W&T Wetenschap & Technologie
Een plek om te discussiëren over wetenschappelijke onderwerpen, wetenschappelijke problemen, technologische projecten en grootse uitvindingen.



Yep.
quote:Marks of Laser Exam on Martian Soil
The Chemistry and Camera (ChemCam) instrument on NASA's Mars rover Curiosity used its laser to examine side-by-side points in a target patch of soil, leaving the marks apparent in this before-and-after comparison.
The two images were taken by ChemCam's Remote Micro-Imager from a distance of about 11.5 feet (3.5 meters). The diameter of the circular field of view is about 3.1 inches (7.9 centimeters).
Researchers used ChemCam to study this soil target, named "Beechey," during the 19th Martian day, or sol, of Curiosity's mission (Aug. 25, 2012). The observation mode, called a five-by-one raster, is a way to investigate chemical variability at short scale on rock or soil targets. For the Beechey study, each point received 50 shots of the instrument's laser. The points on the target were studied in sequence left to right. Each shot delivers more than a million watts of power for about five one-billionths of a second. The energy from the laser excites atoms in the target into a glowing state, and the instrument records the spectra of the resulting glow to identify what chemical elements are present in the target.
The holes seen here have widths of about 0.08 inch to 0.16 inch (2 to 4 millimeters), much larger than the size of the laser spot (0.017 inch or 0.43 millimeter at this distance). This demonstrates the power of the laser to evacuate dust and small unconsolidated grains. A preliminary analysis of the spectra recorded during this raster study show that the first laser shots look alike for each of the five points, but then variability is seen from shot to shot in a given point and from point to point.
ChemCam was developed, built and tested by the U.S. Department of Energy's Los Alamos National Laboratory in partnership with scientists and engineers funded by France's national space agency, Centre National d'Etudes Spatiales (CNES) and research agency, Centre National de la Recherche Scientifique (CNRS).
NASA's Jet Propulsion Laboratory, a division of the California Institute of Technology, Pasadena, manages the Mars Science Laboratory Project, including Curiosity, for NASA's Science Mission Directorate, Washington. JPL designed and built the rover.
Image Credit: NASA/JPL-Caltech/LANL/ CNES/IRAP/LPGN/CNRS


Die Nasa mensen zijn wel flink veranderd... Vroeger superserieuze mannen in pak waar geen glimlach te bespeuren viel; en nu zit de flight director daar in een hawaii t-shirt, en een zeer modern kapsel....quote:


Ik denk dat het ook deels image is  Mensen in witte labjassen spreken het grote publiek niet zo aan
Mensen in witte labjassen spreken het grote publiek niet zo aan 
Opgeblazen gevoel of winderigheid? Zo opgelost met Rennie!


Bobak 
Hij's wel heel erg gay trouwens, zo ruig als een kokosmat

Hij's wel heel erg gay trouwens, zo ruig als een kokosmat
The difference between the three Abrahamic religions:
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.


He's NASA and he knows it 
The difference between the three Abrahamic religions:
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.


Bekijk de video eens,.quote:Op zaterdag 1 september 2012 01:45 schreef Robus het volgende:
Staat daar JPL in morsecode op z'n hoofd?


Zal dat signaal afkomstig van die rover en mars orbiters encrypted zijn? Natuurlijk red je het niet om het signaal af te luisteren met je astra schotel aan je balkon natuurlijk, maar 't zal niet voor het eerst zijn dat de NASA daar iets in is vergeten.


