify in an upcoming trial of a former CIA officer accused of leaking him information about a covert effort to disrupt Iran's nuclear program. Risen has vowed he will never testify about a confidential source.
"As long as I am attorney general, no reporter who is doing his job will go to jail," Holder said at a meeting with news media representatives when asked about the Risen case.
But Steve Aftergood, who closely tracks government secrecy efforts, said, "It's an open question at this point whether the administration will indict any other leakers or pursue other prosecutions."
He noted that, despite Holder's comments, Justice Department prosecutors had yet to formally inform a federal judge whether they will call Risen at the trial of the former CIA officer — a move that could result in a direct confrontation with the reporter if he is asked to identify his source.
"These leaks are taken extremely seriously," he said. If prosecutors have sufficient evidence against the suspected new leaker, "I don't think they will let it slide."
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:GCHQ views data without a warrant, government admits
GCHQ’s secret ‘arrangements’ for accessing bulk material revealed in documents submitted to UK surveillance watchdog
British intelligence services can access raw material collected in bulk by the NSA and other foreign spy agencies without a warrant, the government has confirmed for the first time.
GCHQ’s secret “arrangements” for accessing bulk material are revealed in documents submitted to the Investigatory Powers Tribunal, the UK surveillance watchdog, in response to a joint legal challenge by Privacy International, Liberty and Amnesty International. The legal action was launched in the wake of the Edward Snowden revelations published by the Guardian and other news organisations last year.
The government’s submission discloses that the UK can obtain “unselected” – meaning unanalysed, or raw intelligence – information from overseas partners without a warrant if it was “not technically feasible” to obtain the communications under a warrant and if it is “necessary and proportionate” for the intelligence agencies to obtain that information.
The rules essentially permit bulk collection of material, which can include communications of UK citizens, provided the request does not amount to “deliberate circumvention” of the Regulation of Investigatory Powers Act (Ripa), which governs much of the UK’s surveillance activities.
This point – that GCHQ does not regard warrants as necessary in all cases – is explicitly spelled out in the document. “[A] Ripa interception warrant is not as a matter of law required in all cases in which unanalysed intercepted communications might be sought from a foreign government,” it states. The rules also cover communicationsdata sent unsolicited to the UK agencies.
Campaigners say that this contrasts with assurances by parliament’s Intelligence and Security Committee in July last year that a warrant signed by a minister was in place whenever GCHQ obtained intelligence from the US.
The data can then be stored for up to two years, the same duration as information collected directly by the agency. This can be extended unilaterally if a senior official believes it to be necessary and proportionate for national security purposes.
Privacy International, one of several advocacy groups mounting legal challenges against GCHQ and NSA surveillance, said the revelation should cast further doubts on legal safeguards in the UK.
“We now know that data from any call, internet search, or website you visited over the past two years could be stored in GCHQ’s database and analysed at will, all without a warrant to collect it in the first place,” said deputy director Eric King. “It is outrageous that the government thinks mass surveillance, justified by secret “arrangements” that allow for vast and unrestrained receipt and analysis of foreign intelligence material is lawful.”
The group also said information obtained through these overseas “arrangements” was treated as if it were targeted surveillance, removing a requirement under UK law not to search for UK citizens and residents in such data troves. This means that British citizens could, in theory, be subject to warrantless monitoring by GCHQ.
Amnesty International and Liberty, the co-complainants in the IPT case, echoed Privacy International’s call for reform of surveillance safeguards.
“It is time the government comes clean on such crucial issues for people’s privacy as the sharing of communications intercepts with foreign governments,” said Amnesty International director of law and policy Mike Bostock. “Secret rules are woefully inadequate.”
Liberty’s legal director James Welsh said the tribunal submissions contradicted public statements from the government.
“The line the Government took at the hearing was that there were adequate safeguards, they just couldn’t be made public,” he said. “Leaving aside whether secret safeguards can ever be adequate, this reluctantly-made disclosure suggests otherwise.”
Last week, the foreign secretary, Phillip Hammond, told parliament’s Intelligence and Security Committee he expected that minister who signed surveillance warrants would likely have to justify themselves in front of a public inquiry at some point in the future.
“I’m sure I can speak for all of my colleague who sign warrants that we all have, in the back of our minds, that at some point in the future we will – not might be, but will – be appearing before some inquiry or tribunal or court accounting for the decisions that we’ve made and essentially accounting for the way we’ve applied the proportionality and necessity tests,” he said.
Hammond was also criticised for some of his answers to the committee, with experts suggesting the foreign secretary appeared not to understand the legal framework for the warrants he was signing , following a mischaracterisation of which types of communication would or would not require individual warrants.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:FBI demands new powers to hack into computers and carry out surveillance
Agency requests rule change but civil liberties groups say ‘extremely invasive’ technique amounts to unconstitutional power grab
The FBI is attempting to persuade an obscure regulatory body in Washington to change its rules of engagement that would grant it significant new powers to hack into and carry out surveillance of computers throughout the US and around the world.
Civil liberties groups warn that the proposed rule change amounts to a power grab by the agency that would ride roughshod over strict limits to searches and seizures laid out under the fourth amendment of the US constitution, as well as violating first amendment privacy rights. They have protested that the FBI is seeking to transform its cyber capabilities with minimal public debate and with no congressional oversight.
The regulatory body to which the Department of Justice has applied to make the rule change, the advisory committee on criminal rules, will meet for the first time on November 5 to discuss the issue. The panel will be addressed by a slew of technology experts and privacy advocates concerned about the possible ramifications were the proposals allowed to go into effect next year.
“This is a giant step forward for the FBI’s operational capabilities, without any consideration of the policy implications. To be seeking these powers at a time of heightened international concern about US surveillance is an especially brazen and potentially dangerous move,” said Ahmed Ghappour, an expert in computer law at UC Hastings college of the law who will be addressing next week’s hearing.
The proposed operating changes related to rule 41 of the federal rules of criminal procedure, the terms under which the FBI is allowed to conduct searches under court-approved warrants. Under existing wording, warrants have to be highly focused on specific locations where suspected criminal activity is occurring and approved by judges located in that same district.
But under the proposed amendment, a judge can issue a warrant that would allow the FBI to hack into any computer, no matter where it is located. The change is designed specifically to help federal investigators carry out surveillance on computers that have been “anonymized” – that is, their location has been hidden using tools such as Tor.
The amendment inserts a clause that would allow a judge to issue warrants to gain “remote access” to computers “located within or outside that district” (emphasis added) in cases in which the “district where the media or information is located has been concealed through technological means”. The expanded powers to stray across district boundaries would apply to any criminal investigation, not just to terrorist cases as at present.
Were the amendment to be granted by the regulatory committee the FBI would have the green light to unleash its capabilities – known as “network investigative techniques” – on computers across America and beyond. The techniques involve clandestinely installing malicious software, or malware, onto a computer that in turn allows federal agents effectively to control the machine, downloading all its digital contents, switching its camera or microphone on or off, and even taking over other computers in its network.
“This is an extremely invasive technique,” said Chris Soghoian, principal technologist of the American Civil Liberties Union, who will also be addressing the hearing. “We are talking here about giving the FBI the green light to hack into any computer in the country or around the world.”