Wil je Curi gaan hacken......
How to Hack NASA's Curiosity Mars Rover
How to Hack NASA's Curiosity Mars Rover
quote:The two biggest tech and science stories of the past week were the brutal hacking of Wired reporter Mat Honan's digital life and the exhilarating arrival of NASA's Curiosity rover on the surface of Mars. So here at PCMag, we decided to combine those two stories into one Google-friendly gob of geeky goodness.
That's right, folks, we're going to tell you how to hack the Mars rover.
First, a disclaimer: We don't recommend anybody actually try this. Let science do its thing, people! Nor do we believe we're giving anybody a bright idea just by performing this technical exercise. As we found out after talking to several hackers, crackers, and security pros, the resources required to pull this off are prohibitive—the folks with the actual resources required to compromise Curiosity (*cough* China *cough*) don't need our cobbled-together advice on how to do it.
In other words, a state-backed actor could maybe take over NASA's planetary crawler, but the script kiddies are pretty much SOL here. We are exceedingly unlikely to see "We Are Legion" transmitted by Curiosity as its last act before driving off a cliff while IRC explodes with lulz.
With that said, let's hack the rover!
The Hard Way
The first thing we learned is that hacking Curiosity itself across 352 million miles of interplanetary vacuum is almost certainly the wrong approach to this task. Much better to try to sneak into NASA's own control systems here on Earth, which AlienVault research team engineer Conrad Constantine described as "the weakest, most inexpensive link in all of this."
More on that later. For funsies, here's what Constantine had to say about the hurdles you'd have to overcome to start pinging Curiosity with diabolical contra-NASA instructions:
You would have to be able to transmit an X-Band radio signal at peak 400 kilowatts to reach the Mars rover. Considering you need something that can do 400,000 watts to even have a fighting chance of overriding NASA's own control signal and you can begin to see that it's a pretty serious cost-of-entry to play in this game."
It is probably N-WAY QPSK encoding and you'd have to match that (this is similar to the encoding they use for satellite TV). Difficult, but not impossible. All this stuff would take a good amount of time and observation. Plus you'd want to capture NASA's own transmissions to the rover. That could be tough—they're pretty damn directional."
There's a massive amount of forward-error correction going on as well—remember that Curiosity is receiving queued-up commands from NASA's orbital transponders over low-bandwidth X-BAND uhf (8ghz). This gets into similar territory as TCP/IP spoofing, where you have to predict what the rover is expecting next. Unless you could intercept the directional transmission from the orbital transponders, you're just guessing what state the communications are in.
One hint at just how tough it might be to penetrate the rover's security barriers came by way of a brief story on Space.com earlier this year detailing how the Curiosity team remotely fixed a register glitch in the rover's memory cache, noted Dmitri Alperovitch, co-founder and CTO of CrowdStrike.
"They are updating the software on the rover all the time," said Alperovitch. What's more, these aren't just automated updates like the kind your PC gets on Patch Tuesdays. You have to believe the Curiosity team at NASA's Jet Propulsion Lab (JPL) has a pretty intimate relationship with the rover's systems, making it very tough to sneak a malicious payload by the many engineers who are currently checking up on their baby more obsessively than a D-list celebrity refreshes his Twitter feed.
Sorry, Anons, but the JPL gang probably eats clumsy SQL injections for breakfast.
The Slightly Less Hard Way
So if not a direct assault on NASA's core software, what next? F-Secure security advisor Sean Sullivan suggested an alternative.
"I'm afraid that I don't know enough about the actual code and systems used to come up with much, but for a 'far out' scenario in which money is not an object, I'd backdoor some of the [third-party] technology on board," he said.
Sullivan pointed to pressure and humidity sensors on Curiosity supplied by the Finnish Meteorological Institute. "Perhaps not all is as it seems" with those possible poison pills, he noted archly, shocking us for a moment before we recalled that F-Secure is headquartered in Helsinki and laughed at the inside joke.
In fact, it seems unlikely that NASA's vetting of tech supplied by mission partners like the Finns would have allowed a backdoor access point onto the rover. What's a lot more troubling, to paraphrase Donald Rumsfeld, are the unknown knowns about what makes Curiosity tick that may be out there.
Earlier this year, NASA Inspector General Paul Martin briefed Congress on the "the loss or theft of 48 Agency mobile computing devices" between April 2009 and April 2011 and "5,408 computer security incidents [in 2010 and 2011] that resulted in the installation of malicious software on or unauthorized access to [NASA] systems."
Yikes? The loss of sensitive data on Curiosity wasn't specifically mentioned in Martin's report, which identified "ISS command algorithms" and data related to NASA's Orion deep space capsule as among the losses to unknown actors in recent years, but still—yikes.
The Scarily Possible Way
As mentioned, a brute force takeover of Curiosity isn't as attractive a prospect as trying to infiltrate the Earthside signaling operation.
"Really though, the only viable way to do this on a budget would be to take control of NASA's own control systems. That's the weakest, most inexpensive link in all of this and NASA has the only existing, viable communications setup to the Rover. You'd have to get control of that, without them noticing," said AlienVault's Constantine.
"What you have here is a very moist attack surface, it's saturated with existing comms that you would have to intercept, predict and hijack. Going after the existing control system is likely the most porous point of attack."
CrowdStrike's Alperovitch concurred, but wondered if "the most sophisticated actors capable of this would have the motive" to try to hijack a scientific mission that basically stands to benefit all humankind. That didn't stop him from playing the guessing game, of course.
"Imagine if hackers were able to get access to the systems operating NASA's Deep Space Network—the one that is responsible for radio communications with the rover and other interplanetary objects. Then you would be able to send instructions to the rover and even destroy it by driving it into a rock, for example. Theoretically, you could also upgrade its firmware to no longer accept instructions from NASA so that you would be the sole operator," he mused.
Farfetched? Not as much as you might think.
Several sources pointed to reports that U.S. government satellites were compromised at least four times in 2007 and 2008, possibly at the hands of Chinese computer hackers with ties to the country's military, as well as allegations by Russian space agency officials that cyber-skullduggery was responsible for the failure of the Phobos-Grunt probe last year, as evidence that this sort of thing is well within the realm of possibility.
All that said, maybe the bluntest way to compromise Curiosity would be to plant a mole in JPL itself. And all we can say to that scenario is, stay vigilant, Mohawk Guy!
PCMag's Meredith Popolo was at the Jet Propulsion Lab in California last week covering the Curiosity rover's arrival on Mars. For more, see the slideshow below, which details her tour of JPL. Also check out 7 Minutes of Terror: Landing the Mars Curiosity Rover and What Powers the Mars Curiosity Rover?
For more from Damon, follow him on Twitter @dpoeter.
<a href="http://www.vwkweb.nl/" rel="nofollow" target="_blank">[b]Vereniging voor weerkunde en klimatologie[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>