A glimpse into the kinds of operations that could multiply under the new powers was gained this week when Soghoian discovered from documents obtained by the Electronic Frontier Foundation that in 2007 the FBI had faked an Associated Press story as a ruse to insert malware into the computer of a US-based bomb plot suspect. The revelation prompted angry responses from the AP and from the Seattle Times, whose name was also invoked in the documents, though the FBI said it had not in the end imitated the newspaper.
Civil liberties and privacy groups are particularly alarmed that the FBI is seeking such a huge step up in its capabilities through such an apparently backdoor route. Soghoian said of next week’s meeting: “This should not be the first public forum for discussion of an issue of this magnitude.”
Jennifer Granick, director of civil liberties at the Stanford center for internet and society, said that “this is an investigative technique that we haven’t seen before and we haven’t thrashed out the implications. It absolutely should not be done through a rule change – it has to be fully debated publicly, and Congress must be involved.”
Ghappour has also highlighted the potential fall-out internationally were the amendment to be approved. Under current rules, there are no fourth amendment restrictions to US government surveillance activities in other countries as the US constitution only applies to domestic territory.
However, the US government does accept that it should only carry out clandestine searches abroad where the fourth amendment’s “basic requirement of reasonableness” applies. In a letter setting out its case for the Rule 41 reform, the department of justice states that new warrants issued to authorise FBI hacking into computers whose location was unknown would “support the reasonableness of the search”.
Ghappour fears that such a statement amounts to “possibly the broadest expansion of extraterritorial surveillance power since the FBI’s inception”. He told the Guardian that “for the first time the courts will be asked to issue warrants allowing searches outside the country”.
He warned that the diplomatic consequences could be serious, with short-term FBI investigations undermining the long-term international relationship building of the US state department. “In the age of cyber attacks, this sort of thing can scale up pretty quickly.”
Another insight into the expansive thrust of US government thinking in terms of its cyber ambitions was gleaned recently in the prosecution of Ross Ulbricht, the alleged founder of the billion-dollar drug site the Silk Road. Experts suspect that the FBI hacked into the Silk Road server, that was located in Reykjavik, Iceland, though the agency denies that.
In recent legal argument, US prosecutors claimed that even if they had hacked into the server without a warrant, it would have been justified as “a search of foreign property known to contain criminal evidence, for which a warrant was not necessary”.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Brazil Is Keeping Its Promise to Avoid the U.S. Internet
Brazil was not bluffing last year, when it said that it wanted to disconnect from the United States-controlled internet due to the NSA's obscenely invasive surveillance tactics. The country is about to stretch a cable from the northern city of Fortaleza all the way to Portugal, and they've vowed not to use a single U.S. vendor to do it.
At first glance, Brazil's plan to disconnect from the U.S. internet just seemed silly. The country was not happy when news emerged that the NSA's tentacles stretched all the way down to Brazil. And the country was especially not happy when news emerged that the NSA had been spying on the Brazilian government's email for years. But really, what are you gonna do?
Brazil made a bunch of bold promises, ranging in severity from forcing companies like Facebook and Google to move their servers inside Brazilian borders, to building a new all-Brazilian email system—which they've already done. But the first actionable opportunity the country was presented with is this transatlantic cable, which had been in the works since 2012 but is only just now seeing construction begin. And with news that the cable plan will not include American vendors, it looks like Brazil is serious; it's investing $185 million on the cable project alone. And not a penny of that sum will go to an American company.
The implications of Brazil distancing itself from the US internet are huge. It's not necessarily a big deal politically, but the economic consequences could be tremendously destructive. Brazil has the seventh largest economy in the world, and it continues to grow. So when Brazil finally does divorce Uncle Sam—assuming things continue at this rate—a huge number of contracts between American companies and Brazil will simply disappear. On the whole, researchers estimate that the United States could lose about $35 billion due to security fears. That's a lot of money.
We knew there would be backlash to the Snowden leaks, but it's not just political; Edward Snowden cost the United States a lot of money, even if that wasn't his plan. Yet here we are, waving goodbye to information technology revenues from one of the world's largest countries. Still, that's a small price to pay for knowing just how little privacy we've had all along.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:GCHQ chief accuses US tech giants of becoming terrorists' 'networks of choice'
New director of UK eavesdropping agency accuses US tech firms of becoming ‘networks of choice’ for terrorists
Privacy has never been “an absolute right”, according to the new director of GCHQ, who has used his first public intervention since taking over at the helm of Britain’s surveillance agency to accuse US technology companies of becoming “the command and control networks of choice” for terrorists.
Robert Hannigan said a new generation of freely available technology has helped groups like Islamic State (Isis) to hide from the security services and accuses major tech firms of being “in denial”, going further than his predecessor in seeking to claim that the leaks of Edward Snowden have aided terror networks.
GCHQ and sister agencies including MI5 cannot tackle those challenges without greater support from the private sector, “including the largest US technology companies which dominate the web”, Hannigan argued in an opinion piece written for the Financial Times just days into his new job.
Arguing that GCHQ needed to enter into the debate about privacy, Hannigan said: “I think we have a good story to tell. We need to show how we are accountable for the data we use to protect people, just as the private sector is increasingly under pressure to show how it filters and sells its customers’ data.
“GCHQ is happy to be part of a mature debate on privacy in the digital age. But privacy has never been an absolute right and the debate about this should not become a reason for postponing urgent and difficult decisions.”
Hannigan, who was born in Gloucestershire, not far from GCHQ’s base, has advised the prime minister on counter-terrorism, intelligence and security policy, goes on to take aim at the role of major technology companies. A senior Foreign Office official, Hannigan succeeded Sir Iain Lobban at the Cheltenham-based surveillance agency.
While not naming any company in particular, the GCHQ director writes: “To those of us who have to tackle the depressing end of human behaviour on the internet, it can seem that some technology companies are in denial about its misuse.
“I suspect most ordinary users of the internet are ahead of them: they have strong views on the ethics of companies, whether on taxation, child protection or privacy; they do not want the media platforms they use with their friends and families to facilitate murder or child abuse.”
Hannigan asserts that the members of the public “know” the internet grew out of the values of western democracy and insists that customers of the technology firms he criticises would be “comfortable with a better, more sustainable relationship between the agencies and the technology companies.”
Heading towards the 25th anniversary of the creation of the world wide web, he calls for a “new deal” between democratic governments and the technology companies in the area of protecting citizens.
“It should be a deal rooted in the democratic values we share. That means addressing some uncomfortable truths. Better to do it now than in the aftermath of greater violence.”
In the same piece, Hannigan says Isis differs from its predecessors in the security of its communications, presenting an even greater challenge to the security services.
He writes: “Terrorists have always found ways of hiding their operations. But today mobile technology and smartphones have increased the options available exponentially.
“Techniques for encrypting messages or making them anonymous which were once the preserve of the most sophisticated criminals or nation states now come as standard. These are supplemented by freely available programs and apps adding extra layers of security, many of them proudly advertising that they are ‘Snowden approved’. There is no doubt that young foreign fighters have learnt and benefited from the leaks of the past two years.”
Among the advocates of privacy protection who reacted to Hannigan’s comments, the deputy director of Privacy International, Eric King, said: “It’s disappointing to see GCHQ’s new director refer to the internet – the greatest tool for innovation, access to education and communication humankind has ever known – as a command-and-control network for terrorists.”
King added: “Before he condemns the efforts of companies to protect the privacy of their users, perhaps he should reflect on why there has been so much criticism of GCHQ in the aftermath of the Snowden revelations. GCHQ’s dirty games – forcing companies to handover their customers’ data under secret orders, then secretly tapping the private fibre optic cables between the same companies’ data centres anyway – have lost GCHQ the trust of the public, and of the companies who services we use. Robert Hannigan is right, GCHQ does need to enter the public debate about privacy - but attacking the internet isn’t the right way to do it.”
The Electronic Frontier Foundation (EFF) meanwhile rejected the notion that an agreement between companies and governments was needed.
Jillian York, director of international free expression at EFF said: “A special “deal” between governments and companies isn’t necessary - law enforcement can conduct open source intelligence on publicly-posted content on social networks, and can already place legal requests with respect to users. Allowing governments special access to private content is not only a violation of privacy, it may also serve to drive terrorists underground, making the job of law enforcement even more difficult.”
Welcoming Hannigan’s participation in the public debate, the Labour Party MP Tom Watson said it helped to map out where we should draw the line on privacy and helps the same agencies “to rebuild their legitimacy post-Snowden”.
But he added: “I hope they do not confuse the use of public propaganda through social media by extremists with the use of the covert communications. It is illogical to say that because Isis use Twitter, all our metadata should be collected without warrant.”
Hannigan’s comments come after the director of the FBI, James Comey, called for “a regulatory or legislative fix” for technology companies’ expanding use of encryption to protect user privacy.
Reacting last month to the introduction of strong default encryption by Apple and Google on their latest mobile operating systems, Comey said “the post-Snowden pendulum has swung too far in one direction - in a direction of fear and mistrust.”
“Justice may be denied because of a locked phone or an encrypted hard drive,” said Comey. Without a compromise, “homicide cases could be stalled, suspects could walk free, and child exploitation victims might not be identified or recovered.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Federal Judge Says Public Has a Right to Know About FBI’s Facial Recognition Database
A federal judge has ruled that the FBI's futuristic facial-recognition database is deserving of scrutiny from open-government advocates because of the size and scope of the surveillance technology.
U.S. District Judge Tanya Chutkan said the bureau's Next Generation Identification program represents a "significant public interest" due to concerns regarding its potential impact on privacy rights and should be subject to rigorous transparency oversight.
"There can be little dispute that the general public has a genuine, tangible interest in a system designed to store and manipulate significant quantities of its own biometric data, particularly given the great numbers of people from whom such data will be gathered," Chutkan wrote in an opinion released late Wednesday.
Her ruling validated a Freedom of Information Act lawsuit filed by the Electronic Privacy Information Center that last year made a 2010 government report on the database public and awarded the group nearly $20,000 in attorneys' fees. That government report revealed the FBI's facial-recognition technology could fail up to 20 percent of the time. Privacy groups believe that failure rate may be even higher, as a search can be considered successful if the correct suspect is listed within the top 50 candidates.
"The opinion strongly supports the work of open-government organizations and validates their focus on trying to inform the public about government surveillance programs," said Jeramie Scott, national security counsel with EPIC.
Privacy groups, including EPIC, have long assailed Next Generation Identification, which they argue could be used as an invasive means of tracking that collects images of people suspected of no wrongdoing. The program—a biometric database that includes iris scans and palm prints along with facial recognition—became "fully operational" this summer, despite not undergoing an internal review, known as a Privacy Impact Assessment, since 2008. Government officials have repeatedly pledged they would complete a new privacy audit.
FBI Director James Comey has told Congress that the database would not collect or store photos of ordinary citizens, and instead is designed to "find bad guys by matching pictures to mug shots." But privacy groups contend that the images could be shared among the FBI and other agencies, including the National Security Agency, and even with state motor-vehicle departments.
In his testimony, given in June, Comey did not completely refute that database information could potentially be shared with states, however.
Government use of facial-recognition technology has undergone increasing scrutiny in recent years, as systems once thought to exist only in science fiction movies have become reality. TheNew York Times reported on leaks from Edward Snowden revealing that the NSA intercepts "millions of images per day" across the Internet as part of an intelligence-gathering program that includes a daily cache of some 55,000 "facial-recognition quality images."
The Justice Department did not immediately return a request for comment regarding whether it will appeal Chutkan's decision.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Internet Architecture Boardquote:IAB Statement on Internet Confidentiality
IAB Statement on Internet Confidentiality
In 1996, the IAB and IESG recognized that the growth of the Internet
depended on users having confidence that the network would protect
their private information. RFC 1984 documented this need. Since that
time, we have seen evidence that the capabilities and activities of
attackers are greater and more pervasive than previously known. The IAB
now believes it is important for protocol designers, developers, and
operators to make encryption the norm for Internet traffic. Encryption
should be authenticated where possible, but even protocols providing
confidentiality without authentication are useful in the face of
pervasive surveillance as described in RFC 7258.
Newly designed protocols should prefer encryption to cleartext operation.
There may be exceptions to this default, but it is important to recognize
that protocols do not operate in isolation. Information leaked by one
protocol can be made part of a more substantial body of information
by cross-correlation of traffic observation. There are protocols which
may as a result require encryption on the Internet even when it would
not be a requirement for that protocol operating in isolation.
We recommend that encryption be deployed throughout the protocol stack
since there is not a single place within the stack where all kinds of
communication can be protected.
The IAB urges protocol designers to design for confidential operation by
default. We strongly encourage developers to include encryption in their
implementations, and to make them encrypted by default. We similarly
encourage network and service operators to deploy encryption where it is
not yet deployed, and we urge firewall policy administrators to permit
encrypted traffic.
We believe that each of these changes will help restore the trust users
must have in the Internet. We acknowledge that this will take time and
trouble, though we believe recent successes in content delivery networks,
messaging, and Internet application deployments demonstrate the
feasibility of this migration. We also acknowledge that many network
operations activities today, from traffic management and intrusion
detection to spam prevention and policy enforcement, assume access to
cleartext payload. For many of these activities there are no solutions
yet, but the IAB will work with those affected to foster development of
new approaches for these activities which allow us to move to an Internet
where traffic is confidential by default.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Judge threatens detective with contempt for declining to reveal cellphone tracking methods
Baltimore prosecutors withdrew key evidence in a robbery case Monday rather than reveal details of the cellphone tracking technology police used to gather it.
The surprise turn in Baltimore Circuit Court came after a defense attorney pressed a city police detective to reveal how officers had tracked his client.
City police Det. John L. Haley, a member of a specialized phone tracking unit, said officers did not use the controversial device known as a stingray. But when pressed on how phones are tracked, he cited what he called a "nondisclosure agreement" with the FBI.
"You don't have a nondisclosure agreement with the court," Baltimore Circuit Judge Barry G. Williams replied. Williams threatened to hold Haley in contempt if he did not respond. Prosecutors decided to withdraw the evidence instead.