Beetje onverantwoord om zo'n artikel te schrijven. Natuurlijk dat niet iemand dit zo gauw doet, maar soms heb je van die vervelende gekken tussen zitten, die hier voldoende aanknopingspunten in vinden om uit te werken.
Stel je voor dat het ze ook nog eens lukt om de BIOS/POST Mac-hardware op Curiosity lam te leggen. Zeg dan maar dag tegen je 2,5 miljard kostende autootje op Mars.
Stel je voor dat het ze ook nog eens lukt om de BIOS/POST Mac-hardware op Curiosity lam te leggen. Zeg dan maar dag tegen je 2,5 miljard kostende autootje op Mars.


mowah, de gekken die daadwerkelijk de intentie, kennis, financien en apparatuur hebben om dit te doen, hebben een artikel zoals deze niet nodigquote:Op zondag 2 september 2012 03:40 schreef KeimpeHart het volgende:
Beetje onverantwoord om zo'n artikel te schrijven. Natuurlijk dat niet iemand dit zo gauw doet, maar soms heb je van die vervelende gekken tussen zitten, die hier voldoende aanknopingspunten in vinden om uit te werken.
Stel je voor dat het ze ook nog eens lukt om de BIOS/POST Mac-hardware op Curiosity lam te leggen. Zeg dan maar dag tegen je 2,5 miljard kostende autootje op Mars.
Totaal Travel 04-24: 87 reizen, 151 vliegtickets, 58 landen, 6 continenten, 949 reisdagen, 163.804 foto's
Mijn reisfotos!
Mijn reisfotos!