The tense exchange during a motion to suppress evidence in the robbery trial of 16-year-old Shemar Taylor was the latest confrontation in a growing campaign by defense attorneys and advocates for civil liberties nationwide to get law enforcement to provide details of their phone tracking technology, and how and when they use it.
Law enforcement officials in Maryland and across the country say they are prohibited from discussing the technology at the direction of the federal government, which has argued that knowledge of the devices would jeopardize investigations.
"Courts are slowly starting to grapple with these issues," said Nathan Freed Wessler, an attorney with the American Civil Liberties Union who is tracking stingray cases. "What we're talking about is basic information about a very commonly used police tool, but because of the extreme secrecy that police have tried to invoke, there are not many court decisions about stingrays."
Defense attorney Joshua Insley still believes that police used a stingray to find Taylor. He cited a letter in which prosecutors said they were prohibited by the Department of Justice from disclosing information about methods used in their investigation.
The portable device was developed for the military to help zero in on cellphones. It mimics a cellphone tower to force nearby phones to connect to it.
Records shows that the Baltimore Police Department purchased a stingray for $133,000 in 2009.
Some critics say the use of such technology might be appropriate, with court approval, to help law enforcement locate a suspect. But in the secrecy surrounding its use, they say, it's not always clear that law enforcement officials have secured the necessary approval, or stayed within their bounds.
They also express concern for the privacy of other cellphones users whose data are caught up in a search.
In the case before the court Monday, two teens are accused of robbing a Papa John's pizza delivery driver at gunpoint in April.
Police say phone records show that the phone that was used to call in the delivery was also used to make and receive hundreds of calls to and from Taylor's phone. Police believe the first phone belonged to Taylor's co-defendant. They say Taylor confessed after he was arrested.
Taylor is being tried as an adult. The other suspect is being tried as a juvenile.
In court Monday, the robbery detective who prepared the warrant to search Taylor's home testified that members of the department's Advanced Technical Team did a "ride-by" — described in court papers as "sophisticated technical equipment" — to determine one of the phones was inside the home. Detective Alan Savage said he did not know what technology or techniques the unit employs.
The defense then called Haley to the stand. He said police can use data from the cellphone companies to locate phones in real time.
Insley asked Haley whether police can ascertain a phone's location "independently," without the help of a phone company. Haley said yes.
When asked how, he balked.
"I wouldn't be able to get into that," Haley said.
Insley tried again later. Haley responded that police can get GPS location data from phone companies.
"Then there's equipment we would use that I'm not going to discuss that would aid us in that investigation," Haley said.
Williams, the judge, instructed Haley to answer the question. Haley invoked the nondisclosure agreement.
"I can't. I'm sorry. I can't," Haley said.
Williams called Insley's question "appropriate," and threatened to hold Haley in contempt if he did not answer.
Haley demurred again, and Assistant State's Attorney Patrick R. Seidel conferred with other prosecutors in court to observe the hearing.
Finally, Seidel said prosecutors would drop all evidence found during the search of the home — including, authorities have said, a .45-caliber handgun and the cellphone. The prosecutor said the state would continue to pursue the charges.
Wessler, of the ACLU, said Williams was right to ignore the nondisclosure agreement with the FBI.
"You can't contract out of constitutional disclosure obligations," Wessler said. "A secret written agreement does not invalidate the Maryland public records law [and] does not invalidate due process requirements of giving information to a criminal defendant."
Attorneys say they have suspected for years that police were employing secret methods to track cellphones. But only recently have they begun to find what they believe are clear examples.
Police and prosecutors in another case ran into a similar problem in September, when they were asked to reveal how a cellphone was tracked.
Sgt. Scott Danielczyk, another member of the Advanced Technical Team, testified in that home invasion case — also before Judge Williams — that police used data from a court order to track a cellphone to the general area of the 1400 block of E. Fayette St.
Danielczyk and three other members of the unit were tasked to "facilitate finding it," he testified, and determined the phone was in the possession of someone on a bus.
Williams asked how Danielczyk concluded the phone was being carried by the suspect.
"Um, we had information that he had the property on him," the officer said.
Williams pressed.
"This kind of goes into Homeland Security issues, your honor," Danielczyk said.
"If it goes into Homeland Security issues, then the phone doesn't come in," Williams said. "I mean, this is simple. You can't just stop someone and not give me a reason."
In that case, too, the phone evidence is no longer in play. Prosecutors are proceeding without it.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:The “USA Freedom Act” – which its proponents were heralding as “NSA reform” despite its suffocatingly narrow scope – died in the august U.S. Senate last night when it attracted only 58 of the 60 votes needed to close debate. All Democratic and independent Senators except one (Bill Nelson of Florida) voted in favor, as did three tea-party GOP Senators (Ted Cruz, Mike Lee and Dean Heller). One GOP Senator, Rand Paul, voted against it on the ground that it did not go nearly far enough in reining in the NSA. On Monday, the White House issued a statement “strongly supporting” the bill.
The “debate” among the Senators that preceded the vote was darkly funny and deeply boring, in equal measure. The black humor was due to the way one GOP Senator after the next – led by ranking Senate Intelligence Committee member Saxby Chambliss (pictured above) – stood up and literally screeched about 9/11 and ISIS over and over and over, and then sat down as though they had made a point. Their scary script was unveiled earlier that morning by a Wall Street Journal op-ed by former Bush Attorney General Mike Mukasey and former CIA and NSA Director Mike Hayden warning that NSA reform would make the terrorists kill you; it appeared under this Onion-like headline:
So the pro-NSA Republican Senators were actually arguing that if the NSA were no longer allowed to bulk-collect the communication records of Americans inside the U.S., then ISIS would kill you and your kids. But because they were speaking in an empty chamber and only to their warped and insulated D.C. circles and sycophantic aides, there was nobody there to cackle contemptuously or tell them how self-evidently moronic it all was. So they kept their Serious Faces on like they were doing The Nation’s Serious Business, even though what was coming out of their mouths sounded like the demented ramblings of a paranoid End is Nigh cult.
quote:There is a real question about whether the defeat of this bill is good, bad, or irrelevant. To begin with, it sought to change only one small sliver of NSA mass surveillance (domestic bulk collection of phone records under section 215 of the Patriot Act) while leaving completely unchanged the primary means of NSA mass surveillance, which takes place under section 702 of the FISA Amendments Act, based on the lovely and quintessentially American theory that all that matters are the privacy rights of Americans (and not the 95% of the planet called “non-Americans”).
There were some mildly positive provisions in the USA Freedom Act: the placement of “public advocates” at the FISA court so that someone contests the claims of the US Government; the prohibition on the NSA holding Americans’ phone records, requiring instead that they obtain FISA court approval before seeking specific records from the telecoms (which already hold those records for at least 18 months); and reducing the agency’s “contact chaining” analysis from three hops to two. One could reasonably argue (as the ACLU and EFF did) that, though woefully inadequate, the bill was a net-positive as a first step toward real reform, but one could also reasonably argue, as Marcy Wheeler has with characteristic insight, that the bill is so larded with ambiguities and fundamental inadequacies that it would forestall better options and advocates for real reform should thus root for its defeat.