Ik dacht dat dat ding de Explorer heette.. zo noem ik hem tenminste de hele tijd als ik over de ruimte praat met mensen


laten we dat maar niet doenquote:Op zondag 2 september 2012 10:17 schreef Acit het volgende:
Ik dacht dat dat ding de Explorer heette.. zo noem ik hem tenminste de hele tijd als ik over de ruimte praat met mensen
niet raar opkijken als iets explorer noemt en dan vervolgens crasht. Naam van dit schip was MS Explorer...
Totaal Travel 04-24: 87 reizen, 151 vliegtickets, 58 landen, 6 continenten, 949 reisdagen, 163.804 foto's
Mijn reisfotos!
Mijn reisfotos!


Ik moest lachenquote:Op zondag 2 september 2012 10:42 schreef ETA het volgende:
[..]
laten we dat maar niet doen
[ afbeelding ]
niet raar opkijken als iets explorer noemt en dan vervolgens crasht. Naam van dit schip was MS Explorer...
[i] When you try your best but you don't succeed. When you get what you want but not what you need. [/i]


Mooierdquote:Op zaterdag 8 september 2012 16:59 schreef Tauchmeister het volgende:
[ afbeelding ]
Foto van zichzelf
[i] When you try your best but you don't succeed. When you get what you want but not what you need. [/i]


SMILE...... Youre on candid cameraquote:Op zaterdag 8 september 2012 16:59 schreef Tauchmeister het volgende:
[ afbeelding ]
Foto van zichzelf
<a href="http://www.vwkweb.nl/" rel="nofollow" target="_blank">[b]Vereniging voor weerkunde en klimatologie[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>


Jup, duidelijk familie van Wall-e.quote:Op zaterdag 8 september 2012 16:59 schreef Tauchmeister het volgende:
[ afbeelding ]
Foto van zichzelf
Opgeblazen gevoel of winderigheid? Zo opgelost met Rennie!


Eerder Jonnhy 5quote:Op zondag 9 september 2012 00:37 schreef Eyjafjallajoekull het volgende:
[..]
Jup, duidelijk familie van Wall-e.
<a href="http://www.vwkweb.nl/" rel="nofollow" target="_blank">[b]Vereniging voor weerkunde en klimatologie[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>
<a href="http://www.estofex.org/" rel="nofollow" target="_blank">[b]ESTOFEX[/b]</a>


Nee, het is de achterneef van Wall-e. Niet tegen um zeggen, maar hij is een beetje 'speciaal'. Ongelukje na een overdosis elektromagnetische straling.quote:Op zondag 9 september 2012 01:17 schreef -CRASH- het volgende:
[..]
Eerder Jonnhy 5
[ afbeelding ]
[ afbeelding ]
Opgeblazen gevoel of winderigheid? Zo opgelost met Rennie!


Beetje creepy foto dit
The difference between the three Abrahamic religions:
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.