When pro-privacy members of Congress first unveiled the bill many months ago, it was actually a good bill: real reform. But the White House worked very hard – in partnership with the House GOP – to water that bill down so severely that what the House ended up passing over the summer did more to strengthen the NSA than rein it in, which caused even the ACLU and EFF to withdraw their support. The Senate bill rejected last night was basically a middle ground between that original, good bill and the anti-reform bill passed by the House.
All of that illustrates what is, to me, the most important point from all of this: the last place one should look to impose limits on the powers of the U.S. Government is . . . the U.S. Government. Governments don’t walk around trying to figure out how to limit their own power, and that’s particularly true of empires.
quote:Those who like to claim that nothing has changed from the NSA revelations simply ignore the key facts that negate that claim, including the serious harm to the U.S. tech sector from these disclosures, driven by the newfound knowledge that U.S. companies are complicit in mass surveillance. Obviously, tech companies don’t care at all about privacy, but they care a lot about that.
quote:Increased individual encryption use is a serious impediment to NSA mass surveillance: far stronger than any laws the U.S. Congress might pass. Aside from the genuine difficulty the agency has in cracking well-used encryption products, increased usage presents its own serious problem. Right now, the NSA – based on the warped mindset that anyone who wants to hide what they’re saying from the NSA is probably a Bad Person – views “encryption usage” as one of its key factors in determining who is likely a terrorist. But that only works if 10,000 people around the world use encryption. Once that number increases to 1 million, and then to 10 million, and then to default usage, the NSA will no longer be able to use encryption usage as a sign of Bad People. Rather than being a red flag, encryption will simply be a brick wall: one that individuals have placed between the snooping governments and their online activities. That is a huge change, and it is coming.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:'Brits telecombedrijf was betrokken bij afluisterschandaal NSA'
Een groot telecombedrijf uit Groot-BrittanniŰ heeft een belangrijke rol gespeeld in het afluisterschandaal rond de Amerikaanse inlichtingendiensten NSA, dat werd onthuld door Edward Snowden.
Dat meldt het Britse Channel 4 News.
Het zou gaan om een bedrijf dat in juli 2012 is overgenomen door Vodafone: Cable and Wireless.
De Britse tv-zender zou door Snowden gelekte documenten hebben ingezien. Daaruit blijkt dat het bedrijf onderdeel was van een geheim project, waarvoor bedrijven grote hoeveelheden internetverkeer verzamelden: een kwart van dat verkeer loopt door het Verenigd Koninkrijk.
De Britse inlichtingendienst GCHQ zou volgens Channel 4 News met particuliere bedrijven zoals Cable and Wireless een soort geheime vennootschappen hebben ontwikkeld. De bedrijven werden vermeld onder codenamen. Zo heette Cable and Wireless 'Gerontic'.
Het bedrijf zou de GCHQ onder andere hebben geholpen bij het testen van afluisterapparatuur. Cable and Wireless zou zelfs een medewerker van de Britse inlichtingendienst in voltijd-dienst hebben.
Ook zou het bedrijf ervoor hebben gezorgd dat Britse spionnen de privÚ-communicatie van miljoenen internetgebruikers over de hele wereld konden verzamelen.
Vodafone
In een reactie benadrukte Vodafone dat de GCHQ nooit directe toegang tot haar netwerk is verleend. Volgens het telecombedrijf had de inlichtingendienst enkel toegang tot de klantengegevens kunnen krijgen met toestemming van Vodafone zelf. Dat zou ook gelden voor andere telecombedrijven.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Plasterk: diensten moeten kabelgebonden data kunnen onderscheppen
Het kabinet wil de bevoegdheden van de inlichtingendiensten verruimen. Ook communicatie via de kabel zou in de toekomst massaler mogen worden onderschept. Wel moet dat doelgericht en stapsgewijs gebeuren.
quote:Met het langverwachte voorstel geeft het kabinet gevolg aan de commissie-Dessens, die in december vorig jaar concludeerde dat de huidige spionagewet achterhaald is. Daarin wordt onderscheid gemaakt tussen kabelgebonden en draadloze communicatie. Nu mag het verkeer alleen in het laatste geval (als het via satellieten of portofoons verloopt) in 'bulk' worden onderschept. Dit terwijl 90 procent van de communicatie tegenwoordig via de kabel gaat (denk aan communicatie via internet en smartphone). Dat onderscheid zal straks verdwijnen.
NSA
De verruiming zal door privacyvoorvechters met argusogen worden bekeken. Hiermee krijgen de Nederlandse diensten AIVD en MIVD wettelijke mogelijkheden die enigszins lijken op de praktijken van de Amerikaanse inlichtingendienst NSA, die zijn sleepnetten ongebreideld over de wereld kon uitwerpen.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:In juni begon een commissie een onderzoek naar de praktijken. 'De uitkomst is nul. Het is hete lucht. Er zijn geen feiten', aldus de bron binnen Openbaar Ministerie.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Edward Snowden: state surveillance in Britain has no limits
Whistleblower and former NSA analyst says UK regulation allows GCHQ snooping to go beyond anything seen in US
The UK authorities are operating a surveillance system where “anything goes” and their interceptions are more intrusive to people’s privacy than has been seen in the US, Edward Snowden said.
Speaking via Skype at the Observer Ideas festival, held in central London, the whistleblower and former National Security Agency specialist, said there were “really no limits” to the GCHQ’s surveillance capabilities.
He said: “In the UK … is the system of regulation where anything goes. They collect everything that might be interesting. It’s up to the government to justify why it needs this. It’s not up to you to justify why it doesn’t … This is where the danger is, when we think about … evidence being gathered against us but we don’t have the opportunity to challenge that in courts. It undermines the entire system of justice.”
He also said he thought that the lack of coverage by the UK papers of the story, or the hostile coverage of it, other than by the Guardian, “did a disservice to the public”.
His appearance at the festival on Sunday marked the end of a weekend of almost frenetic social activity by his highly reclusive standards: he appeared at two public events and was the absent star of Laura Poitras’ documentary, Citizenfour, which premiered in New York on Friday.
Collectively, the events revealed a more rounded, human, portrait of the former NSA analyst than had been seen before, and offered a few telling glimpses of what his life was now like in Moscow.
The coverage revealed that Snowden does not drink alcohol, has never been drunk, and that he misses his “old beat-up car”. He also revealed that he has got a job, working on “a very significant grant for a foundation” on a project “for the benefit of the press and journalists working in threatened areas”.
Poitras’ documentary included the revelation that his girlfriend, Lindsay Mills, had joined him in Moscow, and at the New Yorker festival on Saturday he was asked by a member of the audience if “she had been mad” at him given that he had left without warning to find a refuge.
She was not “entirely pleased” he said. “But at the same time it was an incredible reunion because she understood and that meant a lot to me. Although she had a very, very, challenging year. and I leave it to her to discuss that when and if she is ever ready. It was a meeting I’ll never forget.”
A member of the audience at Observer Ideas pointed out that he had been living in paradise with a dancer for a girlfriend and asked, are you mad? He laughed and talked about all the things that he had given up: his job, his home, his family. “And I can’t return to the home country and that’s a lot to give up.”
But, he said: “What kind of world do we want to live in? Do you want to live in a world in which governments make decisions behind closed doors? And when you ask me, I say no.”
He also issued his strongest warning yet about how Silicon Valley firms were compromising the privacy of the public. Google and Facebook, he said, were “dangerous services”. His strongest condemnation was against Dropbox and urged erasure of it from computers. It encrypted your data, he told the audience, but kept the key and would give that to any government which asked.
The irony of the fact that he was appearing via Google Hangout and Skype was not lost on the audience. Later, he said: “No kidding, right? I’m about to disconnect this machine and toss it into a fire, though.”
His more serious point was that he said he believed the battle against the intrusions of big corporations into privacy was a much harder battle to win than the governments’.
He said later: “The unexplored elephant is the corporations – so privileged, so powerful in access, so unregulated – [and] are then tapped by the government.[…] I don’t think it’s unreasonable to think that major corporations have a hand in setting government policy today. Certainly in the US, given our campaign finance issues.”
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:Hackers targeted and hacked Ecuador President Rafael Correa’s computers and internet systems on 20th November. Telesur, the official Ecuadorian press agency said that the attacks were carried out through out the day on 2oth November. Meanwhile President Correa has alleged that American spy agencies are behind the attacks.
quote:He accused the US of “systematic, high-tech” cyber-attacks on his private internet accounts and computers which according to him were was traced back to American servers.
quote:Though President Correa gave very few details in the Twitter posts except the fact that they were systematic attacks with high technology and very huge resources, the Latin media was more forthcoming on this issue. Telesur said that the attacks carried on throughout all of last Thursday, November 20, and that they are an American effort. Another paper which carries President weekly broadcast called Citizen Link no.399 stated,
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:koenrh twitterde op zondag 23-11-2014 om 21:41:58 Q&A with Laura Poitras, Sarah Harrison, Jacob Appelbaum after the Dutch premiere of Citizenfour. #IDFA http://t.co/1qcppLVOwO reageer retweet
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Latest Snowden leak shows UK, US behind Regin malware, attacked European Union
Blame the British and American spy agencies for the latest state-sponsored malware attack, say reporters at The Intercept.
The publication, which in the wake of Glenn Greenwald's departure from The Guardian continued to publish documents leaked by Edward Snowden, said on Monday the recently discovered malware, known as Regin, was used against targets in the European Union.
One of those targets included Belgian telecommunications company Belgacom, which had its networks broken into by the British spy agency the Government Communications Headquarters (GCHQ).
Regin was first publicly talked about over the weekend after Symantec discovered the "sophisticated" malware, though is understood to have been in circulation since 2008.
Compared to Stuxnet, the state-sponsored malware whose creators have never been confirmed, the recently-discovered trojan steals data from machines and networks it infects, disguised as Microsoft software.
Some began to point the finger at Russia and China, but these were quickly discounted by industry experts. Others suspected the U.S. and Israel — a deal already exists that allows the Middle Eastern allied state to access raw and "unchecked" U.S. collected intelligence.
They weren't far off. According to Monday's report, the U.S. working in conjunction with Britain, a European member state (though perhaps not for much longer) attacked Belgacom using the Regin malware.
Though the Belgacom hack was disclosed by Snowden's leaks, the malware used had never been revealed.
The new details from The Intercept show how GCHQ embarked upon its "hacking mission," known as Operation Socialist, by accessing Belgacom's networks in 2010. By targeting engineers through a faked LinkedIn page, GCHQ was able to get deep inside the Internet provider to steal data.
One of Belgacom's main clients was the European Commission, the European Parliament, and the European Council of member state leaders.
Exactly how member states of the European Union — there are 28 of them including the U.K. — will react to one of its own member states launching a successful hacking attack against their executive body, remains unknown.
But while members of the Parliament and Commission staff have, over the years, seen the U.S. as one of the greatest threats to the region's data protection and privacy policies, they should have been looking a little closer to home.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


twitter:e3i5 twitterde op dinsdag 25-11-2014 om 15:15:43 Wow. Full list of undersea fibre optic cables GCHQ is accessing has been published. http://t.co/hsMtCcMHiC http://t.co/ZqpJpkXpqA reageer retweet
quote:
Het artikel gaat verder.quote:Previously unpublished documents show how the UK telecom firm Cable & Wireless, acquired by Vodafone in 2012, played a key role in establishing one of the Government Communications Headquarters’ (GCHQ) most controversial surveillance programs.
A joint investigation by NDR, WDR, SŘddeutsche Zeitung and Channel 4 based on documents leaked by whistleblower Edward Snowden, reveals that Cable & Wireless actively shaped and provided the most data to GCHQ mass surveillance programs, and received millions of pounds in compensation. The documents also suggest that Cable & Wireless assisted GCHQ in breaking into a competitor’s network.
In response to these allegations, Vodafone said that an internal investigation found no evidence of unlawful conduct, but the company would not deny it happened.
"What we have in the UK is a system based on warrants, where we receive a lawful instruction from an agency or authority to allow them to have access to communications data on our network. We have to comply with that warrant and we do and there are processes for us to do that which we’re not allowed to talk about because the law constrains us from revealing these things. We don’t go beyond what the law requires” a Vodafone spokesperson told Channel 4.
In August 2013 SŘddeutsche Zeitung and NDR first named Vodafone as one of the companies assisting the GCHQ. Reports that Vodafone secretly provided customer data to intelligence agencies damaged the company’s relation to German customers. Few months later Der Spiegel reported that the NSA had spied on Chancellor Angela Merkel, whose cell phone was on a Vodafone contract.
This could be a coincidence. No evidence suggests that Vodafone was involved in the “Merkelphone” scandal. But unlike Facebook, Yahoo, or other companies forced to cooperate with the intelligence services, Vodafone has yet to challenge the GCHQ publicly. Konstantin von Notz, a German member of the Bundestag for the Green Party, urges Vodafone to take legal action: „A company such as Vodafone, which has responsibility for so many customers, has to take a clear stand against these data grabs.“
Similarly, Vodafone has provided no explanation as to why GCHQ discussed “potential new deployment risks identified by GERONTIC” in June 2008. According to the Snowden-documents “GERONTIC” was the GCHQ codename for Cable & Wireless, and after acquisition in 2012 (at least for a while) presumably for Vodafone.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:German loophole allows BND spy agency to snoop on own people
Intelligence agency can legally intercept calls and emails from Germans working abroad for foreign firms, MPs discover
German MPs examining the surveillance activities the US National Security Agency have found a legal loophole that allows the Berlin’s foreign intelligence agency to spy on its own citizens.
The agency, known by its German acronym BND, is not usually allowed to intercept communications made by Germans or German companies, but a former BND lawyer told parliament this week that citizens working abroad for foreign companies were not protected.
The German government confirmed on Saturday that work-related calls or emails were attributed to the employer. As a result, if the employer is foreign, the BND could legally intercept them.