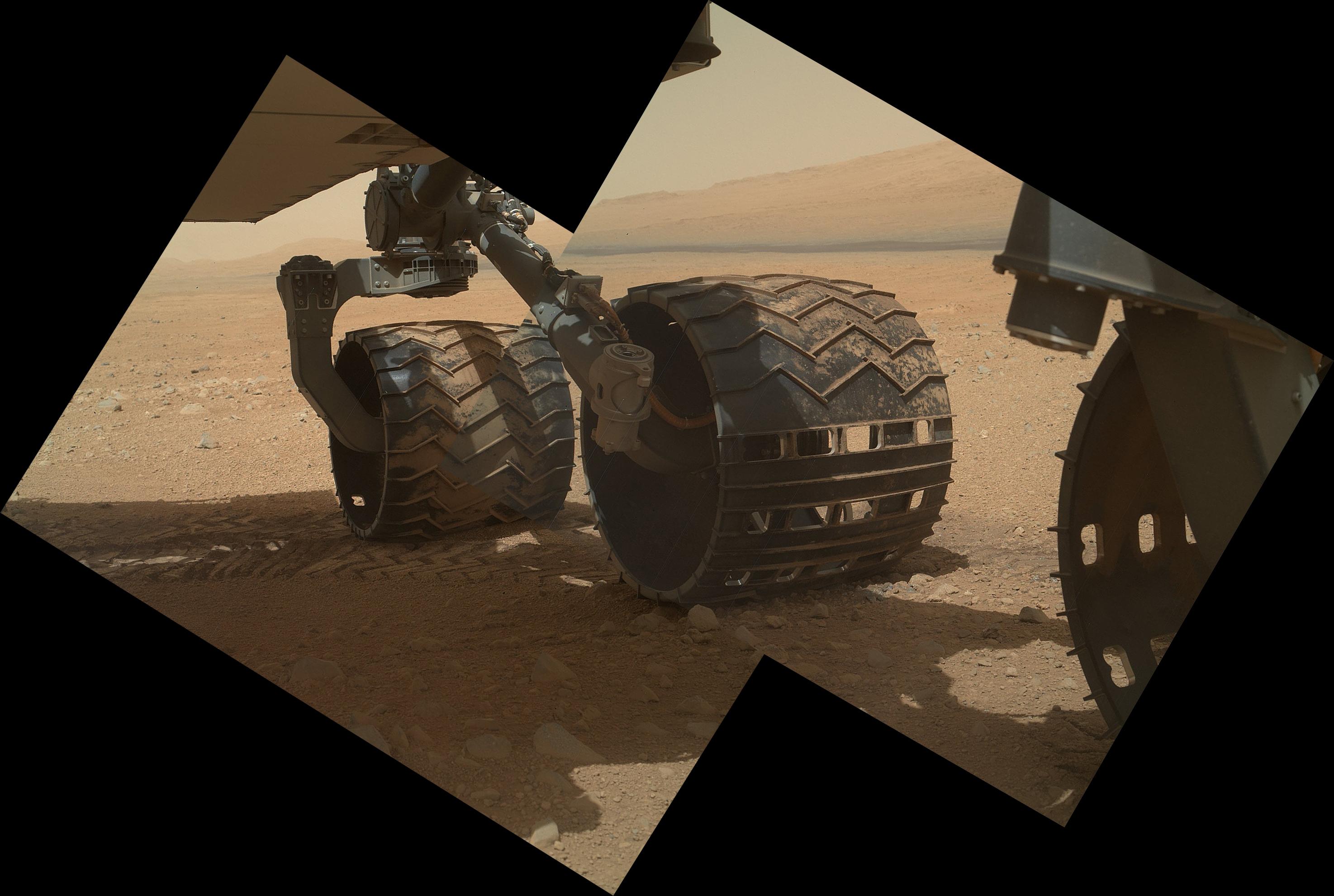
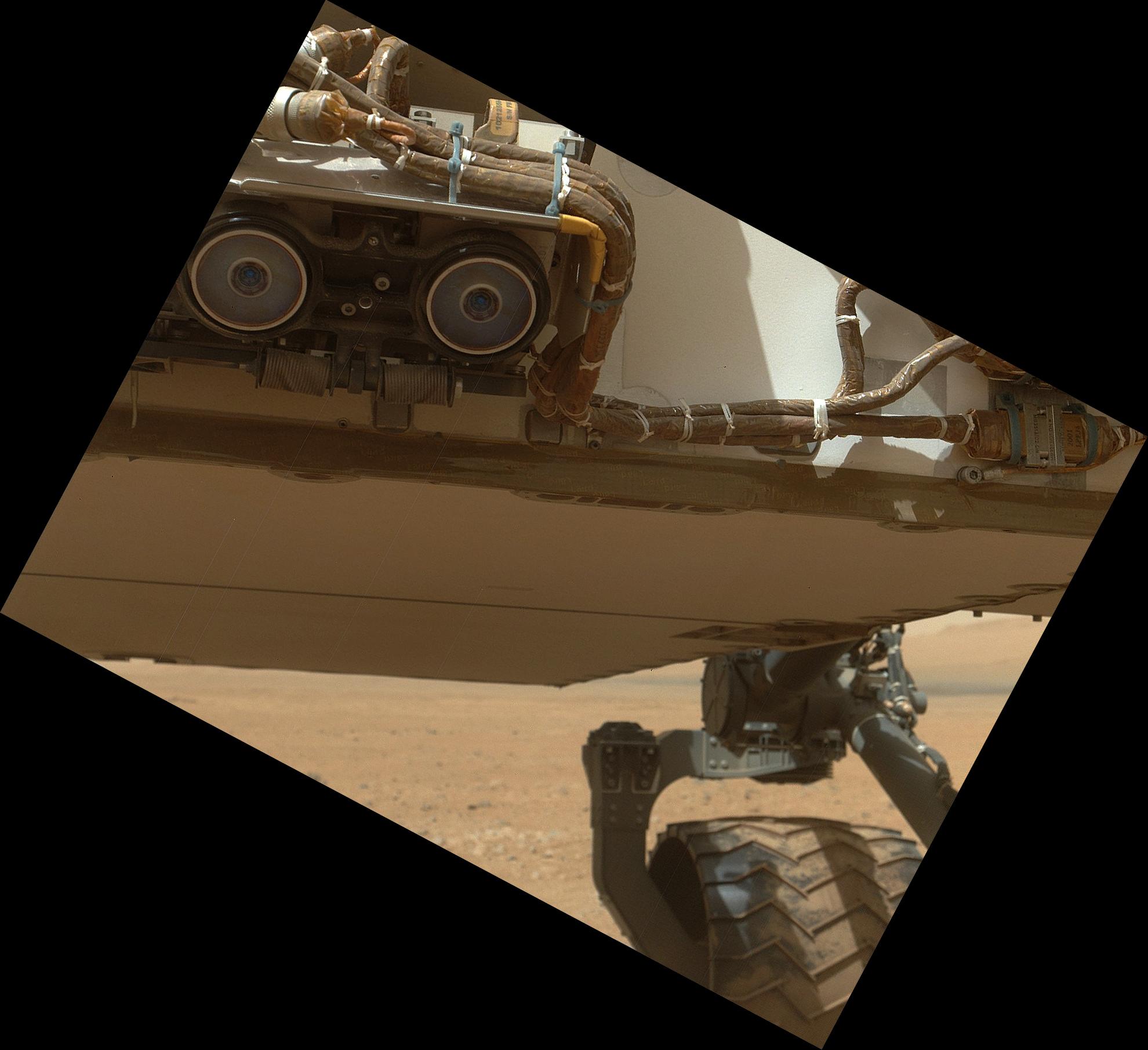
Eerste foto met open stofkap.
De steen onderaan is zo'n 8 cm.
[ Bericht 7% gewijzigd door Robus op 09-09-2012 18:57:17 ]
De steen onderaan is zo'n 8 cm.
[ Bericht 7% gewijzigd door Robus op 09-09-2012 18:57:17 ]


Lekker scherp beeld!  Het gaat om die camera op de arm, neem ik aan?
Het gaat om die camera op de arm, neem ik aan?
The difference between the three Abrahamic religions:
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.


Scherp genoeg om ergens een jezus in te kunnen zien 
Exponentiële deflatie van Bitcoin maakt arme mensen nog veel sneller armer dan het grote probleem van inflatie. Gematigde burning van Ethereum is de gulden middenweg.


Een wat? 
The difference between the three Abrahamic religions:
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.
- Christianity mumbling to the ceiling,
- Judaism mumbling to the wall,
- Islam mumbling to the floor.


Ik had een kleinere foto geplaatst zag ik. Heb nu de full-size erin gezet en is inderdaad gemaakt met de camera op de arm 


OH HAI
Op dinsdag 23 augustus 2011 23:18 schreef problematiQue het volgende:
Mensen die zomaar claimen dat A beter is dan B moet je gewoon negeren. Internetruis.
Mensen die zomaar claimen dat A beter is dan B moet je gewoon negeren. Internetruis.