Opposition politicians have accused Angela Merkel’s government of pretending to be outraged about alleged spying by the NSA while condoning illegal surveillance itself.
The revelation comes after a BND employee was arrested in July on suspicion of selling secret documents to a CIA contact. Rather than report the contact to their allied German counterparts, the US spy agency was reported to have paid the agent Ą25,000 (ú20,000) for 218 documents classified as confidential or top secret.
The incident prompted Germany to consider stepping up its counter-espionage efforts. Possible measures include monitoring the intelligence activities of nominal Nato allies such as the US, Britain and France, and expelling US agents from Germany.
In June the BND officially revealed some of its worst-kept secrets by acknowledging that half a dozen facilities are in fact spy stations.
The agency had for decades maintained that it had nothing to do with sites bearing cryptic names such as the Ionosphere Institute, but amateur sleuths long suspected their true identities and posted them online.
At a ceremony in the Bavarian town of Bad Aibling, the agency’s chief, Gerhard Schindler, officially attached the BND’s logo to the entrance of a site previously called the Telecommunications Traffic Office of the German Armed Force.
The facility features several giant golf ball-shaped radio domes commonly used for eavesdropping on radio, data and phone traffic.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:UK Police Accidentally Sent Documents Admitting To Spying On Journalists To Newspaper, Asked Not To Publish
UK police in Cleveland accidentally sent documents revealing that it has used controversial anti-terror laws to spy on journalists who had not committed any crimes to an area newspaper.
The Cleveland Police “erroneously” sent information to industry paper the Press Gazette indicating that it had used the Regulation of Investigatory Powers Act (RIPA) to obtain telecommunications data while searching for a journalist’s source.
The publication reports that police asked them to delete the documents but says they were unwilling to do so because, “there is a strong public interest in disclosing it.”
RIPA, which regulates how authorities can intercept and monitor communications, is under increased scrutiny as it has emerged that at least four other U.K. police forces have used it to seize telecommunications data while hunting for journalists’ sources. The journalists affected have not been accused of any criminal wrongdoing.
Earlier this week it emerged that after the Metropolitan Police used RIPA to try and access the details of a single journalist in March after wireless carrier Vodafone accidentally provided the phone records of more than 1,500 users. Rather than deleting the data, the department analyzed it in a spreadsheet and stored it for seven months.”
In another incident, a local council used RIPA to follow and spy on a journalist meeting a source at a cafÚ as she investigated “allegations of wrongdoing within the council’s environmental services department,” ultimately “scuppering” her investigation.
Testifying before the Home Affairs Select Committee, the National Union of Journalists has also condemned police use of RIPA as “systemic,” arguing that it risks doing “irreparable damage.”
There is now an ongoing investigation into misuse of the Act by the Interception of Communications Commissioner’s Office (IOCCO), which is to be published in January 2015.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:Amazon’s frightening CIA partnership: Capitalism, corporations and our massive new surveillance state
When Internet retailer and would-be 21st century overlord Amazon.com kicked WikiLeaks off its servers back in 2010, the decision was not precipitated by men in black suits knocking on the door of one of Jeff Bezos’ mansions at 3 a.m., nor were any company executives awoken by calls from gruff strangers suggesting they possessed certain information that certain individuals lying next to them asking “who is that?” would certainly like to know.
Corporations, like those who lead them, are amoral entities, legally bound to maximize quarterly profits. And rich people, oft-observed desiring to become richer, may often be fools, but when it comes to making money even the most foolish executive knows there’s more to be made serving the corporate state than giving a platform to those accused of undermining national security.
The whistle-blowing website is “putting innocent people in jeopardy,” Amazon said in a statement released 24 hours after WikiLeaks first signed up for its Web hosting service. And the company wasn’t about to let someone use their servers for “securing and storing large quantities of data that isn’t rightfully theirs,” even if much of that data, leaked by Army private Chelsea Manning, showed that its rightful possessors were covering up crimes, including the murder of innocent civilians from Yemen to Iraq.
The statement was over the top — try as it might, not even the government has been able to point to a single life lost due to Manning’s disclosures — but, nonetheless, Amazon’s capitalist apologists on the libertarian right claimed the big corporation had just been victimized by big bad government. David Henderson, a research fellow at Stanford University’s Hoover Institution, explained that those calling for a boycott of Amazon were out of line, as the real enemy was “megalomaniacal Senator Joe Lieberman,” who had earlier called on Amazon to drop WikiLeaks (and is, admittedly, a rock-solid choice for a villain).
“The simple fact is that we live in a society whose governments are so big, so powerful, so intrusive, and so arbitrary, that we have to be very careful in dealing with them,” Henderson wrote. That Amazon itself cited a purported violation of its terms of service to kick WikiLeaks off its cloud was “a lie,” according to Henderson, meant to further protect Amazon from state retribution. Did it make him happy? No, of course not. “But boycotting one of the government’s many victims? No way.”
But Amazon was no victim. Henderson, like many a libertarian, fundamentally misreads the relationship between corporations and the state, creating a distinction between the two that doesn’t really exist outside of an intro-to-economics textbook. The state draws up the charter that gives corporations life, granting them the same rights as people — more rights, in fact, as a corporate person can do what would land an actual person in prison with impunity or close to it, as when Big Banana was caught paying labor organizer-killing, right-wing death squads in Colombia and got off with a fine.
Corporations are more properly understood not as victims of the state, but its for-profit accomplices. Indeed, Amazon was eager to help the U.S. government’s campaign against a website that — thanks almost entirely to Chelsea Manning — had exposed many embarrassing acts of U.S. criminality across the globe: the condoning of torture by U.S. allies in Iraq; the sexual abuse of young boys by U.S. contractors in Afghanistan; the cover-up of U.S. airstrikes in Yemen, including one that killed 41 civilians, 21 of them children. The decision to boot WikiLeaks was, in fact, one that was made internally, no pressure from the deep state required.
“I consulted people I knew fairly high up in the State Department off the record, and they said that they did not have to put pressure … on Amazon for that to happen,” said Robert McChesney, a professor of communication at the University of Illinois, in an appearance on “Democracy Now!.” “It was not a difficult sell.”
And it paid off. A little more than a year later, Amazon was awarded a generous $600 million contract from the CIA to build a cloud computing service that will reportedly “provide all 17 [U.S.] intelligence agencies unprecedented access to an untold number of computers for various on-demand computing, analytic, storage, collaboration and other services.” As The Atlantic noted, and as former NSA contractor Edward Snowden revealed, these same agencies collect “billions and perhaps trillions of pieces of metadata, phone and Internet records, and other various bits of information on an annual basis.”
That is to say: On Amazon’s servers will be information on millions of people that the intelligence community has no right to possess — Director of National Intelligence James Clapper initially denied the intelligence community was collecting such data for a reason — which is used to facilitate corporate espionage and drone strikes that don’t just jeopardize innocent lives, but have demonstrably ended hundreds of them.
Instead of helping expose U.S. war crimes, then, Amazon’s cloud service could be used to facilitate them, for which it will be paid handsomely — which was, in all likelihood, the whole point of the company proving itself a good corporate citizen by disassociating itself from an organization that sought to expose its future clients in the intelligence community.
“We look forward to a successful relationship with the CIA,” Amazon said in a 2013 statement after winning that long-sought contract (following a protracted battle for it with a similarly eager tech giant, IBM).
If it were more honest, Amazon might have said “We look forward to a successful relationship with the [coup d’Útat-promoting, drone-striking, blood-stained] CIA.”
And if it were more honest, Amazon could have said the same thing in 2010.
So long as there are giant piles of money to be made by systematically violating the privacy of the public (the CIA and NSA together enjoy a budget of over $25 billion), corporations will gladly lie in the same bed as those who created them, which is, yes, gross. Protecting consumer privacy is at best an advertising slogan, not a motivating principle for entities whose sole responsibility to shareholders is to maximize quarterly profits. This isn’t an admission of defeat — and when companies fear state-sanctioned invasions of privacy will cost them customers in the private sector or contracts with foreign states, they do sometimes roll back their participation — but a call to recognize the true villain: If we desire more than just an iPhone with encryption, we must acknowledge the issue is not just a few individual megalomaniacs we call senators, but a system called capitalism that systemically encourages this behavior.
In the 1970s, following the resignation of President Richard Nixon, the Church Committee exposed rampant spying on dissidents that was illegal even according to the loose legal standards of the time. Speeches were made, reforms were demanded and new laws were passed. The abuses, it was claimed, were relegated to history. What happened next? Look around: The total surveillance we enjoy today, enabled by high-tech military contractors including AT&T and Google and Verizon and every other nominally private tech company that capitalism encourages to value profits over privacy — a public-private partnership that grants those in power a means of spying on the powerless beyond the wildest dreams of any 20th century totalitarian. Sure, ostensibly communist states can of course be quite awful too, but the difference is that, in capitalist nations, the citizens actually place the eavesdropping devices in their own homes.
Now, whether the reforms of the 1970s were inadequate or were just plain ignored by those who were to be reformed is sort of beside the point; the status quo is what it is and, at least if one values privacy and the ability to organize and engage in political discussion and search the Internet without fear a spy agency or one of its contractors is monitoring it all in real-time, it sure isn’t good. So when groups such as the Electronic Frontier Foundation and progressive magazines such as The Nation call for “another Church Committee,” the question we ought to ask them is: “Fucking really?”
Abolishing capitalism is indeed a utopian goal, but when corporations routinely go above and beyond their legal duties to serve the state — granting police and intelligence agencies access to their customers’ data without so much as a judge’s rubberstamp on a warrant — expecting meaningful change from a few hearings or legislative reforms will only leave the reformers disappointed to find their efforts have just led to dystopia. So long as there’s money to be made serving the corporate state, that is what corporations will do; there’s no need to resort to conspiracy for it’s right there in their corporate. And that’s not to be defeatist, but to suggest we ought to try a different approach: we ought to be organizing to put a stop to public-private partnerships altogether.
Right-wing libertarians and other defenders of capitalism are absolutely right when they say that the profit motive is a mighty motive indeed — and that’s precisely why we should seek to remove it; to take away even just the prospect of a federal contract. If the demands of privacy advocates are limited by myopic concerns of what’s politically possible here and now, all they will have to show for their advocacy will be a false sense of achievement. The problem isn’t, as some imagine it, a state spying without appropriate limits, but the fact that capitalism erases the distinction between public and private, making it so non-state actors gleefully act as the state’s eyes and ears. This isn’t about just Google or the government, but both: the capitalist state. And until we start recognizing that and saying as much, the result of our efforts will be more of the same.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
quote:De Amerikaanse klokkenluider Edward Snowden is maandag in Stockholm geŰerd met de alternatieve Nobelprijs, de Right Livelihood Award 2014. Snowden, die politiek asiel in Rusland heeft gekregen, was bij de ceremonie niet aanwezig.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


quote:
Het artikel gaat verder.quote:In March 2011, two weeks before the Western intervention in Libya, a secret message was delivered to the National Security Agency. An intelligence unit within the U.S. military’s Africa Command needed help to hack into Libya’s cellphone networks and monitor text messages.
For the NSA, the task was easy. The agency had already obtained technical information about the cellphone carriers’ internal systems by spying on documents sent among company employees, and these details would provide the perfect blueprint to help the military break into the networks.
The NSA’s assistance in the Libya operation, however, was not an isolated case. It was part of a much larger surveillance program—global in its scope and ramifications—targeted not just at hostile countries.
According to documents contained in the archive of material provided to The Intercept by whistleblower Edward Snowden, the NSA has spied on hundreds of companies and organizations internationally, including in countries closely allied to the United States, in an effort to find security weaknesses in cellphone technology that it can exploit for surveillance.
The documents also reveal how the NSA plans to secretly introduce new flaws into communication systems so that they can be tapped into—a controversial tactic that security experts say could be exposing the general population to criminal hackers.
Codenamed AURORAGOLD, the covert operation has monitored the content of messages sent and received by more than 1,200 email accounts associated with major cellphone network operators, intercepting confidential company planning papers that help the NSA hack into phone networks.
One high-profile surveillance target is the GSM Association, an influential U.K.-headquartered trade group that works closely with large U.S.-based firms including Microsoft, Facebook, AT&T, and Cisco, and is currently being funded by the U.S. government to develop privacy-enhancing technologies.
Karsten Nohl, a leading cellphone security expert and cryptographer who was consulted by The Intercept about details contained in the AURORAGOLD documents, said that the broad scope of information swept up in the operation appears aimed at ensuring virtually every cellphone network in the world is NSA accessible.
Free Assange! Hack the Planet
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia
[b]Op dinsdag 6 januari 2009 19:59 schreef Papierversnipperaar het volgende:[/b]
De gevolgen van de argumenten van de anti-rook maffia


 The FBI has reportedly raided the home of a "2nd Snowden". Watch how they treat them for an example of how they would have treated Snowden
The FBI has reportedly raided the home of a "2nd Snowden". Watch how they treat them for an example of how they would have treated Snowden 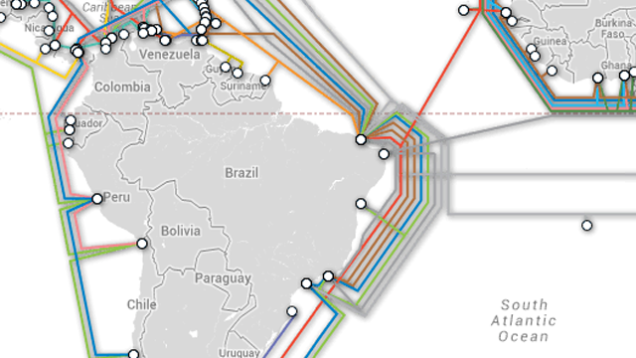

 Q&A with Laura Poitras, Sarah Harrison, Jacob Appelbaum after the Dutch premiere of Citizenfour.
Q&A with Laura Poitras, Sarah Harrison, Jacob Appelbaum after the Dutch premiere of Citizenfour. 
 Wow. Full list of undersea fibre optic cables GCHQ is accessing has been published.
Wow. Full list of undersea fibre optic cables GCHQ is accessing has been published.